The “unpatchable” exploit that makes every current Nintendo Switch hackable [Updated]
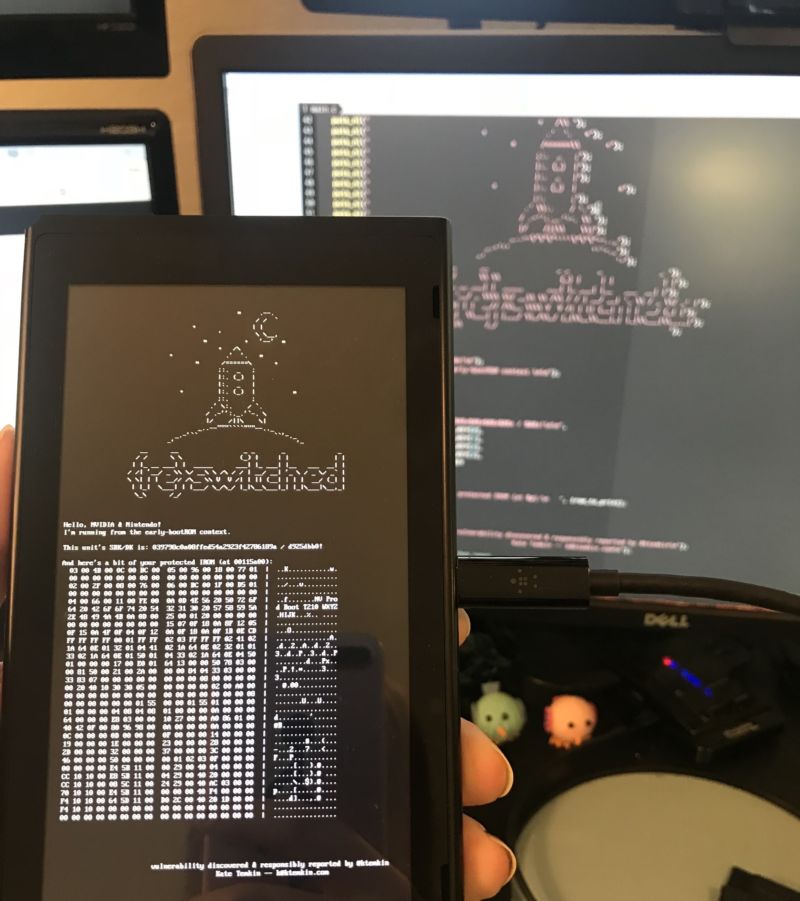
Enlarge / The "proof of concept" payload for today's exploit shows crucial protected information from the now-exposed Nintendo Switch bootROM. (credit: Kate Temkin / ReSwitched)
A newly published "exploit chain" for Nvidia Tegra X1-based systems seems to describe an apparently unpatchable method for running arbitrary code on all currently available Nintendo Switch consoles. Hardware hacker Katherine Temkin and the hacking team at ReSwitched released an extensive outline of what they're calling the Fusi(C)e Geli(C)e coldboot vulnerability earlier today, alongside a proof-of-concept payload that can be used on the Switch.
"Fusi(C)e Geli(C)e isn't a perfect, 'holy grail' exploit-though in some cases it can be pretty damned close," Temkin writes in an accompanying FAQ.
The exploit, as outlined, makes use of a vulnerability inherent in the Tegra X1's USB recovery mode, circumventing the lock-out operations that would usually protect the chip's crucial bootROM. By sending a bad "length" argument to an improperly coded USB control procedure at the right point, the user can force the system to "request up to 65,535 bytes per control request." That data easily overflows a crucial direct memory access (DMA) buffer in the bootROM, in turn allowing data to be copied into the protected application stack and giving the attacker the ability to run arbitrary code.
Read 14 remaining paragraphs | Comments