 |
by Felix Salmon on (#3WS41)
With nimble startups like Netflix and NewTV, the death of television seems imminent. But the old-fashioned medium is powerful, lucrative, and just might be too big to fail.
|
| Link | http://feeds.wired.com/ |
| Feed | http://feeds.wired.com/wired/index |
| Updated | 2026-01-19 09:47 |
 |
by Klint Finley on (#3WR4Z)
In new rankings from analyst firm RedMonk, Apple’s programming language Swift and Android favorite Kotlin saw their meteoric growth slightly slow down.
|
 |
by Tom Philpott on (#3WQXQ)
And cooking it to kingdom come won't necessarily protect you.
|
 |
by Emily Dreyfuss on (#3WQSF)
A new report shows that Google still tracks your location even if you thought you opted out.
|
 |
by Joe Ray on (#3WQ50)
GE loaded this microwave with Alexa capabilities and scan-to-cook technology. But those high-tech features make microwaving more complicated than ever.
|
 |
by Rhett Allain on (#3WQ4Y)
Really, this is a classic projectile motion physics problem.
|
 |
by Graeme McMillan on (#3WQ52)
The Mouse House reportedly wants all of them for its streaming service.
|
 |
by Angela Watercutter on (#3WPZ8)
Feeling the need to tack a reaction on everything you see is stressful. But you don't have to do it.
|
 |
by Matt Simon on (#3WPZ6)
Thanks in part to groundwork laid by the animators of Disney’s “Frozen,†this simulation may help develop better avalanche warning systems.
|
 |
by Andy Greenberg on (#3WPZ4)
A new study found that just 42,000 of those hacked home devices could be enough to leave a country of 38 million people in the dark.
|
 |
by Lily Hay Newman on (#3WP8H)
Researchers have demonstrated that sending a single malicious fax is all it takes to break into a network.
|
 |
by Louise Matsakis on (#3WP5Z)
A preliminary study shows that hackers penetrate systems in unique, documentable ways—just like criminals in the physical world.
|
 |
by Brian Barrett on (#3WP3G)
The so-called man in the disk attack uses Android's permissive external storage to wreak havoc on devices.
|
 |
by Andy Greenberg on (#3WP12)
Researchers found they could turn the smart speakers into surveillance devices—if they could get their own attack tool on the same Wi-Fi.
|
 |
by Andy Greenberg on (#3WNWG)
A former NSA hacker finds a new way malware can take control of a Mac's mouse for a powerful intrusion technique.
|
 |
by Laura Mallonee on (#3WNNQ)
The country is home to a $1 billion tech scene.
|
 |
by Aarian Marshall on (#3WNK1)
Plus, we chat with Kodiak Robotics, a new autonomous trucking startup, and Steve McQueen’s Ford Mustang Bullitt is back.
|
 |
by Graeme McMillan on (#3WNJZ)
Last week the Infowars founder was booted from several platforms—but not Twitter.
|
 |
by Caroline Sinders on (#3WNGW)
Opinion: When police departments post photos of protestors on social media, it puts them at risk of harassment, or worse.
|
 |
by Miranda Katz on (#3WNF4)
The most common snooping techniques are relatively subtle, but trouble emerges when employers invest too much significance in these metrics.
|
 |
by Adrienne So on (#3WNF6)
Rad Power's RadWagon makes hauling groceries and kids a breeze, at a price you can actually pay.
|
 |
by Aarian Marshall on (#3WMRW)
Investigators are asking how a man managed to steal, fly, and crash a plane from Seattle-Tacoma International Airport without authorization.
|
 |
by Lily Hay Newman on (#3WMQ2)
Analysis of five body camera models marketed to police departments details vulnerabilities could let a hacker manipulate footage.
|
 |
by Emily Dreyfuss on (#3WM8Z)
The PGA Tour gets hit with ransomware, Wikileaks says the US Senate wants a word, and more.
|
 |
by Geek's Guide to the Galaxy on (#3WM8X)
The title of chess champion Garry Kasparov's book 'Winter Is Coming' is no accident.
|
 |
by Shannon Stirone on (#3WM75)
67p is known as the rubber ducky comet because of its funky shape—the result of two smaller bodies colliding.
|
 |
by Wired Staff on (#3WM73)
This weekend's picks include deals from LG, Apple, and Dell.
|
 |
by Jack Stewart on (#3WM4G)
Elon Musk still has to prove he has the funding in place, and investors want to know where it's coming from.
|
 |
by Wired Staff on (#3WM4E)
No matter how you prefer to crush that term paper or immerse yourself in research, these computers will help you excel.
|
 |
by Joshua Sokol on (#3WM4J)
Black holes occasionally reveal themselves when passing stars get ripped apart by their gravity. These tidal disruption events have created a new way for astronomers to map the hidden cosmos.
|
 |
by Lily Hay Newman on (#3WKJY)
While hackers at the DefCon security conference dismantle voting machines, officials stress the need for means to act on the results.
|
 |
by Louise Matsakis on (#3WKH0)
Matt Linton says he was asked to leave Caesars Palace Thursday night after a tweet about an “attack†was reported to the police.
|
 |
by Wired Staff on (#3WK91)
Samsung has gone all out with the new Galaxy Note 9. Why?
|
 |
by Louise Matsakis on (#3WK5B)
The technology company Crestron makes touchscreen panels and other equipment for places like conference rooms, which a researcher found can be turned into hidden microphones and webcams.
|
 |
by Brian Barrett on (#3WK59)
Android smartphones from Asus, LG, Essential, and ZTE are the focus of a new analysis about risks from firmware bugs introduced by manufacturers and carriers.
|
 |
by Louise Matsakis on (#3WJWX)
Researchers have repeatedly shown that writing samples, even those in artificial languages, contain a unique fingerprint that's hard to hide.
|
 |
by Jason Parham on (#3WJWZ)
Lee's latest is his best in years, investigating how identity is weaponized for and against us.
|
 |
by Matt Simon on (#3WJAZ)
A simulated basketball player can teach itself through trial and error how to finely manipulate the ball, both while stationary and while running.
|
 |
by Julie Muncy on (#3WJAX)
There's more to gaming than the newest title—catch up with our weekly recap.
|
 |
by Mejs Hasan on (#3WJ73)
Every night, 17 video cameras scan the skies for meteors.
|
 |
by Dan Solomon on (#3WJ3P)
There are certain similarities between the two disrupting companies—like spending lots of money.
|
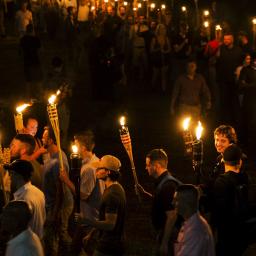 |
by Emma Grey Ellis on (#3WJ3K)
This weekend the second annual Unite the Right rally will provide the best chance to gauge the scale of a group with unknown—but much discussed—strength.
|
 |
by Megan Molteni on (#3WJ3H)
Here’s how the Parker probe was engineered to withstand temperatures spiking to over a million degrees Fahrenheit.
|
 |
by Adam Rogers on (#3WHCK)
Vice President Mike Pence's speech at the Pentagon laid out what a new US Space Force would do. It’ll cost $8 billion to start.
|
 |
by Lily Hay Newman on (#3WH9T)
Card readers used by popular companies like Square and PayPal have several security flaws that could result in customers getting majorly ripped off.
|
 |
by Emily Dreyfuss on (#3WH6W)
Silicon Valley engineers have the power to shape products and companies—both of which have enormous impact on our society.
|
 |
by Klint Finley on (#3WH38)
It may seem strange to worry about the future of broadcast in this digital era, but the fact remains: that’s how many people get their news.
|
 |
by Mejs Hasan on (#3WGTZ)
On July 27, the US Forest Service signed a new plan for managing public forest lands that lets tribes like the Karuk continue their tradition of controlled burns.
|
 |
by Lily Hay Newman on (#3WGQ7)
Researchers found a way to compromise a Mac the first time it connects to Wi-Fi, potentially putting scores of enterprise customers at risk.
|
 |
by Emily Dreyfuss on (#3WGJ5)
Online voting has major security flaws, and experts are concerned that Voatz, the platform West Virginia will use this midterm election, doesn't solve them.
|