Don’t count on STARTTLS to automatically encrypt your sensitive e-mails
(credit: Yzmo)
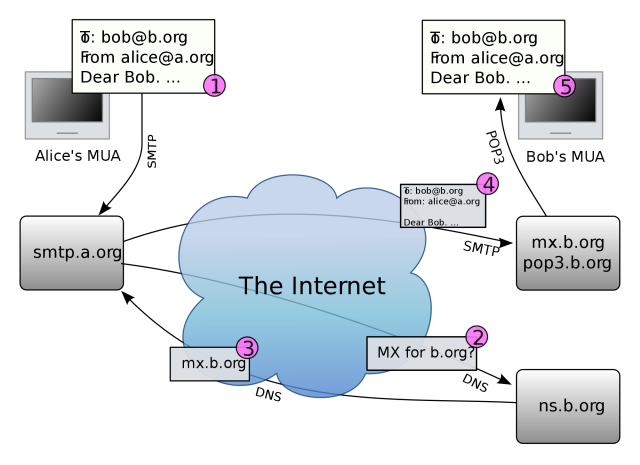
Researchers have some good and bad news about the availability of secure e-mail. Use of STARTTLS and three other security extensions has surged in recent months, but their failure rate remains high, in large part because of active attacks that downgrade encrypted connections to unencrypted ones.
That conclusion, reached in a recently published research paper, means that a significant chunk of e-mail continues to be transmitted in plaintext and with no mechanism for verifying that a message hasn't been tampered with while it travels from sender to receiver. The downgrades are largely made possible by the simple mail transfer protocol used by many e-mail services. Because it wasn't originally designed to provide message confidentiality or integrity, it relies on later-developed extensions including STARTTLS, domainkeys Identified Mail, sender policy framework, and domain-based message authentication that often don't work as intended.
The researchers wrote:
Read 6 remaining paragraphs | Comments