Malware in Modern ICS: Understanding Impact While Avoiding Hype
Understanding the threat posed to industrial control systems (ICSs) by malware is difficult. It requires knowledge of proper ICS functionality in order to identify illegitimate software. One industrial cybersecurity company searched through a public malware database to develop a base ICS infection metric. A number of cyber and operational security best practices were also identified through the research, which could be used to help keep your ICS safe.
Cyber threats are well understood in the information technology (IT) security community. For years, popular IT security vendors have had sensors, such as anti-virus systems and intrusion detection systems (IDS) in customer environments, reporting back to them when intrusions by adversaries have been detected. This, coupled with security operations and incident response data in which the full intrusion of an adversary could be observed and analyzed, led to the security sub-field of intrusion analysis.
Intrusion analysis across industries, dealing with thousands of cases a year, has led to insight into how adversaries operate. This insight is called threat intelligence. However, those anti-malware systems have not historically been present in industrial control system (ICS) networks for a variety of reasons-many legitimate-and security operations and incident response data have been unavailable for sharing across the community. This means that even highly reputable IT security vendors have very little insight into ICS cyber threats.
Questionable ICS Threat StatisticsAs the ICS security community tries to understand ICS cyber threats and how to defend against them, it often turns to publicly available case studies and metrics about intrusions. However, there has been very little consistency across these datasets.
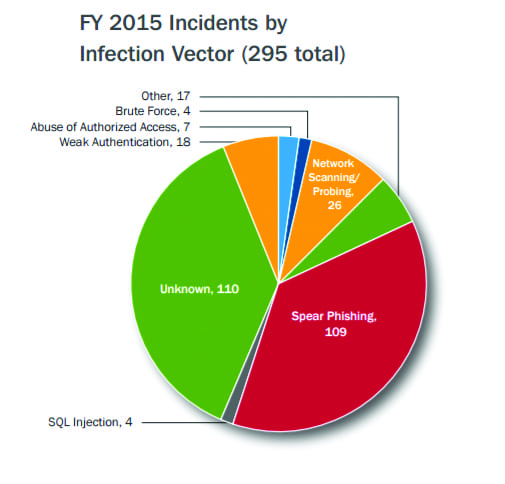
For example, the Department of Homeland Security's Industrial Control Systems Computer Emergency Response Team (ICS-CERT) puts out metrics each year on the number of incidents it is tracking. Every year these numbers range between 200 and 300 cases (Figure 1). However, the ICS-CERT openly states each year that the number 1 attack vector is "Unknown," because ICS networks lack visibility. Additionally, the team admits that a significant portion (between 70% and 90%) of incident reports come from federal agencies and not asset owners and operators. On the other end of the spectrum, we have seen reports from IT security vendors, such as Dell, suggesting that there were 675,186 supervisory control and data acquisition system attacks in January 2014.
All of the industry numbers suffer from the lack of a definition of what counts as an "attack," the lack of visibility into the ICS networks, and inconsistency with how the datasets are measured. Well-intentioned security analysts try to make the case for security, only to find that they must rely on over-hyped and inflated metrics or reference the same old use cases repeatedly. This is the problem that comes from not having base metrics and understanding around threats in ICS environments.
The Research ApproachTo help address the lack of good metrics in the community, Dragos Inc.-an industrial cybersecurity company based in Fulton, Md.-created a team and defined three hypotheses that it wanted to test. It posited the following:
a- There is a lot of infected ICS software available in public databases that IT security vendors have not identified or analyzed due to a lack of understanding around ICS software.
a- ICS-themed malware is not rare.
a- Security teams are improperly submitting sensitive ICS files to public databases.
First, the team defined what it was looking for in the context of malware. After all, human adversaries pose the threat; malware is just their mechanism (Figure 2). While malware can pose a threat to ICS, it is ultimately just a tool. The following three malware categories were defined for this research.
Nontargeted malware. Nontargeted malware was defined as any sample of malware that is common and appears not to be specifically structured or themed to target industrial environments. As an example, common malware families such as Sality and Ramnit are viruses that spread through removable media on Windows-based systems in the network. They impact IT systems just as commonly as operations technology systems in the ICS networks and are not specifically used by adversaries to gain access to ICS environments.
ICS-themed malware. ICS-themed malware on the other hand is delivered via methods designed to gain access to ICS environments. This may be apparent in phishing emails targeted specifically to asset owners and operators. It could also be malware disguised as legitimate ICS files such as human machine interface (HMI) installers, or could be connected to public internet domains and websites themed to look as if they are normal ICS websites.
ICS-tailored malware. ICS-tailored malware includes specific components and development efforts by malware authors to target industrial environments. There are only three publicly known pieces of malware that were specifically tailored to target ICS: Stuxnet, Havex, and BlackEnergy 2. However, many more adversaries have purposely tried to compromise ICS environments using nonICS specific malware.
Public Malware DatabasesAnti-virus firms and security teams often use public malware databases to check software against a large number of anti-virus engines in search of malicious files. This practice helps provide insight into the cyber threat landscape. To test Dragos' hypotheses, the team leveraged a public malware database known as VirusTotal.
VirusTotal is a website that contains more than 50 anti-malware software engines from popular security vendors such as Symantec, McAfee, and Kaspersky. Organizations from around the world use the website to submit files from their environment to check them against the 50+ engines at once, utilizing the resource to help detect malware in their environments.
However, unbeknownst to most users of this free website, but in no way a hidden fact, the submissions remain on the website and organizations that buy access can review the submissions of others. It is very common for security personnel and outsourced security teams to leverage this as a free approach to checking files against all major anti-malware products, but it leads to adversaries, as well as defenders, being able to see the same submissions.
For this research, Dragos bought VirusTotal's paid-access database to perform searches across it for ICS software, installation file paths, keywords related to specific vendors and asset owner sites, and various types of industrial software. This research was conducted over a 120-day period on millions of file and malware samples submitted to VirusTotal from users around the world. Analysts in Dragos' Threat Operations Center then analyzed the results obtained from these searches to validate that they were in fact valid ICS software files and submissions from industrial organizations.
Analyzing Infected FilesThe first hypothesis tested used a census-like approach to determine how many ICS software files submitted to VirusTotal during the 120-day period were infected with nontargeted malware. The results showed that more than 15,000 ICS file submissions, including data historian installers, HMI installers, key-generators for industrial applications, and applications for configuring and interacting with logic controllers, were compromised.
The team then analyzed the flagged submissions in an attempt to determine how many were the same file submitted multiple times, how many might be associated with numerous malware infections from the same organization, and how many were false-positives in which anti-malware vendors triggered alerts on software that was actually legitimate. Surprisingly, all of the anti-malware vendors had a high false-positive rate. They frequently identified legitimate ICS software as malicious likely due to the heuristics of those anti-malware engines. In other words, they were designed using a "better-safe-than-sorry" philosophy.
In the end, roughly 10% of the submissions appeared to be legitimate infections of unique industrial sites, meaning that 1,500 industrial organizations had malware infections in their environments during the 120-day period. Extending this to a full 365-day year, the Dragos team concluded that there were likely 3,000 to 4,500 industrial organizations that are infected with malware in their ICS networks.
The real numbers are likely to be significantly higher, because not every industrial organization or their security teams and anti-malware vendors leverage VirusTotal. This means the data represents only a subset of the larger community. However, this data provides a base metric for the community. It seems safe to say that there are a lot more than the few hundred incidents a year, as ICS-CERT reports, but there are nowhere near the 600,000 plus that multiple IT security vendors have claimed.
Themed Malware ExamplesThe second hypothesis tested specifically looked for ICS-themed malware. There have been very few public use cases of ICS-themed malware to date, but these are some of the more interesting case studies as they show a desire by human threats to compromise ICS organizations.
Malware that is costly to develop, such as ICS-tailored malware, sets a very high bar for the community that, in the team's analysis, is unnecessary. As an example, many security personnel have wondered if the community will see a Stuxnet 2.0-styled attack, but when ICS environments can easily be compromised by nontargeted malware there is no need for such tailored malware. Instead, it is wiser from an adversary resource investment perspective to use ICS-themed malware to gain a foothold in ICS networks.
In the 120-day period, the team searched through files in the VirusTotal database going back to 2013 and found over a dozen ICS-themed malware samples. There were two notable cases that stood out.
The first was a spear phishing email and accompanying PDF that was themed for the Nuclear Materials Management & Safeguards Systems from July 2011. When users opened the attachment, their system was infected with a piece of malware that opened a backdoor for adversaries, who could then remotely access infected systems. The intent of the adversaries was not within the scope of the research and would not have been discernable from the dataset.
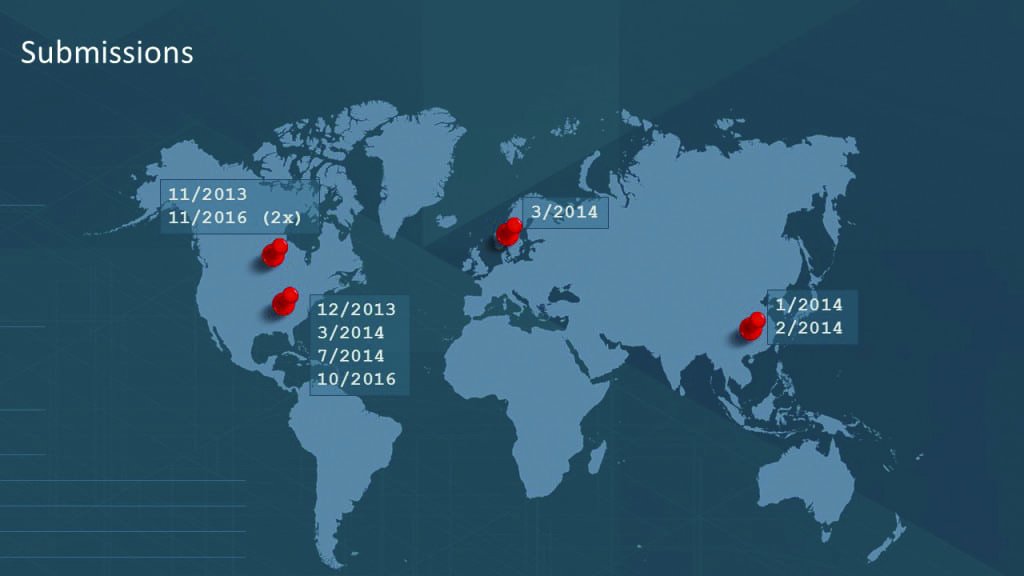
The second interesting case was a Siemens Automation themed application, designed to interact with Siemens logic controllers. The Siemens-themed application was a piece of malware designed to download and install other malware on the victim host. This suggests that the Siemens theme was used as a lure to those who had interest in Siemens (such as engineers or technicians) to install additional malware. Interestingly, the dataset showed that the first observed upload on VirusTotal, possibly from an industrial environment, dated back to March 2013. Additionally more than 10 different organizations located in the U.S., Europe, and China (Figure 3) were potentially affected, some as recently as March 2017. This particular malware did not have the capability to maliciously interact with Siemens equipment-it was simply themed to look like a Siemens application.
Malware authors can do that for any vendor. The fact that one targeting Siemens was found only represents the adversary's desire to infect organizations leveraging Siemens equipment; it in no way reflects on the security of the Siemens product itself.
Poor OPSEC PracticesThe third hypothesis tested looked for legitimate ICS software and sensitive files related to the ICS that were being uploaded to VirusTotal by potentially poorly trained security personnel. It is common for outsourced IT security teams to do large submissions of files from customer environments to VirusTotal as a free way to scan through the files for malicious activity. Of course, this leaves those files available to anyone, adversary or defender, who purchases access to the database.
The Dragos team found an alarming number of sensitive files in the database including legitimate HMI installers, key generators, and industrial software applications. There were thousands of such files that would allow adversaries to gain access to software to build their own lab environments and test attacks against specific types of ICS setups.
More alarming still were the 120 project files submitted to the database over a 90-day period. These project files contained sensitive logic controller and process information. Additionally, sensitive files were discovered including electric substation layouts and architectures as well as a Nuclear Regulatory Commission report detailing sensitive incidents that occurred in the sector (Figure 4). In many ways this represents poor OPSEC and sanitization processes by security teams and anti-malware vendors uploading otherwise sensitive customer data to public databases.
The conclusions from the research are useful to the community because they provide base metrics of infections that occur in industrial environments and identifies specific OPSEC issues. Conservatively, at least 3,000 industrial organizations are infected each year with nontargeted malware. The impact of this malware can result in operational efficiency issues and potential operational reliability issues.
None of the infections identified during the Dragos research would have resulted in catastrophic issues, but they are worth addressing through visibility and monitoring in the environment. Most of the infections were through malware that spread throughout the environment via an opportunistic method. This means that the monitoring of network traffic, as well as removable media and interconnections between the networks, would help quickly identify these infections.
ICS-themed malware can be counted in the tens instead of single use cases that the community has highlighted before. This shows that adversaries have increased awareness of industrial environments and are targeting them. Specialized and ICS-tailored malware would be required to cause the worst kinds of attacks, such as destructive attacks, but ICS-themed malware is enough to gain a foothold in many environments.
Monitoring the ICS networks and detecting abnormalities will undoubtedly yield better reliability in the environments through better security. However, many of the ICS-themed malware cases identified were taking the approach of malware themed to look like legitimate ICS software installers. A simple approach to greatly mitigate this attack vector is to verify the supply chain of the software before it is introduced into the environment.
As an example, a digital cryptographic hash of software is available upon request to the producer of the software application, and should be tested and verified before software is installed in the environment. This simple check is trivial for any security team or well-trained operator and almost completely eliminates this attack vector.
OPSEC issues will continue to exist for ICS asset owners and operators who do not validate that their security teams understand the software and files from the ICS well enough not to submit them to public databases such as VirusTotal. Security teams should leverage their own malware analysis platforms, commonly referred to as a malware sandbox, internal to their environment instead of relying on internet databases that offer free services. Free services often mean that the customer data is being sold as the product of the company.
Alternatively, paid services can be utilized when the license agreement is understood to ensure that customer data cannot be sold to third parties. Additionally, if outsourced security teams are used such as managed security service providers (MSSPs) special care should be taken to ensure that the MSSP understands ICS environments well enough to monitor them correctly. For example, MSSPs should never take customer data and submit it to public databases. Service level agreements and master service agreements with these teams should be inspected to ensure that this is not allowable in the contracts with these companies.
Dragos' research has resulted in more accurate base metrics that can be used by the community without relying on hyped estimates. These metrics can be used to make a justification for security in these environments without the need for alarmism and fear. Simple cybersecurity best practices can make the ICS a much more defensible environment and organizations should ensure that their sensitive data is not ending up in public databases through poorly reviewed security practices. a-
-Robert M. Leeis founder and CEO of Dragos Inc. andBen Milleris director of Threat Operations Center at Dragos Inc.
The post Malware in Modern ICS: Understanding Impact While Avoiding Hype appeared first on POWER Magazine.