For almost 11 years, hackers could easily bypass 3rd-party macOS signature checks
Enlarge / The Little Snitch firewall was one of at least eight third-party Mac security tools affected by a code-signing bypass. (credit: Okta)
For almost 11 years, hackers have had an easy way to get macOS malware past the scrutiny of a host of third-party security tools by tricking them into believing the malicious wares were signed by Apple, researchers said Tuesday.
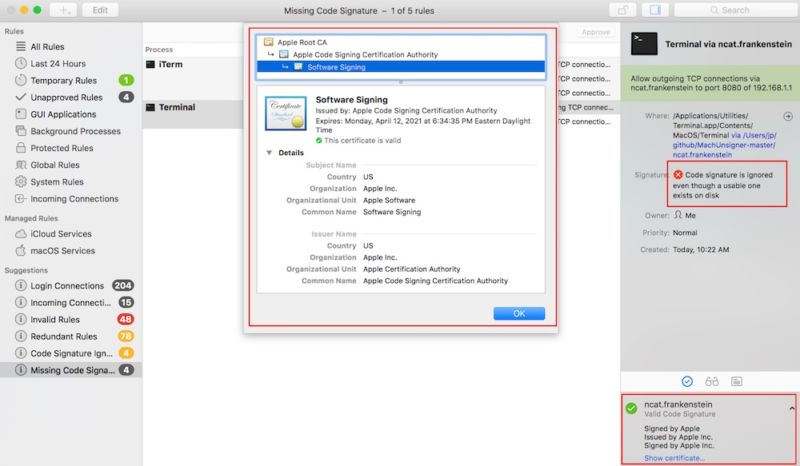
Digital signatures are a core security function for all modern operating systems. The cryptographically generated signatures make it possible for users to know with complete certainty that an app was digitally signed with the private key of a trusted party. But, according to the researchers, the mechanism many macOS security tools have used since 2007 to check digital signatures has been trivial to bypass. As a result, it has been possible for anyone to pass off malicious code as an app that was signed with the key Apple uses to sign its apps.
The technique worked using a binary format, alternatively known as a Fat or Universal file, that contained several files that were written for different CPUs used in Macs over the years, such as i386, x86_64, or PPC. Only the first so-called Mach-O file in the bundle had to be signed by Apple. At least eight third-party tools would show other non-signed executable code included in the same bundle as being signed by Apple, too. Affected third-party tools included VirusTotal, Google Santa, Facebook OSQuery, the Little Snitch Firewall, Yelp, OSXCollector, Carbon Black's db Response, and several tools from Objective-See. Many companies and individuals rely on some of the tools to help implement whitelisting processes that permit only approved applications to be installed on a computer, while forbidding all others.
Read 6 remaining paragraphs | Comments