With warshipping, hackers ship their exploits directly to their target’s mail room
Why break into a company's network when you can just walk right in - literally?
Gone could be the days of having to find a zero-day vulnerability in a target's website, or having to scramble for breached usernames and passwords to break through a company's login pages. And certainly there will be no need to park outside a building and brute-force the Wi-Fi network password.
Just drop your exploit in the mail and let your friendly postal worker deliver it to your target's door.
This newly named technique - dubbed "warshipping" - is not a new concept. Just think of the traditional Trojan horse rolling into the city of Troy, or when hackers drove up to TJX stores and stole customer data by breaking into the store's Wi-Fi network. But security researchers at IBM's X-Force Red say it's a novel and effective way for an attacker to gain an initial foothold on a target's network.
"It uses disposable, low cost and low power computers to remotely perform close-proximity attacks, regardless of the cyber criminal's location," wrote Charles Henderson, who heads up the IBM offensive operations unit.
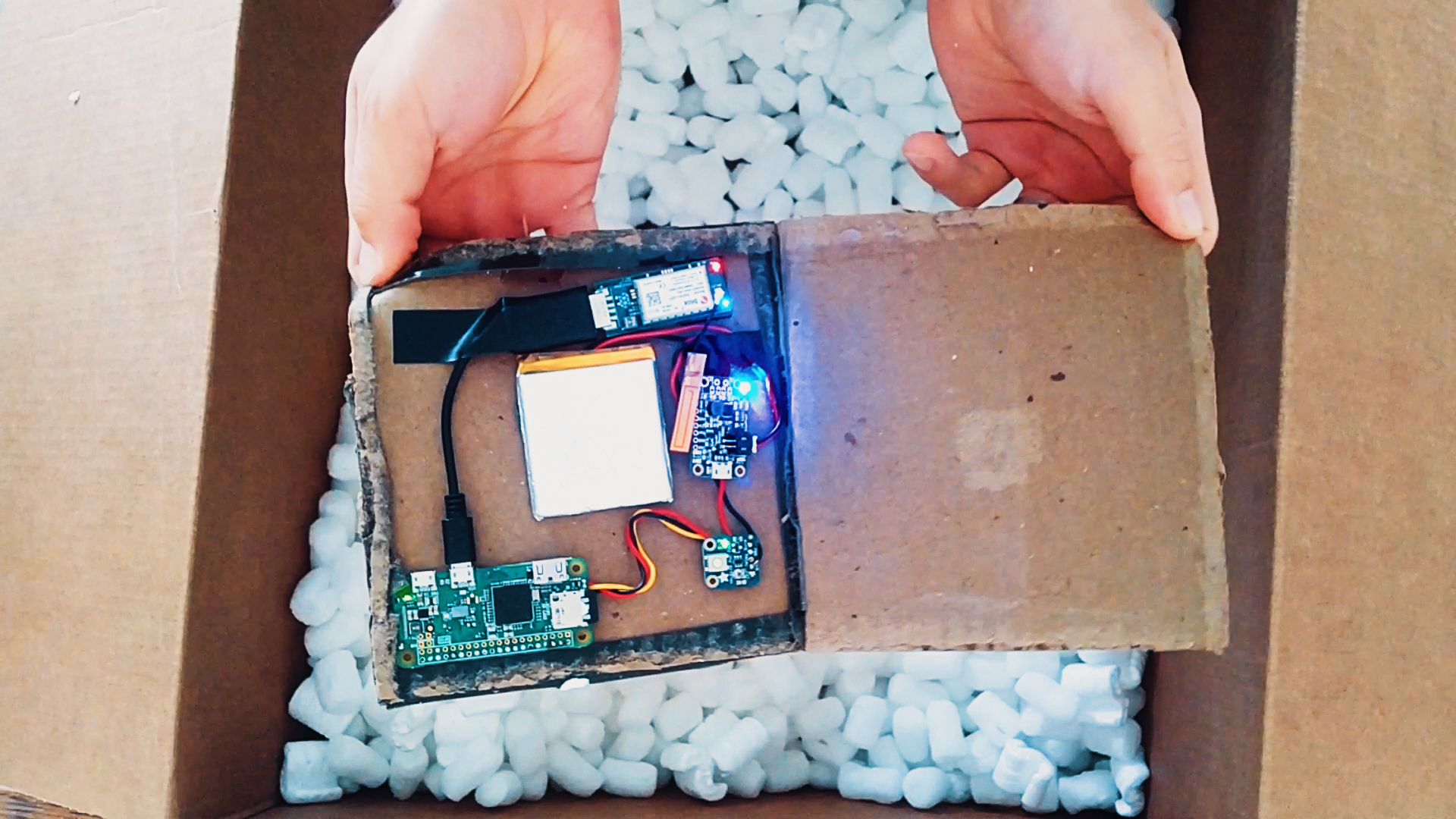
A warshipping device. (Image: IBM/supplied)
The researchers developed a proof-of-concept device - the warship - which has a similar size to a small phone, into a package and dropped it off in the mail. The device, which cost about $100 to build, was equipped with a 3G-enabled modem, allowing it to be remote controlled so long as it had cell service. With its onboard wireless chip, the device would periodically scan for nearby networks - like most laptops do when they're switched on - to track the location of the device in its parcel.
"Once we see that a warship has arrived at the target destination's front door, mailroom or loading dock, we are able to remotely control the system and run tools to either passively, or actively, attack the target's wireless access," wrote Henderson.
Once the warship locates a Wi-Fi network from the mailroom or the recipient's desk, it listens for wireless data packets it can use to break into the network. The warship listens for a handshake - the process of authorizing a user to log onto the Wi-Fi network - then sends that scrambled data back over the cellular network back to the attacker's servers, which has far more processing power to crack the hash into a readable Wi-Fi password.
With access to the Wi-Fi network, the attacker can navigate through the company's network, seeking out vulnerable systems and exposed data, and steal sensitive data or user passwords.
All of this done could be done covertly without anyone noticing - so long as nobody opens the parcel.
"Warshipping has all the characteristics to become a stealthy, effective insider threat - it's cheap, disposable, and slides right under a targets' nose -all while the attacker can be orchestrating their attack from the other side of the country," said Henderson. "With the volume of packages that flow through a mailroom daily - whether it be supplies, gifts or employees' personal purchases - and in certain seasons those numbers soar dramatically, no one ever thinks to second guess what a package is doing here."
The team isn't releasing proof-of-concept code as to not help attackers, but uses the technique as part of its customer penetration testing services - which help companies discover weak spots in their security posture.
"If we can educate a company about an attack vector like this, it dramatically reduces the likelihood of the success of it by criminals," Henderson said.
