Ransomware Forces Two Chemical Companies to Order ‘Hundreds of New Computers’
A ransomware attack appears to have affected two American chemicals companies, Motherboard has learned.
Hexion and Momentive, which make resins, silicones, and other materials, and are controlled by the same investment fund, were hit by the ransomware on March 12, according to a current employee. An internal email obtained by Motherboard and signed by Momentive's CEO Jack Boss refers to a "global IT outage" that required the companies to deploy "SWAT teams" to manage.
Based on the ransom message, the ransomware that hit Hexion and Momentive appears to be LockerGoga, the same ransomware that forced an aluminum manufacturing giant Norsk Hydro to shut down its worldwide network this week. Motherboard cross-referenced the ransom message associated with the Momentive attack to known LockerGoga attacks, and found that the language and formatting were identical.
Got a tip? You can contact Lorenzo Franceschi-Bicchierai securely on Signal at +1 917 257 1382, OTR chat at lorenzofb@jabber.ccc.de, or email lorenzo@motherboard.tv.
On the day of the attack, some of the companies' Windows computers were hit with a blue screen error and their files encrypted, said the current employee, who asked to remain anonymous as they were not authorized to speak to the press.
"Everything [went down]. Still no network connection, email, nothing," they said in an online chat on Thursday.
Boss's email said that the data on any computers that were hit with the ransomware is probably lost, and that the company has ordered "hundreds of new computers."
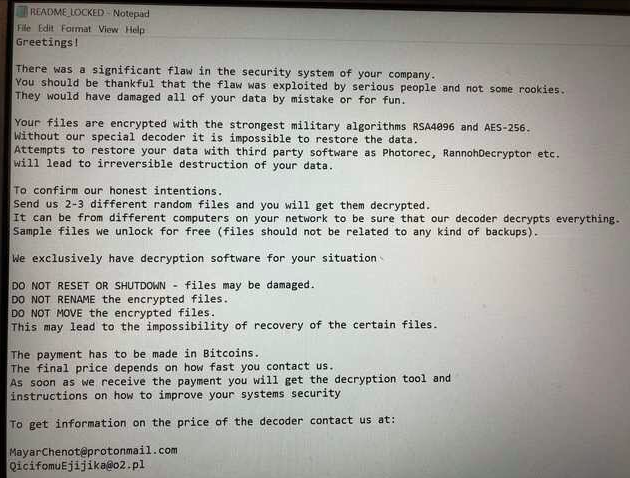 A screenshot of the ransom notice displayed on a Momentive laptop. Image: Motherboard
A screenshot of the ransom notice displayed on a Momentive laptop. Image: MotherboardOn Friday evening, Hexion announced in a press release that it was working to resume normal operations "in response to a recent network security incident."
Boss's email indicates that the ransomware first hit the company last week, and explains what the company is doing to recover. Among the measures taken, Boss wrote that the Momentive is giving some employees new email accounts because their old ones are still inaccessible. The company notes that it is using a new domain-momentiveco.com for new email addresses rather than momentive.com.
Motherboard sent an email to a known Momentive email address that uses the old domain, momentive.com, but it bounced back. The error message noted that "due to a network event," email services are currently unavailable.
The leaked email also notes that as more people who email the company receive the same error message that Motherboard saw, the more likely employees are to be contacted by third parties looking to more information. It then lists an email address and phone number that should be given to the media. Motherboard called this number and emailed this address but did not get a response.
On Friday, Motherboard called Hexion's main phone line. The employee who answered declined to provide any information about the attack. When asked whether there had been an incident, the employee said "no comment" and immediately hung up. Motherboard called back and spoke to someone else, who did not identify themselves but said that they could not provide any information to us.
News of this attack shows that the hackers behind the LockerGoga ransomware may be more active than previously thought.
Until today, there were only two known victims of LockerGoga, a relatively new type of malware that infects computers, encrypts their files and ask for a ransom. The first known victim was Altran, a French engineering consulting firm that was hit in late January. Then earlier this week, the Norwegian aluminum giant Norsk Hydro revealed that it had been hit by a ransomware attack. A Kaspersky Lab spokesperson said that they have knowledge of more victims around the world.
Hydro did not mention what malware hit it. But Norwegian media, citing local cybersecurity authorities, said it was LockerGoga. MalwareHunterTeam, a group of independent security researchers, found a sample of LockerGoga on the online malware repository VirusTotal that had been uploaded from Norway on the day Hydro was hit.
MalwareHunterTeam told Motherboard that the ransom notice shared by our source is very similar to the one found in LockerGoga attacks.
Joe Slowik, a security researcher at Dragos, a cybersecurity company that focuses on critical infrastructure and who has studied the malware, said that LockerGoga does not appear to be very good at its purported goal: collecting money from the victims. In fact, as the ransom note shows, and unlike other popular ransomware, victims have to email the hackers and negotiate a price to get files decrypted, making it harder for the criminals to scale their earnings.
"It's a piece of very inefficient ransomware," Slowik told Motherboard in a phone call.
It may be inefficient at collecting money, but it's apparently good enough to slow down multinational companies in both Europe and the United States.
Listen to CYBER, Motherboard's new weekly podcast about hacking and cybersecurity.