Not sure what two-factor authentication is? We're here to help
What 2FA is, why it's important, and why you should use it.
You see a lot of talk on the internet about two-factor authentication (or 2FA as it's commonly called), and most of the time, you just see people like us telling you to use it.
We'll continue that trend and start this guide by telling you to use 2FA whenever and wherever you can. However, we're also going to let you know what it is and why you must use it. Ready to learn more? Read on.
Lock it downYubico Yubikey 5 NFCKeep your accounts extra safe with a physical 2FA key
Everyone should be using two-factor authentication (yes, you!), and one of the best ways to start is with the Yubico Security Key. This USB key fits in any USB-A port and securely saves 2FA login codes for your Google, Facebook, Dropbox, and other online accounts. It's also extremely durable and can be attached to a key ring for easy transportation.
Jump to:- Understanding two-factor authentication
- It starts with your passwords
- 2FA is incredibly secure
- It's easy to get started with 2FA
- What is the best 2FA method?
- Why this is so important
To put it in simple terms, two-factor authentication (2FA) means that you need to present two different things from two different sources that prove who you are. Generally, three different ID types can be used for 2FA purposes when it comes to online accounts:
- A thing that only you should know. A password, PIN, account number, your street address, or even the last four digits of your Social Security number fit the bill here.
- A thing that you can hold in your hands. This means your phone, an authenticator fob, or a USB security key.
- A thing that is part of you, like your fingerprint, retina pattern, or voice pattern.
When you have 2FA enabled on an account, you need two of these three things to get access.
You've been using 2FA all along and probably didn't realize it.
You've been using 2FA for most of your adult life. The companies who process credit card payments for online retailers usually force you to enter the three-digit code on the back of your credit card as well as the card number, then need you to provide the billing address. The numbers on the card (both front and back) are a way to make sure you have the card in your possession for the first method of authentication, then the address you provide has to match what the card issuer has on file as a second way to prove who you are. That's 2FA.
Back when the world still used checks to pay for things, most businesses wanted two forms of physical ID from a well-recognized place like your state DMV or school as a way to make sure you are the person whose name is on the top of the check. That's also 2FA. Plus, to get those IDs usually requires multiple things from different places to prove who you are.
Using 2FA for your online accounts is a little bit different but still uses the same principle - if you can provide more than one method to prove who you are, you probably are who you claim to be. For an account like Google, Facebook, or Amazon, you need to supply a password. Your password is something only you should know, but sometimes other people can get hold of it. When you add a 2FA requirement - like an authentication token sent to your phone or something like the Google Titan security key you plug into your computer - a password is no longer enough to get into your account. Without both pieces of authentication, you're locked out.
Do I still need a strong password if I use two-factor authentication?With all the various online services at your disposal, it's important to have a unique password for every single one of them. Duplicate passwords open you up to being potentially hacked in the event that someone gets ahold of one password and then tries to use it at different sites. It's impossible to keep all of your passwords stored in your memory, and that's where password managers come in.
The great thing is that password managers have evolved so much that many of them offer additional features that are not only useful but continue to keep your information confidential. For example, 1Password is currently our favorite password manager due to its ease of use. But the app can also act as a 2FA authenticator after everything has been set up. The code refreshes on a regular basis and is much more secure than relying on SMS messages for authentication.
Password managers are great tools for ensuring you have a lengthy and unique password for all of your online accounts, but a strong password isn't a good enough excuse to ignore two-factor authentication and not use it. Just about any password can be hacked if someone is persistent enough and has the right amount of computing power, but bypassing 2FA through a dedicated app or security key is virtually impossible unless you have access to that physical device.
As such, it goes both ways. Just because you use two-factor authentication doesn't mean you should disregard a strong password. Similarly, you still need to use two-factor authentication even though you have (what you think is) an un-hackable password.
Is two-factor authentication secure?Yes and no. Using 2FA on an account is a lot more secure than not using it, but nothing is perfectly secure. That scary thought aside, using 2FA is usually sufficient protection for your "stuff" unless you're a high-profile target or really unlucky.
Using 2FA is usually sufficient protection for your online accounts and services.
On the positive side, if you're using 2FA and some fake phishing email tricks you into supplying your password, they still can't log into your account. The way most people use 2FA for online accounts is to have a token sent to an app on their Android phones, and without that token, the email scammer isn't going to have any luck getting access. They will enter your account user name or ID, then the password, and then they need to supply that token to go any further. Unless they have your phone, the work involved in bypassing the second ID requirement is enough to get the bad guy to say "forget it!" and move to someone else.
On the other hand, if you're someone like the President or Mick Jagger, people are going to want to get into your accounts, and there are ways. The communication between the people supplying the authentication token and your phone is safe for the most part, so attackers go after the website or server asking for the credentials. Very clever folks can hijack auth tokens and cookies, and as soon as one method gets patched, they start looking for another. This takes a lot of knowledge and hard work, which means that the result has to be worth it all. Chances are you and I aren't worth the trouble, so 2FA is an excellent way to secure our accounts.
How do I use two-factor authentication?It's easier than you might think!
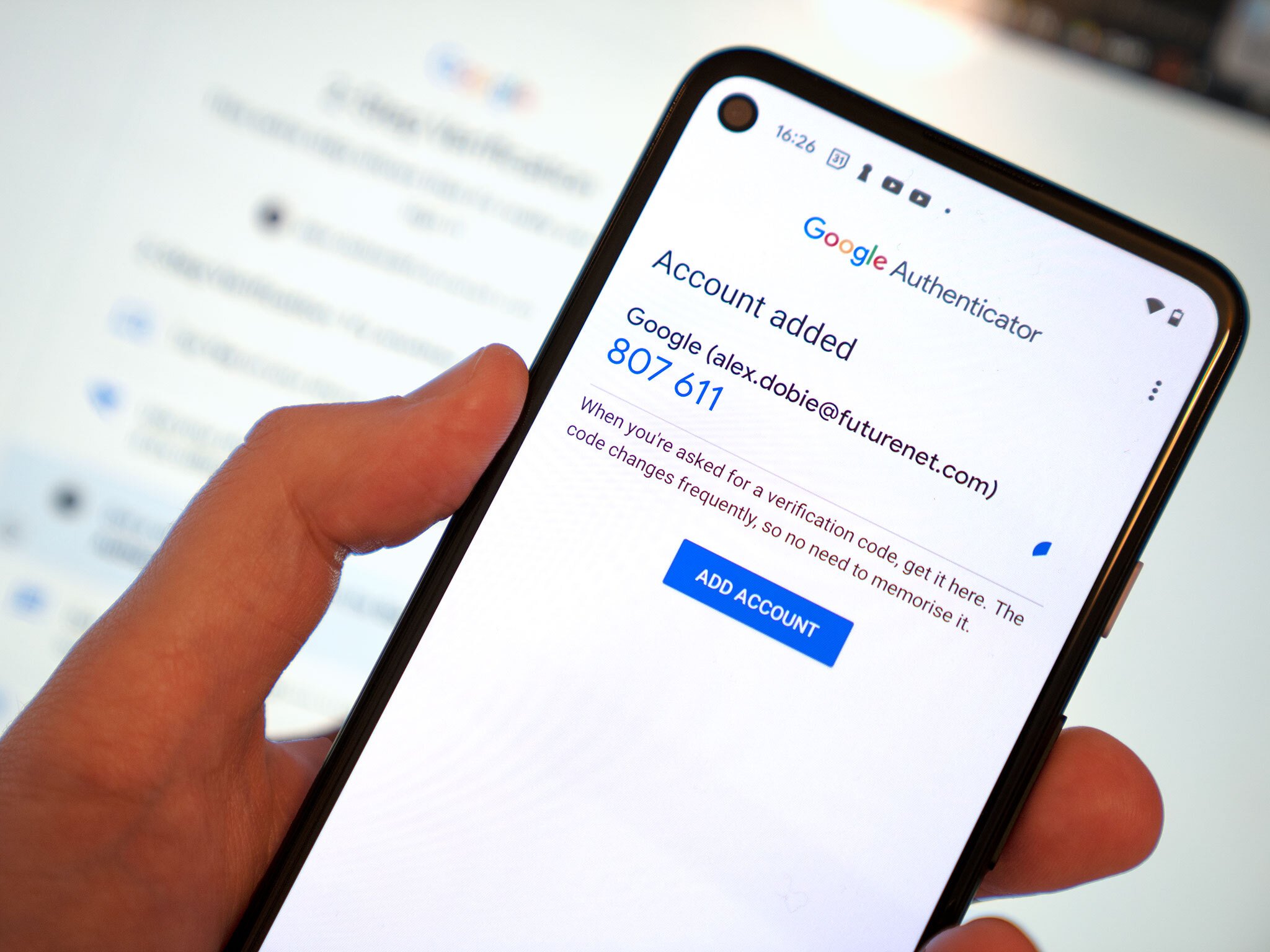
Setting up 2FA on an account is a three-step process. You need to provide your current credentials by typing in your password again (this helps keep someone else from adding it to your account), even if you're currently logged into the service. Then you go into the account settings and enable 2FA on your account. This lets the server know you want to enable it, and it'll ask what kind of authentication you will be using - most common are codes sent to your phone as an SMS message or through an authenticator application. Finally, you affirm the change by supplying a token back to the server. If you're using an app, this might be a barcode you have to scan or manually enter some information into the app. If you chose to use SMS, a code will be sent that you need to enter on the website to finish things up.
That last step happens when you want to log into that account again. You'll enter a username or ID, then a password, and then be asked to supply an authentication number. That number is sent as an SMS, for example, or in the app on your phone if you decided to go that route. You type that number into the text field, and that's it! You have access.
Most services will store an authentication token on your phone or computer, so you won't have to resupply the code the next time you want to log in. However, if you want to set up access from another place, you'll need a code. While the process is practically the same regardless of whether you're setting up 2FA on your Google account or just trying to keep your Amazon payments safe and secure, there are a few differences here and there.
Something else we hear about all of the time that various Twitter accounts end up getting hacked and those accounts start tweeting out some weird stuff. With a platform as large as Twitter, it's extremely important to make sure you have 2FA set up, along with changing your password regularly.
What is the best two-factor authentication method?Most popular apps default to SMS 2FA. You enter your login credentials, receive a text with a six-digit code, enter it into the box, and ask the site to remember your browser next time. Simple! But in a worst-case scenario, someone after your account can intercept an SMS message or convince a carrier that they're you and get your number assigned to their SIM card. However unlikely, SMS exploits leave your account more vulnerable than it should be.
Ranking the best 2FA methods, a U2F key is our favorite option but also the most inconvenient. A device like the Yubico Yubikey 5 or Titan Security Key sends a signed challenge code back to the server specific to the site, your account, and the device itself. Once connected to an account, no one can access it without the key; it's so ironclad that if you lose it, you'll never get into your account again. So you'll want to buy a backup, and two of these can get quite expensive.
A more expedient option is push-based 2FA, which Google and Apple use. Rather than send a text, you get a notification that you tap to receive the code. So long as you don't lose your phone (or any other device associated with the account), no one should be able to get your 2FA code. The only downside with this method is you need a wireless connection to receive the notification; cellular doesn't work.
Then you have authenticator apps, which generate time-based one-off passwords (TOTP) without an online connection. While more secure than SMS, phishers can still use your login and TOTP to access a website if you give it to them, so you have to tread more carefully and make sure the login page is legitimate.
Why is two-factor authentication so important?In a world that's constantly becoming more connected with new security and privacy issues popping up just about every day, it's important that everyone out there takes the necessary precautions to protect their online presence as much as possible.
Two-factor authentication is not 100% foolproof, but it adds a significant security layer that can keep unwanted eyes and hands off your data. And when you combine using a password manager with two-factor authentication, you have a better chance at thwarting anyone from getting ahold of those precious logins.
It might be annoying at first to deal with entering your 2FA codes when logging into your online accounts. Still, the extra couple of seconds this takes is well worth the added protection that two-factor authentication provides.
Lock it downYubico Yubikey 5 NFCKeep your accounts extra safe with a physical 2FA key
Everyone should be using two-factor authentication (yes, you!), and one of the best ways to start is with the Yubico Security Key. This USB key fits in any USB-A port and securely saves 2FA login codes for your Google, Facebook, Dropbox, and other online accounts. It's also extremely durable and can be attached to a key ring for easy transportation.