
Germany's Angela Merkel isn't the only one riled over recent revelations of American surveillance and data gathering. Turns out
The American government conducted a major intelligence offensive against China , with targets including the Chinese government and networking company Huawei.
Edward Snowden is the source of the revelations, as reported to German daily Spiegel. Among the American intelligence service's targets were former Chinese President Hu Jintao, the Chinese Trade Ministry, banks, as well as telecommunications companies. But the NSA made a special effort to target Huawei.
According to a top secret NSA presentation, NSA workers not only succeeded in accessing the email archive, but also the secret source code of individual Huwaei products."
There's more than one way to compute a secure hash, from MD5 to SHA-3 to SHA-1 and beyond. So who cares about yet another: Blake2?
There are a couple of reasons you might be interested in checking out Blake2: It was rated best hash function in the SHA-3 competition, is faster than MD5, and cryptographers find that it's similar to the well-regarded SHA-2 algorithm in ways that matter.
Says developer Zooko Wilcox-O'Hearn:
Jean-Philippe Aumasson, Samuel Neves, Christian Winnerlein, and I decided that what the world needed was not just a secure hash function that was faster than Keccak, but one that was faster than MD5! This is because MD5 (and SHA-1) continue to be very widely used, even in new applications, even though MD5 and SHA-1 are unsafe for many uses. We hypothesized that offering engineers a hash function that was both faster and more secure than their beloved MD5 or SHA-1 might be more effective than haranguing them to upgrade to an alternative that is more secure but slower.
Have a look for yourself at Wilcox-O'Hearn's page.
Ottawa bitcoin exchange
Canadian Bitcoins was subject to a heist that led to $100,000 worth of bitcoins being stolen. But it was no complicated, security fraud: it was simple, social engineering.
The Ottawa Citizen reports: The Ottawa police are investigating an Oct. 1, 2013, incident at Canadian Bitcoins, when someone opened an online chat session with a technical support worker at Granite Networks, now owned by Rogers Communications, and claimed to be Canadian Bitcoins owner James Grant. He claimed to have a problem with a server and asked the attendant to reboot it into recovery mode, allowing him to bypass security on the server. "It's ridiculous," said the real James Grant when asked about the incident. "There was absolutely zero verification of who it actually was."
The most frustrating details relate to the high degree of physical security that the real owner was subjected to when attempting to access his server cage - something the thieves didn't face.
Canadian Bitcoins' statement on the matter is here.Here's an unpleasant start to your morning: confirmation of a
long-running openSSH exploit [PDF] that has led to an extensive botnet pumping out spam, viruses, malware, and of course links to redirect farms.
Symantec provides some analysis here . "Operation Windigo" as it's called has been alive since 2011, stealing SSH credentials on Windows, Linux, and BSD systems, and it has hit a couple of well-known companies, including cpanel and the Linux Foundation.
Check your system in the time it takes for your morning coffee to cool, with this command to see if you've been affected:
ssh -G 2>&1 | grep -e illegal -e unknown >/dev/null && echo "System clean" || echo "System infected"
Uninfected systems return an "error illegal option" or "unknown option" for the -G flag, plus as the usage message, whereas infected systems will return only the usage message.
If your system doesn't come up clean, you are probably one of an estimated 25,000 compromised servers currently sending out over 35 million pieces of spam.

The US FBI has been working with the FAA and the Air Line Pilots Association
to crack down on people pointing lasers at aircraft. "Reported incidents of laser attacks on aircraft in flight in the US have increased more than 1,000 percent since 2005, according to the FAA, from 283 up to 3,960 in 2013 - an average of 11 incidents a day."
Per the Air Line Pilots Association, "
reports of aircraft laser illuminations in the U.S. have increased sharply over the past few years from 2836 in 2010 to 3,960 last year."
Sergio Patrick Rodriguez, 26,
now has the dubious distinction of being sentenced to "14 years in federal prison, a term prosecutors believe to be among [California's] longest for such a crime." Rodriguez's gang membership and criminal record were likely factors in his sentence, as was
using a laser that is called 13 times more powerful than most laser pointers. Has anyone seen this happen? Or experienced it as a pilot or aircraft passenger?

Late last year, US retailer
Target had multiple IT failures that led to 40 million credit cards being leaked. Target lost more than $61 million in breach-related expenditures and incurred a significant decrease to holiday sales.
Businessweek has a lengthy article laying out the failures, among them:
- Despite installing FireEye's monitoring technology, security administrators disabled FireEye's option to automatically delete malware as it is detected, allowing the unclassified 'malware.binary' through.
- When Target India's team received the first critical alert from FireEye, they notified the security team at Target's Headquarters in Minneapolis Minnesota, USA, but the report was ignored or simply no action was taken on it.
- Additional critical alerts were generated, but apparently no action was taken on them.
- Symantec Endpoint Protection detected odd behavior on the same server as detected by FireEye, but this did not raise concern.
- The initial illicit access was gained by an outside vendor's stolen credentials, which should not have given as much network access as it did.
Although the data was copied through a few hops in the US, the destination was ultimately traced to Russia. Analysis of the binaries shows that the malware itself was unsophisticated and included a possible hacker's alias in the 'exfiltration code'.

From
www.extremetech.com: This is almost incomprehensible: Despite all of the awesome technology that mankind has developed, it's still possible for a Boeing 777-200 with 239 people on board to vanish. It's mind blowing that all we have to go on is the plane's "radar signature" and even then, that last radar reading was so poor that the search area is thousands of square miles of open water. Surely, given the fact that we can track a smartphone anywhere on Earth down to a few meters, there's a better way of keeping track of missing aircraft?
With recent wifi enabled aircraft and scads of modern incoming and outgoing signals, surely they cannot claim that some of the more legacy technology is to blame -- especially in the newest plane on the market? An EPIRB is pretty much mandatory for sea-faring craft and will signal the nearest SAR: why isn't there an equivalent on aircraft?
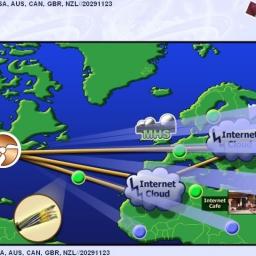
New Snowden related documents and an
article by Glenn Greenwald reveal National Security Agency programs for hacking and infecting computers on a mass scale using automated systems. The attacks are not just targeted against suspects or "persons of interest", but also against third-parties people who maintain network and computing infrastructure.
By hacking an administrator's computer, the agency can gain covert access to communications that are processed by his company. Sys admins are a means to an end,
the NSA operative writes.
The implants being deployed were once reserved for a few hundred hard-to-reach targets, whose communications could not be monitored through traditional wiretaps. But the documents analyzed by The Intercept show how the NSA has aggressively accelerated its hacking initiatives in the past decade by computerizing some processes previously handled by humans. The automated system - codenamed TURBINE - is designed to allow the current implant network to scale to large size (millions of implants) by creating a system that does automated control implants by groups instead of individually.

Burgess Everett and Manu Raju report at Politico that Senator Dianne Feinstein set off a political firestorm when she took to the Senate floor to
accuse CIA officials of potentially violating the Constitution in conducting an unauthorized search of her committee's computers to turn up documents related to a congressional investigation into
Bush-era detention and interrogation programs. Feinstein, who spoke to President Barack Obama about her concerns, said her panel will vote to declassify the report into the interrogation practices sometime this month, something that could embarrass the intelligence community. "We're not going to stop," says Feinstein. "If the Senate can declassify this report, we will be able to ensure that an un-American, brutal program of detention and interrogation will never again be considered or permitted."
CIA Director John Brennan forcefully pushed back against Feinstein's allegations, prompting senators to begin calling for a larger investigation into the matter. John McCain called the situation "very disturbing."
"Heads will roll," Graham said if an investigation confirms Feinstein's allegations. "If what they're saying is true about the CIA, this is Richard Nixon stuff. This is dangerous to a democracy, heads should roll, people should go to jail, if it's true," Graham said. "The legislative branch should declare war on the CIA - if it's true."
Is Senator Feinstein's outrage justified, or is she a
a hypocrite as Snowden charges?
In these paranoid post-NSA times, you'd be forgiven for worrying about the security of your communications. Are your private conversations on Twitter, Facebook or Skype really private, or are they being stored on some shadowy organisations' servers in perpituity? Is something you thought was said in confidence going to come back to haunt you at some unknown time in the future? A lot of developers are asking themselves these kinds of questions, and we're starting to see the emergence of decentralized messaging systems. Here are a couple of these projects which look promising. Although still under active development, they both have clients available which are usable
right now by adventurous alpha testers:
- Project Tox is a FOSS (Free and Open Source Software) instant messaging application aimed to replace Skype. It aims to be an easy to use, all-in-one communication platform (including audio, and videochats in the future) that ensures their users full privacy and secure message delivery. Outlines of the DHT and Lossless UDP protocols used, and a recent post on reddit has more information, and details of different client apps available.
- twister is built on Bitcoin and BitTorrent protocols to deliver a peer-to-peer microblogging system, a secure decentralized alternative to Twitter. The download page has links to source code and Win32 binaries and an installable Android package is available for users who have 'Unknown sources' enabled.
- And while it's not a messing system per se , I2P may also be of interest as an 'anonymous overlay network' which also provides access to secure blogging and email among other features and is available on many platforms .
One thing to bear in mind -- communication software is only as useful as the people using it, so if you want to talk to your friends with either of these, now's the time to start convincing them to adopt...
 Germany's Angela Merkel isn't the only one riled over recent revelations of American surveillance and data gathering. Turns out The American government conducted a major intelligence offensive against China , with targets including the Chinese government and networking company Huawei.
Germany's Angela Merkel isn't the only one riled over recent revelations of American surveillance and data gathering. Turns out The American government conducted a major intelligence offensive against China , with targets including the Chinese government and networking company Huawei.





