The voting machines that local officials swore were not connected to the internet have been connected to the internet for years
Election Systems & Software (ES&S) is America's leading voting machine vendor; they tell election officials (who are county-level officials who often have zero cybersecurity advice or expertise) not to connect their systems to the internet, except briefly to transmit unofficial tallies on election night.
This is a stupid idea to begin with. These systems shouldn't have modems, and they shouldn't ever be connected to the internet, at all.
But as it turns out, lots of election officials, including many in heavily contested districts that have determined the outcomes of national elections (cough Florida cough) just leave their machines connected to the internet all the time, while denying that this is the case, possibly because they don't know any better.
A team of ten leading security experts, including some affiliated with NIST's election cybersecurity efforts, have used internet-wide scanning to locate dozens of these systems, live on the internet, and because it's the internet, they're not even sure who all of them belong to, and can't alert the relevant officials. Many of these systems have been online for months; some have likely been online for years.
ES&S has downplayed the risk, using incredibly misleading definitions of "not connected to the internet" (for example, insisting that "behind a firewall" is the same thing as "airgapped"). The company's account of its security best practices, training and maintenance are belied by their own public documents as well as authenticated whistleblower's accounts.
In one case -- Rhode Island -- it appears that every vote cast in the state is tallied on a single system that is often available on the internet.
There's no evidence that any of the systems have been tampered with, but in part that's because the inconsistencies involving these systems have not been resolved with recounts, or when recounts have been ordered, they've been recounts using the same, potentially compromised systems.
Kim Zetter documents all of this in eye-watering detail in a damning, beautifully reported longread for Motherboard.
Senate Republicans have stalled all legislation aimed at improving voting system security.
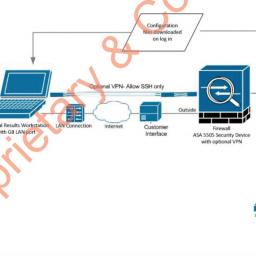
The ES&S firewalls are configured to only allow authenticated systems to connect and pass data through the firewall to the SFTP server; they also block outbound connections to the internet from systems behind the firewall. Authenticated systems include modem-enabled voting machines at voting precincts, or a computer at regional transmission sites. But even these authenticated systems, armed with passwords to communicate with the SFTP server, can only communicate with that server and cannot reach past this to the critical backend systems, according to ES&S. The passwords for the voting machines to communicate with the SFTP server are generated by the election-management system and passed to the voting machines on a USB flash drive when the systems are programmed before each election, and the passwords are also stored on the SFTP server to authenticate the machines.
The two backend systems-the reporting system that tabulates votes and the election-management system-sit on a local area network, which is connected to the Cisco firewall through a switch. The switch doesn't provide additional security; it simply acts as a traffic cop to direct incoming data to the right system. To collect the encrypted votes the voting machines have deposited on the SFTP server, the backend reporting system reaches through the firewall to query the server every few minutes. If new files have arrived, the reporting system grabs those, decrypts them to read the votes inside, then tabulates them.
At least this is how the configuration in the diagram ES&S provided Motherboard works. But a different diagram the company submitted last year to Travis County, Texas, as part of a contract proposal, and which is available online, shows the reporting system and election-management system directly connected to the SFTP server through the switch, and all of them are connected to the firewall. This would mean the backend reporting system could bypass the firewall to reach the SFTP server directly, a less secure configuration. Weber of ES&S told Motherboard the Travis diagram is incorrect.
Exclusive: Critical U.S. Election Systems Have Been Left Exposed Online Despite Official Denials [Kim Zetter/Motherboard]
(Thanks, Anonymous!)