Hackers can eavesdrop on mobile calls with $7,000 worth of equipment
Enlarge (credit: Rupprecht et al.)
The emergence of mobile voice calls over the standard known as Long Term Evolution has been a boon for millions of cell phone users around the world. VoLTE, short for Voice over LTE, provides up to three times the capacity of the earlier 3G standard, resulting in high-definition sound quality that's a huge improvement over earlier generations. VoLTE also uses the same IP standard used to send data over the Internet, so it has the ability to work with a wider range of devices. VoLTE does all of this while also providing a layer of security not available in predecessor cellular technologies.
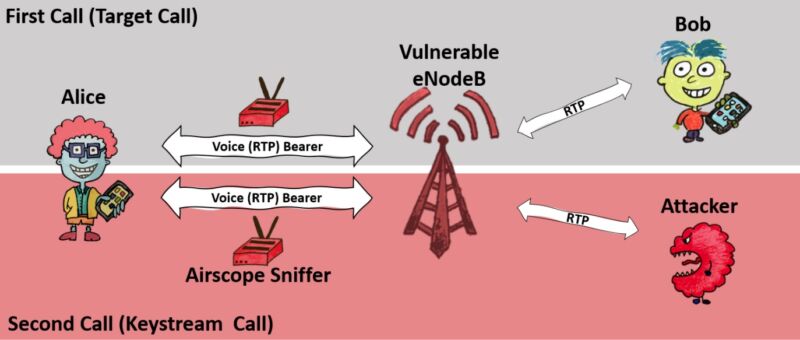
Now, researchers have demonstrated a weakness that allows attackers with modest resources to eavesdrop on calls. Their technique, dubbed ReVoLTE, uses a software-defined radio to pull the signal a carrier's base station transmits to a phone of an attacker's choosing, as long as the attacker is connected to the same cell tower (typically, within a few hundred meters to few kilometers) and knows the phone number. Because of an error in the way many carriers implement VoLTE, the attack converts cryptographically scrambled data into unencrypted sound. The result is a threat to the privacy of a growing segment of cell phone users. The cost: about $7,000.
So much for more secureData confidentiality is one of the central LTE security aims and a fundamental requirement for trust in our communication infrastructure," the researchers, from Ruhr University Bochum and New York University, wrote in a paper presented Wednesday at the 29th USENIX Security Symposium. We introduced the ReVoLTE attack, which enables an adversary to eavesdrop and recover encrypted VoLTE calls based on an implementation flaw of the LTE protocol."
Read 21 remaining paragraphs | Comments