A leaky database of SMS messages is a reminder that SMS is really, really insecure
Berlin-based security researcher Si(C)bastien Kaul discovered that Voxox (formerly Telcentris) -- a giant, San Diego-based SMS gateway company -- had left millions of SMSes exposed on an Amazon cloud server, with an easily queried search front end that would allow attackers to watch as SMSes with one-time login codes streamed through the service.
It's a timely reminder that SMS sucks. It is not secure, and should not be used for two-factor authentication messages (2FA). Weak 2FA is behind an epidemic of number-porting scams that are bootstrapped to steal your online accounts, your cryptocurrency, and your email.
Authenticator apps are much more secure (which is not to say they are perfect -- and security economics predicts that as they are used to defend more and more, they will be subject to ever-better-resourced attacks, so watch this space).
Each record was meticulously tagged and detailed, including the recipient's cell phone number, the message, the Voxox customer who sent the message and the shortcode they used.Among our findings from a cursory review of the data:
* We found a password sent in plaintext to a Los Angeles phone number by dating app Badoo;
* Several Booking.com partners were sent their six-digit two-factor codes to log in to the company's extranet corporate network;
* Fidelity Investments also sent six-digit security codes to one Chicago Loop area code;
* Many messages included two-factor verification codes for Google accounts in Latin America;
* A Mountain View, Calif.-based credit union, the First Tech Federal Credit Union, also sent a temporary banking password in plaintext to a Nebraska number;
* We found a shipping notification text sent by Amazon with a link, which opened up Amazon's delivery tracking page, including the UPS tracking number, en route to its destination in Florida;
* Messenger apps KakaoTalk and Viber, and quiz app HQ Trivia use the service to verify user phone numbers;
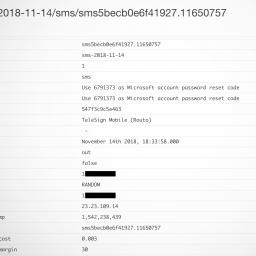
* We also found messages that contained Microsoft's account password reset codes and Huawei ID verification codes;
* Yahoo also used the service to send some account keys by text message;
* And, several small to mid-size hospitals and medical facilities sent reminders to patients about their upcoming appointments, and in some cases, billing inquiries.
A leaky database of SMS text messages exposed password resets and two-factor codes [Zack Whittaker/Techcrunch]
(via The Verge)