Microsoft secretly seized domains used in COVID-19-themed email cyberattacks
A court has granted a bid by Microsoft to seize and take control of malicious web domains used in a large-scale cyberattack targeting victims in 62 countries with spoofed emails in an effort to defraud unsuspecting businesses.
The technology giant announced the takedown of the business email compromise operation in a Tuesday blog post.
Tom Burt, Microsoft's consumer security chief, said the attackers tried to gain access to victims' email inboxes, contacts and other sensitive files in order to send emails to businesses that look like they came from a trusted source. The end goal of the attack is to steal information or redirect wire transfers.
Last year, the FBI said businesses lost more than $1.7 billion as a result of business email compromise attacks.
Microsoft said it first detected and scuppered the operation in December, but that the attackers returned, using the COVID-19 pandemic as a fresh lure to open malicious emails. In one week alone, the attackers sent malicious emails to millions of users, Microsoft said.
Last month, the company secretly sought legal action by asking a federal court to allow it to take control and sinkhole" the attacker's domains, effectively shutting down the operation. The court granted Microsoft's request shortly after but under seal, preventing the attackers from learning of the imminent shutdown of their operation.
Details of the case were unsealed Monday after Microsoft secured control of the domains.
It shows a growing trend of using the U.S. courts system to shut down cyberattacks when time is of the essence, without having to involve the federal authorities, a process that's frequently cumbersome, bureaucratic, and seldom quick.
This unique civil case against COVID-19-themed [business email compromise] attacks has allowed us to proactively disable key domains that are part of the criminals' malicious infrastructure, which is a critical step in protecting our customers," said Burt.
Microsoft declined to say who, or if it knew, who was behind the attack but a spokesperson confirmed it was not a nation state-backed operation.
The attack worked by tricking victims into turning over access to their email accounts. Court filings seen by TechCrunch describe how the attackers used phishing emails are designed to look like they come from an employer or other trusted source," while designed to look like they are legitimate emails from Microsoft.
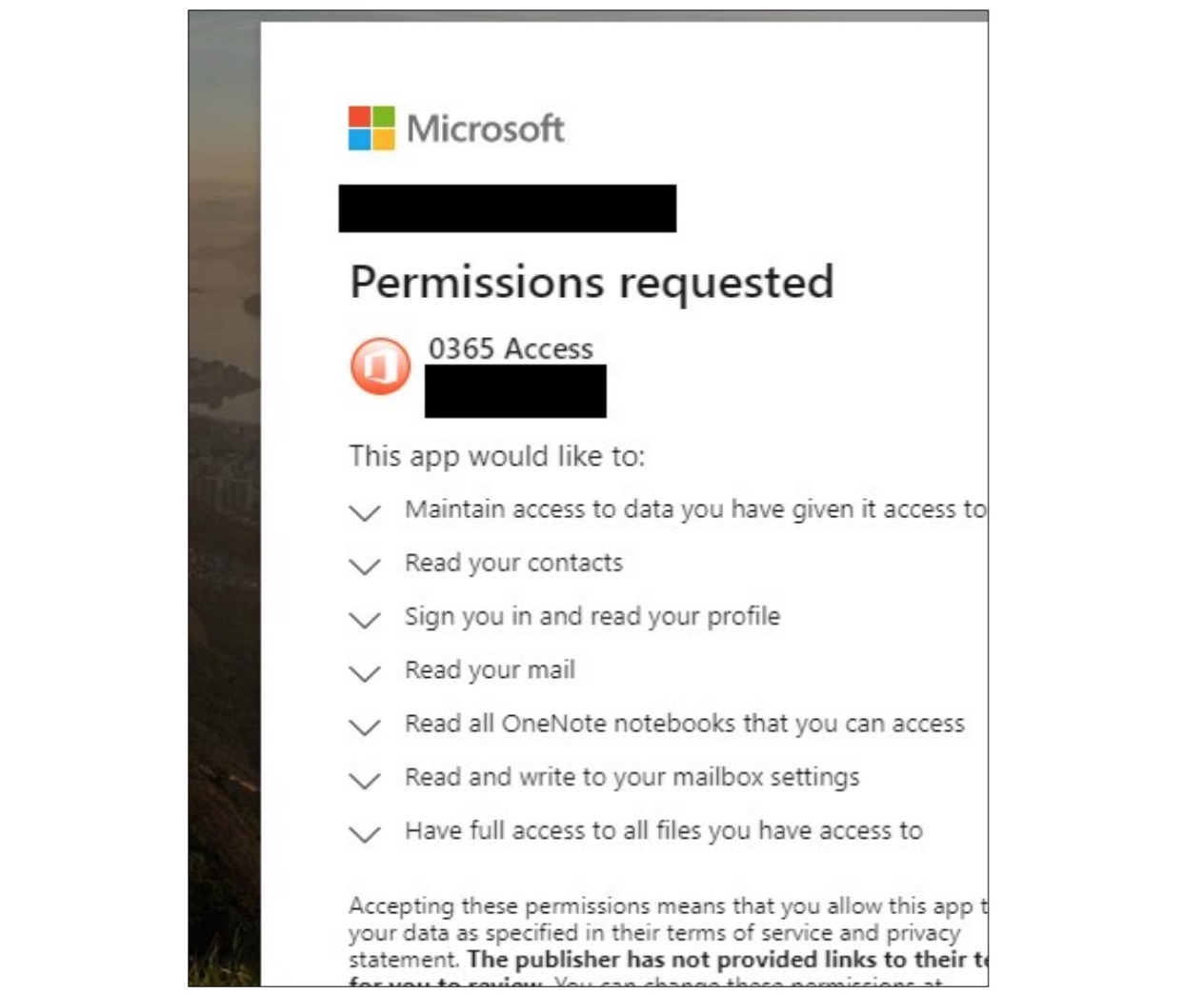
The malicious web app that steals victims' account access tokens. (Image: Microsoft)
Once clicked, the phishing email opens a legitimate Microsoft login page. But once the victim enters their username and password, the victim is redirected to a malicious web app that was built and controlled by the attackers. If the user is tricked into approving the web app access to their accounts, the web app siphons off and sends the victim's account access tokens to the attackers. Account access tokens are designed to keep users logged in without having to re-enter their passwords, but if stolen and abused, can grant full access to a victim's account.
Burt said the malicious operation allowed the attackers to trick victims into giving over access to their accounts without explicitly" requiring the victim to turn over their username and password, as they would in a more traditional phishing campaign."
With access to those accounts, the attackers would have full control of the accounts to send spoofed messages designed to trick companies into turning over sensitive information or carry out fraud, a common tactic for financially-driven attackers.
By taking out the attackers' domains used in the attack, Burt said the civil case against the attackers let the company to proactively disable key domains that are part of the criminals' malicious infrastructure."
It's not the first time Microsoft has asked a court to grant it ownership of malicious domains. In the past two years, Microsoft took control of domains belonging to hackers backed by both Russia and Iran.
Microsoft sues to take control of domains involved in Iran hacking campaign