Russian Cyber Threat Actors Have Gained Access to Power Plant ICS Systems
Russian government cyber threat actors have infiltrated workstations and servers of corporate networks containing data output from industrial control systems (ICS) or supervisory control and data acquisition (SCADA) systems associated with an unnamed number of power plants, the Department of Homeland Security (DHS) has warned.
The dire warning issued by the agency's U.S. Computer Emergency Readiness Team (US-CERT) in a March 15 report stems from a joint technical analysis conducted by the DHS in collaboration with the FBI. In it, the entities characterized the compromises as part of a multi-stage intrusion campaign carried out by Dragonfly, a group that it has been surveying for two years, and which it warned in October 2017 has reportedly stepped up cyberattacks aimed at severely crippling operations in the European and North American energy sectors.
The campaign comprises two distinct categories of victims: third-party suppliers with less secure networks, which US-CERT refers to as "staging targets," and intended targets, which comprise organizational networks. "The initial victims are peripheral organizations such as trusted third-party suppliers with less secure networks, referred to as 'staging targets' throughout this alert. The threat actors used the staging targets' networks as pivot points and malware repositories when targeting their final intended victims," the report says.
The campaign employed a variety of tactics, techniques, and procedures to infiltrate generator ICS and SCADA systems, including spear-phishing emails; watering hole domains; credential gathering; open-source and network reconnaissance; host-based exploitation; and targeting ICS infrastructure.
What Is KnownForensic analysis shows that the threat actors sought information on network and organizational design and control system capabilities within the organization. In one instance, the report says, the threat actors downloaded a small photo from a publicly accessible human resource page, which, when expanded, was a high-resolution photo that displayed control systems equipment models and status information in the background. The threat actors also compromised third-party suppliers to download source code for several intended targets' websites. They also attempted to remotely access corporate web-based email and virtual private network (VPN) connections.
Once inside the intended target's network, the threat actors used privileged credentials to access domain controllers via remote desktop protocols (RDP) and then used the batch scripts to enumerate hosts and users, as well as to capture screenshots of systems across the network.
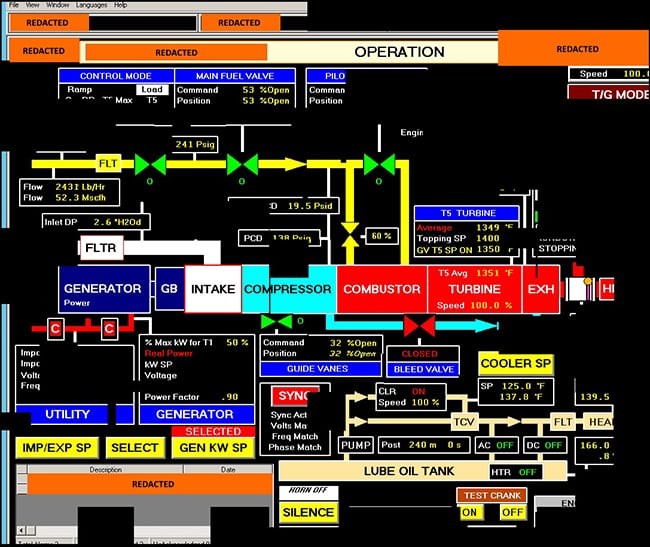
The threat is inside. US-CERT on March 15 warned that threat actors associated with the Russian government had infiltrated ICS and SCADA systems at power plants using a variety of tactics. This image is a DHS reconstruction of a screenshot fragment of a human machine interface (HMI) that the threat actors accessed. Source: US-CERT
Along with publishing an extensive list of indicators of compromise, the DHS and FBI recommended that network administrators review IP addresses, domain names, file hashes, network signatures, and a consolidated set of YARA rules for malware associated with the intrusion authored by the National Cybersecurity and Communications Integration Center. YARA is an open-source and multiplatform tool that provides a mechanism to exploit code similarities between malware samples within a family.
What Can Be DoneThe DHS and FBI also recommended that network administrators add listed IPs to watch lists to determine whether malicious activity has been observed within their organization. System owners are also advised to run the YARA tool on any system suspected to have been targeted by these threat actors. The DHS also pointed to a list of general best practices applicable to the campaign [For more, see "General Best Practices to Thwart a Dragonfly Cyberattack."]
The DHS also specifically instructs anyone who identifies the use of tools or techniques it identified to report them to the DHS or law enforcement immediately at NCCICcustomerservice@hq.dhs.gov (link sends e-mail) or 888-282-0870.
Why This is SignificantEarlier this month, cybersecurity firm Dragos Inc. warned in a series of reports that 2017 was a "watershed" year in ICS security largely due to the discovery of new capabilities and a significant increase in ICS threat activity groups.
Before last year, only three families of ICS-specific malware were known: Stuxnet, discovered before 2010, BlackEnergy 2, discovered in 2012, and Havex, which emerged in 2013. Over 2017, two new samples emerged: TRISIS and CRASHOVERRIDE. While the impact of these adversaries cannot be understated, Dragos said it is "confident" that additional unknown events have occurred.
The unprecedented disruption of electric grid operations in Ukraine on December 23, 2015 was attributed to the use of BlackEnergy 3 malware. A second attack in December 2016 that left portions of Kiev without power was pegged to CRASHOVERRIDE. Both are attributed to Russian threat actors.
Joe Slowik, a Dragos senior threat analyst, noted that numerous incidental infections occur in industrial networks on a regular basis, and while ICS-specific or ICS-tailored malware is rarer, the emergence of the two new malware samples is an ominous sign for industrial systems, which are likely to see operational losses and safety events into 2018 and into the foreseeable future, he suggested.
The latest UC-CERT report concerning the Dragonfly campaign is worrisome, according to Phil Neray, vice president of Industrial Cybersecurity at Boston-based industrial cybersecurity firm CyberX, and it validates what the ICS community has known for months: "Russian cyberattackers have both the intent and the ability to successfully compromise our critical infrastructure networks, including in our nuclear facilities," he said.
"The attackers demonstrated sophistication by using a variety of techniques to steal credentials from control system engineers-from phishing to website 'watering hole' attacks-and especially in the way they covered their tracks after intruding our networks, by deleting logs and other digital breadcrumbs that could reveal their presence," Neray explained.
"It's easy to see how Russia could leverage these dangerous footholds to test our red lines and threaten us with sabotage in the event of escalating hostilities, such as new Russian incursions on former Soviet territories."
-Sonal Patel is a POWER associate editor (@sonalcpatel, @POWERmagazine)
The post Russian Cyber Threat Actors Have Gained Access to Power Plant ICS Systems appeared first on POWER Magazine.