E-commerce site is infected not by one, but two card skimmers

Enlarge (credit: Mighty Travels)
Payment card skimming that steals consumers' personal information from e-commerce sites has become a booming industry over the past six months, with high-profile attacks against Ticketmaster, British Airways, Newegg, and Alex Jones' InfoWars, to name just a few. In a sign of the times, security researcher Ji(C)rime Segura found two competing groups going head to head with each other for control of a single vulnerable site.
The site belongs to sportswear seller Umbro Brasil, which as of Tuesday morning was infected by two rival skimmer groups. The first gang planted plaintext JavaScript on the site that caused it to send payment card information to the attackers as customers were completing a sale. The malicious JavaScript looked like this:
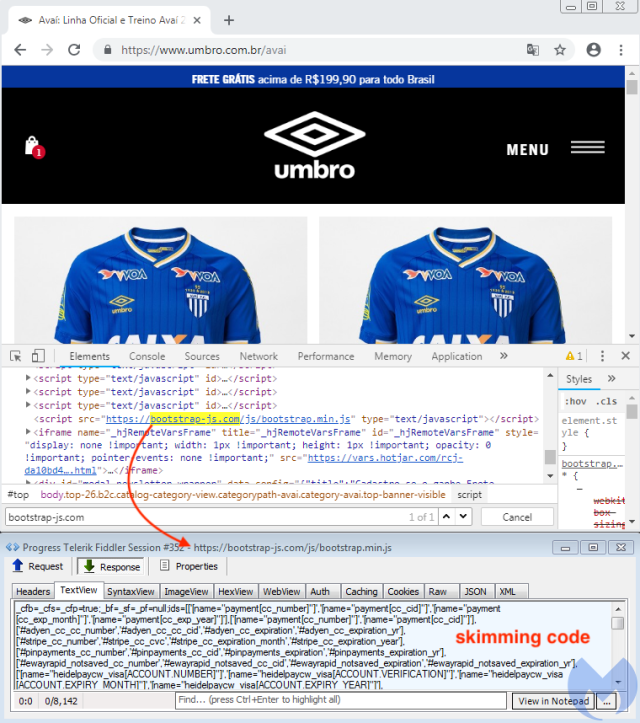
The first skimmer using unobfuscated JavaScript.
A second gang exploited either the same or a different website vulnerability as the first. The second group then installed much more advanced JavaScript that was encoded in a way to prevent other programs from seeing what it did. This is what it looked like:
Read 8 remaining paragraphs | Comments