Critical Windows 10 vulnerability used to Rickroll the NSA and Github
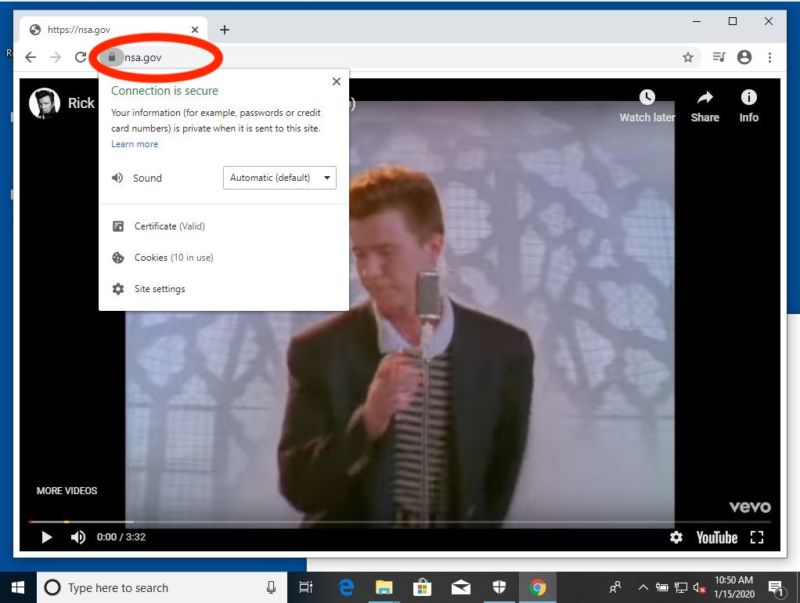
Enlarge / Chrome on Windows 10 as it Rickrolls the NSA. (credit: https://twitter.com/saleemrash1d/status/1217519809732259840/photo/1)
Less than a day after Microsoft disclosed one of the most critical Windows vulnerabilities ever, a security researcher has demonstrated how attackers can exploit it to cryptographically impersonate any website or server on the Internet.
Researcher Saleem Rashid on Wednesday tweeted images of the video "Never Gonna Give You Up," by 1980s heart-throb Rick Astley, playing on Github.com and NSA.gov. The digital sleight of hand is known as Rickrolling and is often used as a humorous and benign way to demonstrate serious security flaws. In this case, Rashid's exploit causes both the Edge and Chrome browsers to spoof the HTTPS verified websites of Github and the National Security Agency. Brave and other Chrome derivatives, as well as Internet Explorer, are also likely to fall to the same trick. (There's no indication Firefox is affected.)
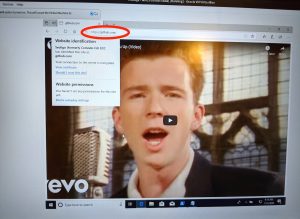
The same exploit used to Rickroll Github on Edge.
Rashid's simulated attack exploits CVE-2020-0601, the critical vulnerability that Microsoft patched on Tuesday after receiving a private tipoff from the NSA. As Ars reported, the flaw can completely break certificate validation for websites, software updates, VPNs, and other security-critical computer uses. It affects Windows 10 systems, including server versions Windows Server 2016 and Windows Server 2019. Other versions of Windows are unaffected.
Read 17 remaining paragraphs | Comments