DHS Issues Pipeline Cybersecurity Directive but Industry Championing FERC Mandatory Standards
The post DHS Issues Pipeline Cybersecurity Directive but Industry Championing FERC Mandatory Standards appeared first on POWER Magazine.
Owners and operators of the 100 most critical" hazardous liquid and natural gas pipelines, and liquefied natural gas (LNG) facilities will need to act within the next 30 days to align with federal cybersecurity guidance under new mandates issued by the Transportation Security Administration (TSA).
The TSA's May 27-issued pipeline-focused security directive is a notable, concerted step by the U.S. federal government to secure a key component of the nation's critical infrastructure. However, industry is separately coalescing to convince Congress that the Federal Energy Regulatory Commission (FERC) is better equipped for the mandate authority to issue physical and cybersecurity standards for the nation's vast network of natural gas pipelines.
TSA Requires Action Within 30 DaysSecurity Directive (2021-01), which TSA, a Department of Homeland Security (DHS) agency, declared effective on May 28 requires three actions. First, owners and operators of pipeline systems deemed critical"-based on factors such as volume transported and service to other critical sectors-will by June 4 designate a primary and alternate corporate cybersecurity coordinator, who can be accessible" to TSA and the DHS's Cybersecurity and Infrastructure Security Agency (CISA) 24 hours a day, seven days a week. Pipeline owners must also report to CISA-within 12 hours of discovery-any cybersecurity incidents they discover on their IT or operational technology (OT) systems, as well as physical attacks on their network infrastructure.
Over the next 30 days, pipeline owners must also immediately review pipeline cybersecurity measures in the TSA's April 2021-revised Pipeline Security Guidelines and assess whether current practices align with guidelines. They must also identify any gaps along with remediation measures.
The directive responds directly to a ransomware incident that on May 7 prompted Colonial Pipeline Co., owner of the nation's largest refined products pipeline, to proactively shut it down. The full pipeline, a 2.5-million-barrel-per-day system of approximately 5,500 miles, wasn't restarted until May 13, significantly disrupting a key supply of transportation fuels to the East Coast and southeastern U.S.
The cybersecurity landscape is constantly evolving and we must adapt to address new and emerging threats," said Secretary of Homeland Security Alejandro N. Mayorkas in a statement as TSA rolled out the directive this week.
The DHS said the TSA is also now considering follow-on mandatory measures that will further support the pipeline industry in enhancing its cybersecurity and that strengthen the public-private partnership so critical to the cybersecurity of our homeland."
Pipeline Security's Cross-Cutting Impact-and ResponsibilitiesAs POWER reported, the Colonial pipeline attack rattled industry. Though just one of more than 4,000 ransomware attacks that occur daily, according to CISA, its high-stakes repercussions underscored the threats cybersecurity attacks pose to the operational reliability of critical infrastructure.
On Wednesday, industrial control system (ICS) expert and Cyber Vice President of Portfolio Strategy and Enablement at Hexagon Nick Cappi told POWER:I am glad to see government involvement in securing our critical infrastructure (even if it's limited to a specific sector, in this case, pipelines). With that said, it feels like a knee-jerk reaction to an event. Hopefully, we don't have to wait for events in each sector to receive the same type of attention from government agencies and new regulations to prevent future incidents," he said.
However, owing to the vast scope of the U.S. pipeline system's basic components and vulnerabilities, TSA is just one of several federal agencies that are tasked with protecting the nation's pipeline systems. The agency's Security Policy and Industry Engagement's Pipeline Security Branch today bears primary oversight responsibility for the physical security and cybersecurity of the transmission and distribution pipeline system.
Still, as tasked by the 9/11 Commission Act of 2007, the entity only identifies the top 100 critical pipeline systems in the nation, though there are more than 3,000 pipeline operators in the U.S. The TSA issued its first voluntary Pipeline Security Guidelinesin 2011 and released revised guidelines in March 2018. Following an audit by the Government Accountability Office (GAO) that found the revisions did not include all elements from the National Institute of Standards and Technology's (NIST's) Framework for Improving Critical Infrastructure Cybersecurity,TSA issued an updated version of the security guidelines this April, presumably to improve its assessment of critical risks.
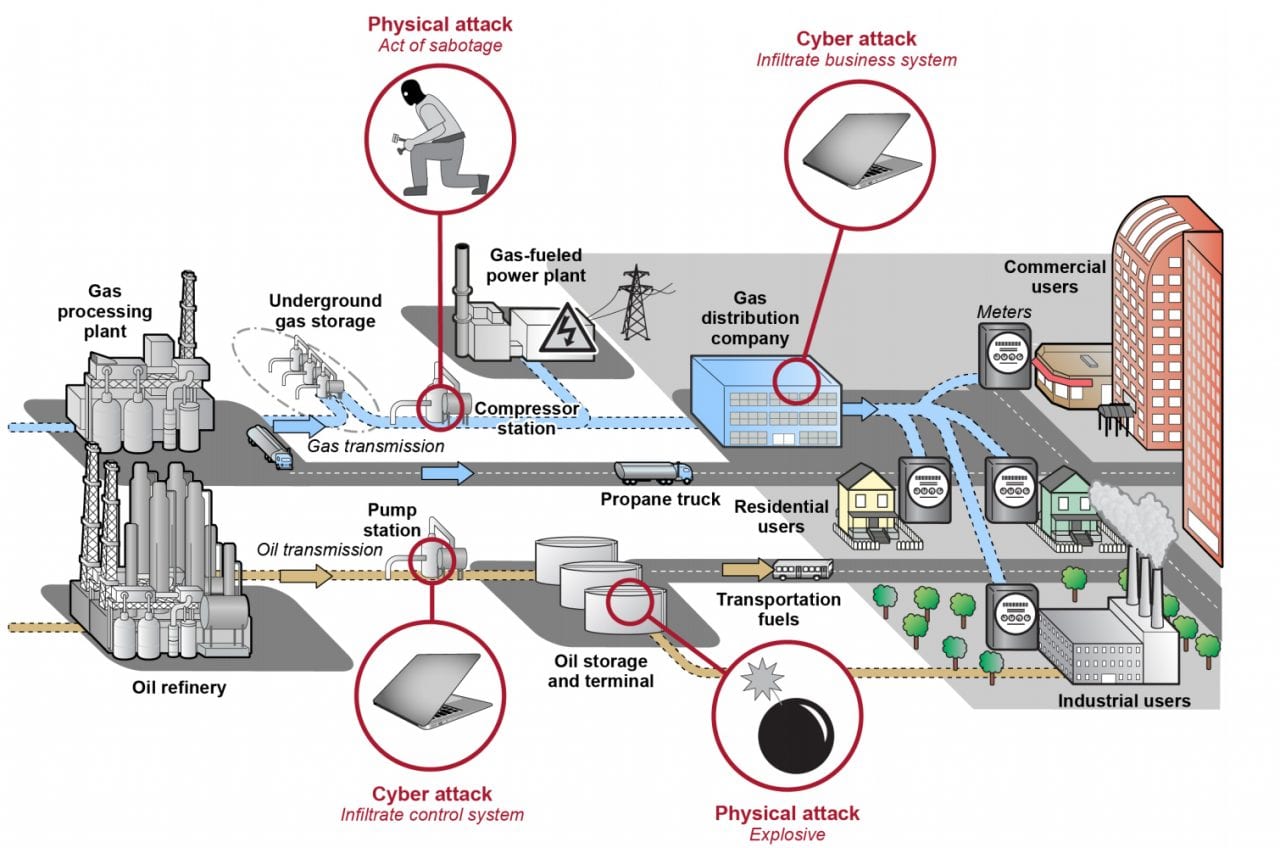
 More than 2.7 million miles of pipeline transport and distribute oil, natural gas, and other hazardous products throughout the U.S. This illustration shows the U.S. pipeline system, its basic components, examples of vulnerabilities, and the entities to which it supplies energy and raw materials. These entities include utility companies, airports, military sites, and industrial and manufacturing facilities. Source: GAO
More than 2.7 million miles of pipeline transport and distribute oil, natural gas, and other hazardous products throughout the U.S. This illustration shows the U.S. pipeline system, its basic components, examples of vulnerabilities, and the entities to which it supplies energy and raw materials. These entities include utility companies, airports, military sites, and industrial and manufacturing facilities. Source: GAO
Other agencies that also hold pipeline security responsibilities include the National Cybersecurity and Communications Integration Center, a DHS program that assists critical infrastructure owners in addressing cyber incidents and attacks, including those targeting ICS. The Pipeline and Hazardous Materials Safety Administration (PHMSA) within the Department of Transportation, meanwhile, is responsible for regulating the safety of hazardous materials transportation and the safety of pipeline systems.
The Department of Energy (DOE), which has traditionally been responsible for protecting electric power, oil, and natural gas delivery infrastructure, has also taken on a concerted cybersecurity role in December 2018 through its launch of the Office of Cybersecurity, Energy Security, and Emergency Response. The DOE, notably, is also spearheading a Trump-era initiative to limit bulk power system (BPS) equipment procurement from foreign adversaries as part of a broader measure that responds to energy system supply chain vulnerabilities.
FERC, NERC Have Repeatedly Called for Mandatory Natural Gas Pipeline StandardsFinally, FERC has regulatory authority over interstate natural gas pipelines as ordained by the Natural Gas Act of 1938, though it has no jurisdiction over pipeline safety or security. However, the independent DOE agency-which also regulates most of the nation's electricity sector-says it actively works with other agencies concerning pipeline safety and security. FERC also oversees the North American Electric Reliability Corp. (NERC), the federally designated U.S. Electric Reliability Organization, which has developed mandatory critical infrastructure protection standards for protecting electric utility-critical and cyber-critical assets. FERC and NERC, notably, have repeatedly underscored critical infrastructure interdependencies and urged more vigilance and action for natural gas pipeline security.
Just this week, NERC President and CEO Jim Robb pointed to extraordinary events over the past nine months, which included major weather events, supply chain compromises, and the Colonial pipeline cyberattack, suggesting that the reliability and security risk to the electricity system has seen a step-change increase." Robb has also pointedly called for gas industry regulators to establish cybersecurity standards that are comparable to NERC's reliability standards. During a May 13 board meeting, he urged policymakers to refocus on ensuring that gas infrastructure is as secure as the grid it supplies. This is not a jurisdictional play," he said, pointing to NERC's 2017 Special Assessment: Potential Bulk Power System Impacts Due to Severe Disruptions on the Natural Gas System. Rather, it underscores the need for foundational security standards for an industry that is critical to reliability and national security," he said.
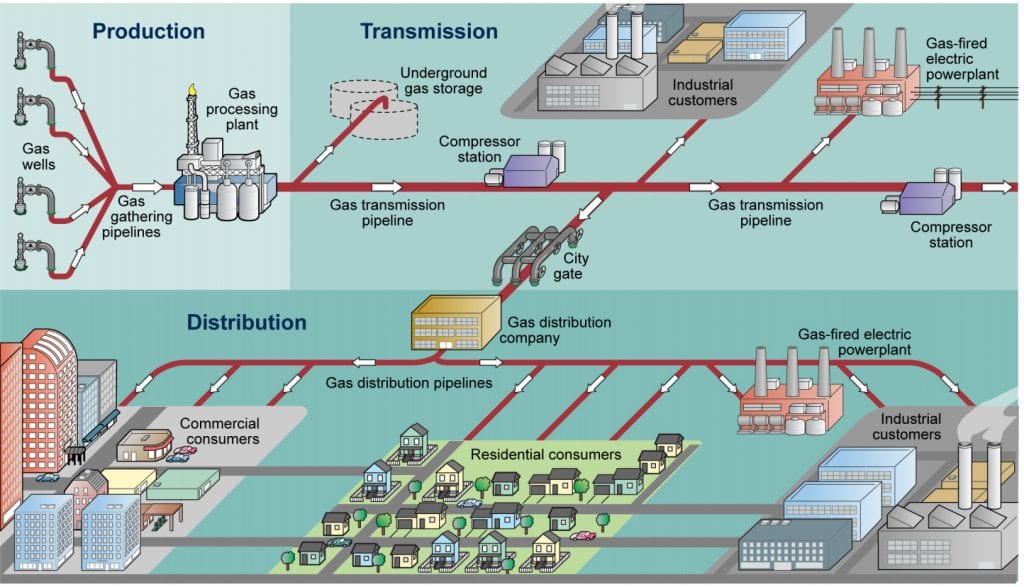 The natural gas supply chain is composed of three major sectors: production, transmission, and distribution. According to the Energy Information Administration, in 2020, 42% of the natural gas delivered by transmission and distribution pipelines went to power plants, 30% to industrial plants, 17% to residential consumers, and 11% to commercial consumers. Almost 195,000 miles of transmission pipelines are interstate and are therefore subject to federal regulation. Another 2.2 million miles are low-pressure pipelines that distribute natural gas to residential and commercial consumers. Source: GAO
The natural gas supply chain is composed of three major sectors: production, transmission, and distribution. According to the Energy Information Administration, in 2020, 42% of the natural gas delivered by transmission and distribution pipelines went to power plants, 30% to industrial plants, 17% to residential consumers, and 11% to commercial consumers. Almost 195,000 miles of transmission pipelines are interstate and are therefore subject to federal regulation. Another 2.2 million miles are low-pressure pipelines that distribute natural gas to residential and commercial consumers. Source: GAO
John Moura, NERC's director of Reliability Assessment and Technical Committees, on Wednesday also highlighted natural gas-electric dependencies when discussing the entity's dismal predictions for BPS reliability this summer. NERC's assessment warns of potential energy shortfalls during extreme conditions in California, as well as in Texas, New England, and the Midwest.
FERC Chairman Richard Glick has also strongly advocated mandatory cyber standards for pipelines. In a 2018 op-ed, Glick and Commissioner Neil Chatterjee (then FERC's chairman) jointly urged Congress to vest the responsibility for pipeline security with FERC, which they said fully comprehends the nation's energy sector and has sufficient resources to address the growing cybersecurity threat to gas pipelines."
In the wake of the Colonial Pipeline incident, Glick (and Commissioner Allison Clements) renewed that call, underscoring a need for mandatory pipeline cybersecurity standards similar to those applicable to the electricity sector." Glick noted: Simply encouraging pipelines to voluntarily adopt best practices is an inadequate response to the ever-increasing number and sophistication of malevolent cyber actors. Mandatory pipeline security standards are necessary to protect the infrastructure on which we all depend."
Energy Consumers Want FERC Mandate AuthorityAt least one group, the Industrial Energy Consumers of America (IECA), is actively lobbying Congress to give FERC federal reliability oversight over natural gas pipelines, as well as the mandate authority to issue standards for pipeline physical and cybersecurity requirements.
IECA describes itself as the only national cross-industry trade association that is dedicated to the manufacturing sector's interests. Its membership comprises firms that are major energy, power, and feedstock consumers, hailing from the chemicals, plastics, steel, iron ore, aluminum, paper, food processing, fertilizer, insulation, glass, industrial gases, pharmaceutical, building products, automotive, brewing, independent oil refining, and cement industries.
In a May 19 letter to U.S. Senate and House leaders, IECA President and CEO Paul Cicio noted pipeline security requirements under the TSA are voluntary," not mandatory. Unlike electricity, there are no mandatory standards and there is only very limited federal oversight of natural gas pipeline reliability," he wrote. Our nation cannot have electricity reliability without a secure and reliable supply of natural gas." The Colonial Pipeline attack, along with recent energy reliability debacles in Texas and California should be a wake-up call for Congress to take action," he said.
FERC is suited to provide reliability oversight and the mandate authority to issue cyber and physical standards because it meets at the intersection of natural gas and electricity markets that are dependent upon one another," Cicio said.
Establishing FERC oversight is also timely, given that the natural gas market is undergoing change due to significant growth in [liquefied natural gas (LNG)] and pipeline exports that can threaten reliability during peak winter and summer demand, and the shift to renewable energy." To date, more than 43% of 2020 U.S. natural gas production has been approved for export to 2050, he said, citing the Energy Information Administration. This is on top of pipeline exports equal to 8.6% of production. Projects that are proposed and in pre-filing equal another 9.3% of 2020 production." So far, no federal agency has the responsibility to ensure that there is adequate pipeline capacity at peak demand. In fact, no federal agency has the responsibility to monitor at what rate pipelines are operating to determine whether there is sufficient capacity," he wrote.
LNG exporters have locked-up firm pipeline capacity to ensure that gas flows to export facilities. Their highest demand is in the winter. No one knows how much capacity is available to supply power generation, homeowners, and manufacturers at peak demand."
Cicio acknowledged implementation of mandatory physical and security requirements could increase costs for natural gas consumers. However, one successful attack could shut down tens of thousands of manufacturing facilities and cost tens of millions of dollars per day for each facility," he said. The economic harm could be staggering."
-Sonal Patelis a POWER senior associate editor (@sonalcpatel,@POWERmagazine).
The post DHS Issues Pipeline Cybersecurity Directive but Industry Championing FERC Mandatory Standards appeared first on POWER Magazine.