How to identify and remove KidsGuard ‘stalkerware’ from your phone
We reported today on KidsGuard, a powerful mobile spyware. Not only is the app secretly installed on thousands of Android phones without the owners' consent, it also left a server open and unprotected, exposing the data it siphoned off from victims' infected devices to the internet.
This consumer-grade spyware also goes by "stalkerware." It's often used by parents to monitor their kids, but all too frequently it's repurposed for spying on a spouse without their knowledge or consent. These spying apps are banned from Apple and Google's app stores, but those bans have done little to curb the spread of these privacy invading apps, which can read a victim's messages, listen to their phone calls, track their real-time locations and steal their contacts, photos, videos and anything else on their phones.
Stalkerware has become so reviled by privacy experts, security researchers and lawmakers that antivirus makers have promised to do more to better detect the spyware.
TechCrunch obtained a copy of the KidsGuard app. Using a burner Android phone with the microphones and cameras sealed, we tested the spyware's capabilities. We also uploaded the app to online malware scanning service VirusTotal, which runs uploaded files against dozens of different antivirus makers. Only eight antivirus engines flagged the sample as malicious - including Kaspersky, a member of the Coalition Against Stalkerware and F-Secure.
Yoong Jien Chiam, a researcher at F-Secure's Tactical Defense unit, analyzed the app and found it can obtain "GPS locations, account name, on-screen screenshots, keystrokes, and is also accessing photos, videos, and browser history."
KidsGuard's developer, ClevGuard, does not make it easy to uninstall the spyware. But this brief guide will help you to identify if the spyware is on your device and how to remove it.
Before you continue, some versions of Android may have slightly different menu options, and you take these following steps at your own risk. This only removes the spyware, and does not delete any data that was uploaded to the cloud.
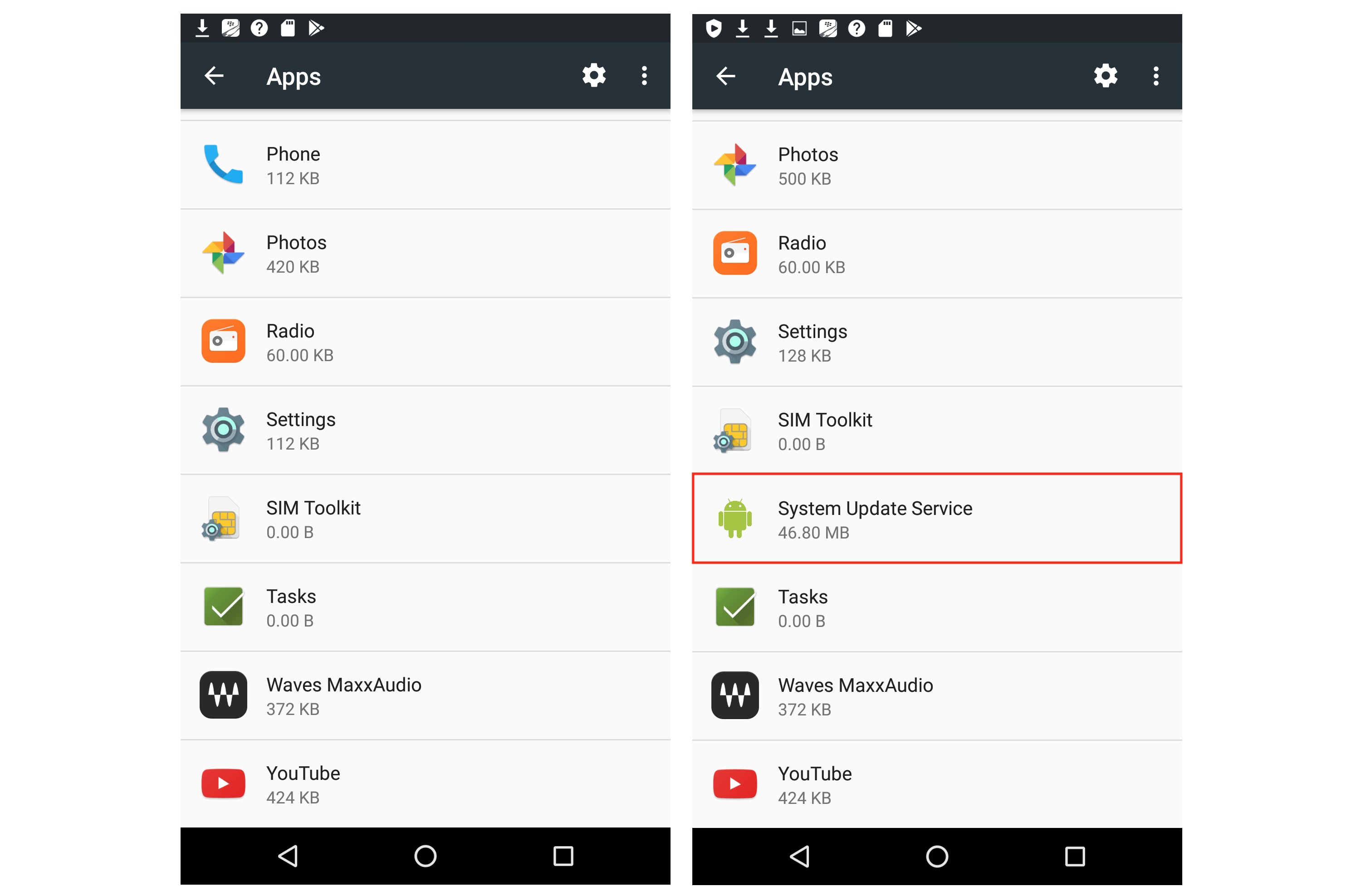
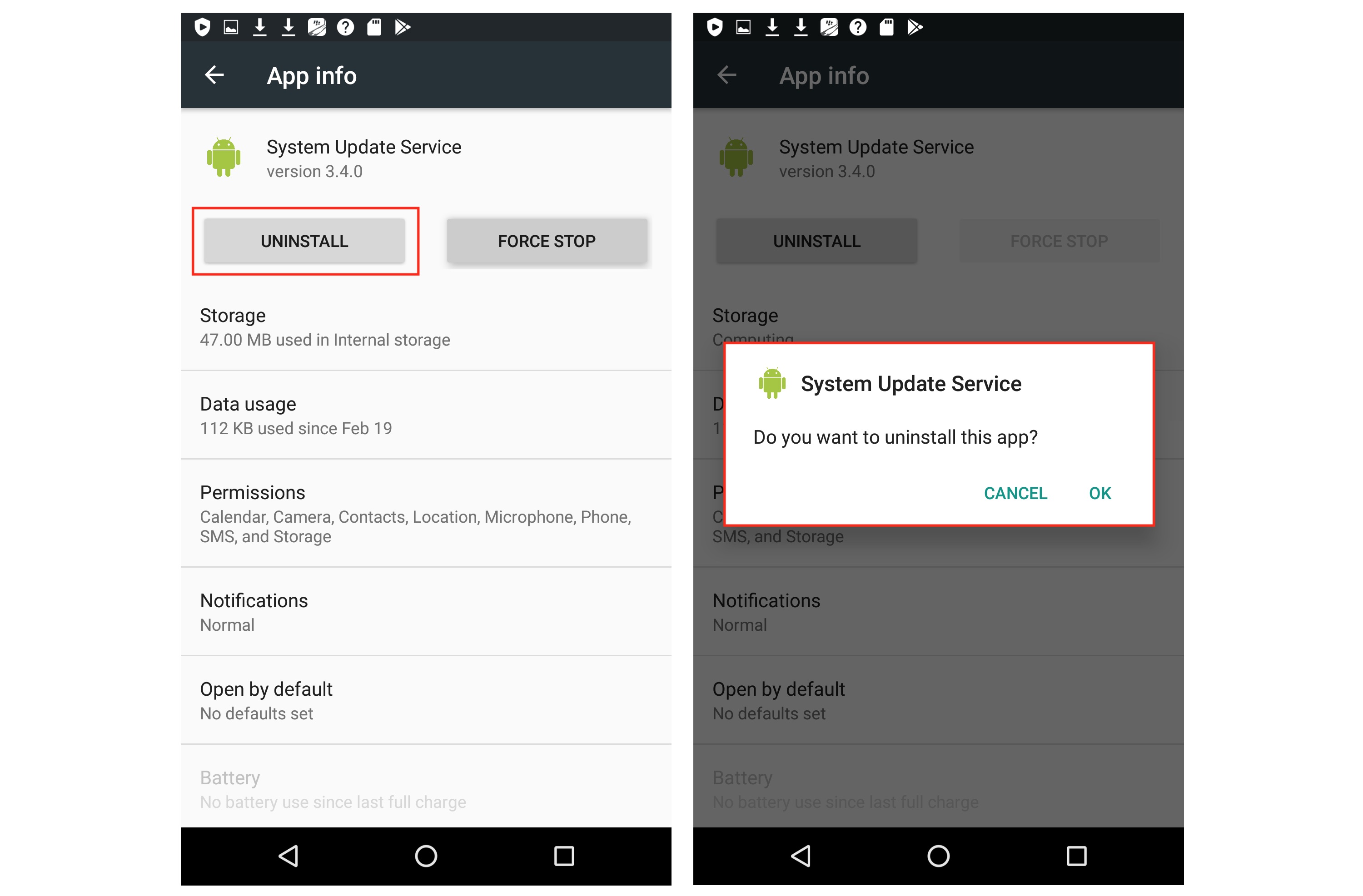
How to identify the spywareIf you have an Android device, go to Settings > Apps, then scroll down and see if "System Update Service" is listed. This is what ClevGuard calls the app to disguise it from the user. If you see it, it is likely that you are infected with the spyware.
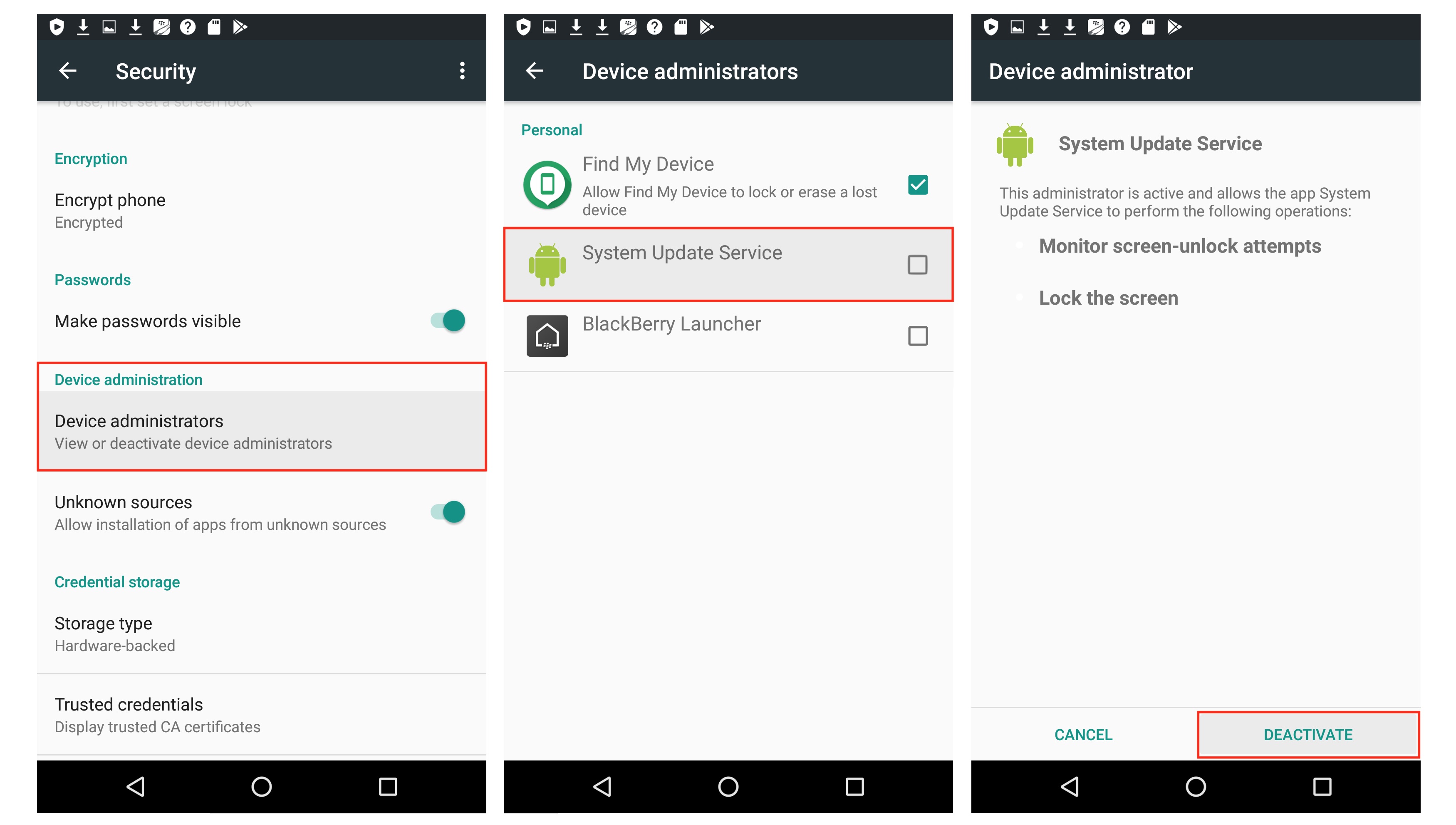
Go to Settings > Security, then Device administrators, then untick the "System Update Service" box, then hit Deactivate.
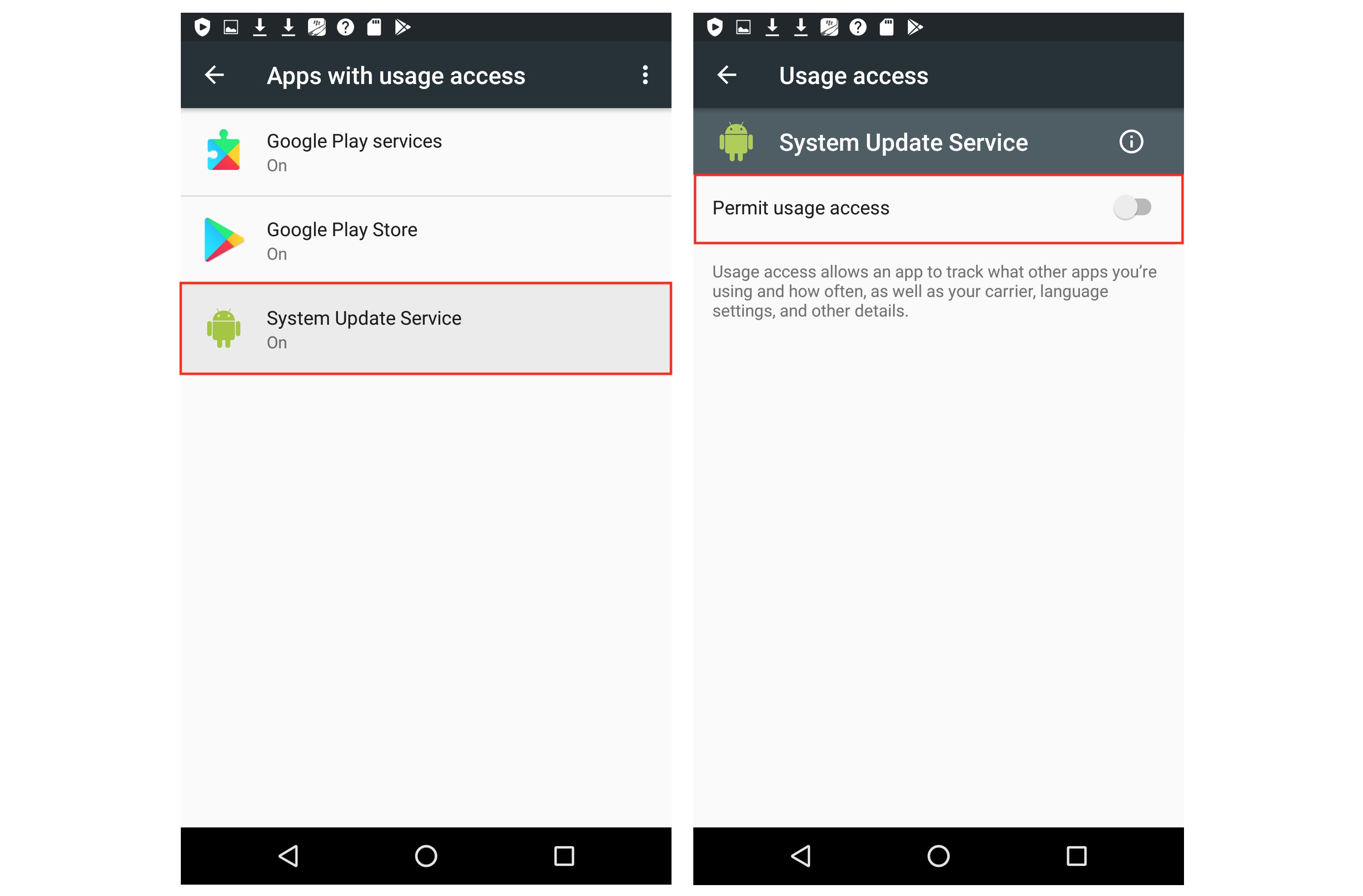
Now, go back to Settings > Security, then scroll to Apps with usage access. Once here, tap on "System Update Service," then switch off the permit usage toggle.
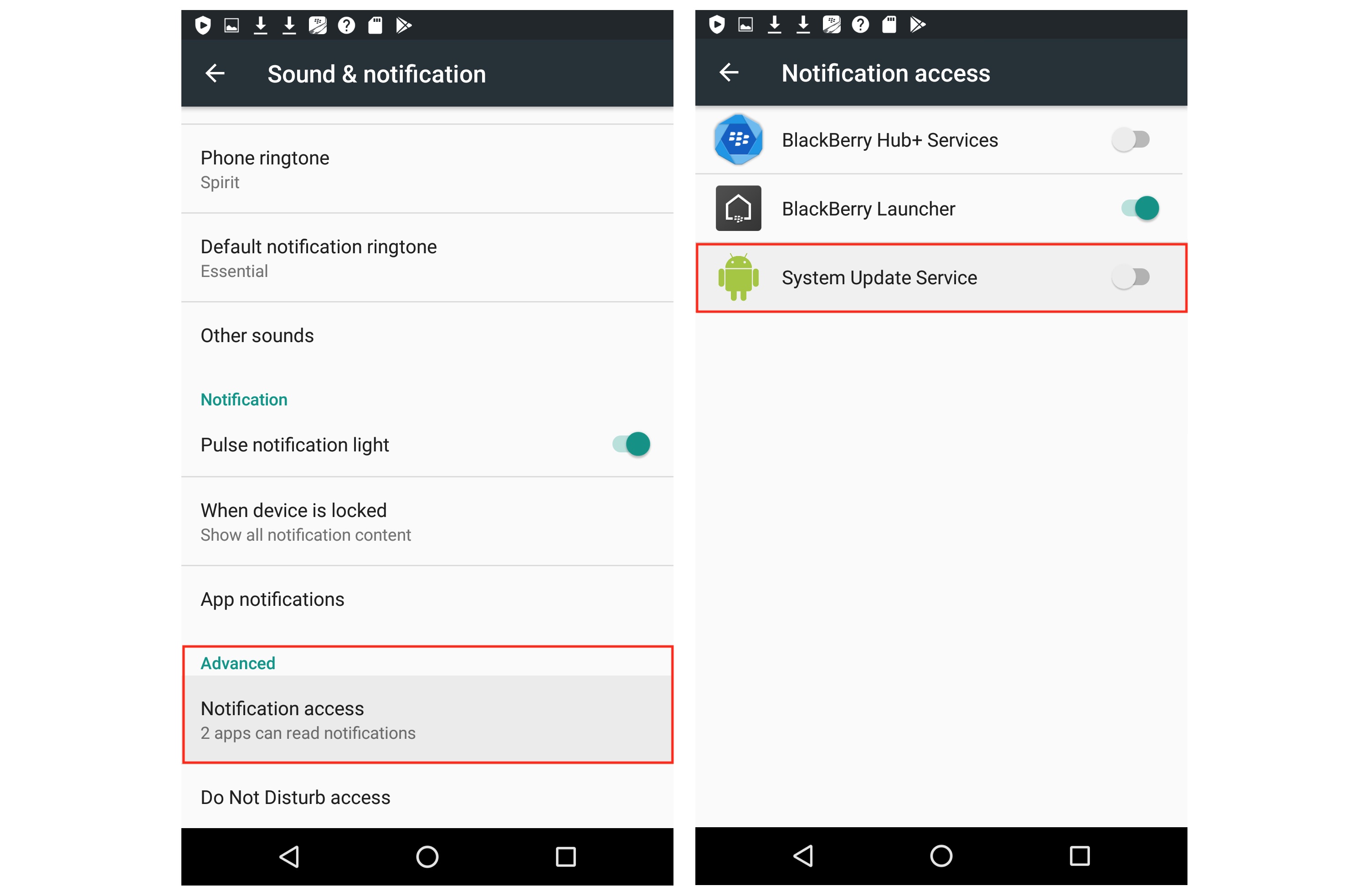
Once that is done, go back to Settings > Sound & notification, then go to Notification access. Now switch off the toggle for "System Update Service."
Following those steps, you have effectively disabled the spyware. Now you are able to uninstall it. Go to Settings > Apps and scroll down to "System Update Service." You should be able to hit Uninstall, but you may need to hit Force Stop first. Tap OK to uninstall the app. This may take a few minutes.
Now that you've rid your device of the spyware, you'll need to enable a couple of settings that were switched off when your device was first infected. Firstly, go back to Settings > Security, then switch off the toggle for Unknown sources. Secondly, go to the Play Store > Play Protect. If you have the option, select Turn on. Once it's on, you should check to ensure that it "looks good."