Distributed Renewables Cyber Resilience
The benefits of renewable energy continue to grow, with wind generation supplying 9.2% of generation in the U.S. and up to 22.6% in other western countries like Germany. Solar is at 2.8% in the U.S. (for utility-scale installations) and near 10% in Germany. Through diversification and greater distribution system integration, the application of renewable energy promises greater power system resilience from threats that include damaging storms and cyber-attack.
While renewable energy offers communities the ability to meet critical load demand, distributed systems can lift the resilience burden on transmission systems and large-scale generation suppliers to fulfill these needs. Diversification of generation assets can reduce the impact from individual threats, as disruptions from compromise are likely smaller in scale and less likely to affect all assets, specifically from cyber-attack. Looking to the future and potential impacts of climate change, distribution and diversification provide practical pathways for resilience and impact reduction.
However, the control systems necessary to integrate the distribution and diversification required to maintain power system stability expand the attack surface via more communications interfaces. As a result, the resilience to cyber-attack must be elevated to levels proportional to increasing threat levels in order to give owners and operators the reliability their mission demands. Advancing a reference architecture that enables secure design across all generation types, large and small scale, is critical to the future of distributed power system resilience. (See other proposals here: https://sunspec.org/wp-content/uploads/2020/01/EPRI-Security-Architecture-for-the-Distributed-Energy-Resources-Integration-Network.pdf.)
A Reference Architecture for Orchestrated ResponseThe application of secure technologies and applications will underpin next-generation resilient designs for energy applications, informed by research and development (R&D) work, and applied by industry. To inform a reference architecture design and R&D gaps for the renewables industry, a survey was conducted to evaluate the current state of the industry. The survey was sent to: cybersecurity vendors and original equipment manufacturers (OEMs) in solar energy, wind energy, and electric vehicle (EV) sectors.
A security architecture requires several elements, including:
- Detect. Monitoring of network traffic to recognize undesirable traffic.
- Analyze. Methods, including machine learning, to baseline normal traffic and recognize abnormal.
- Decide/Visualize. Presentation of information to cyber defenders for quick recognition and response.
- Mitigate/Recover. Methods to stop a cyber-attack and reverse any negative affects.
- Share. Providing of indicators of cyber-attack that can be securely shared and benefit the defenses of other organizations.
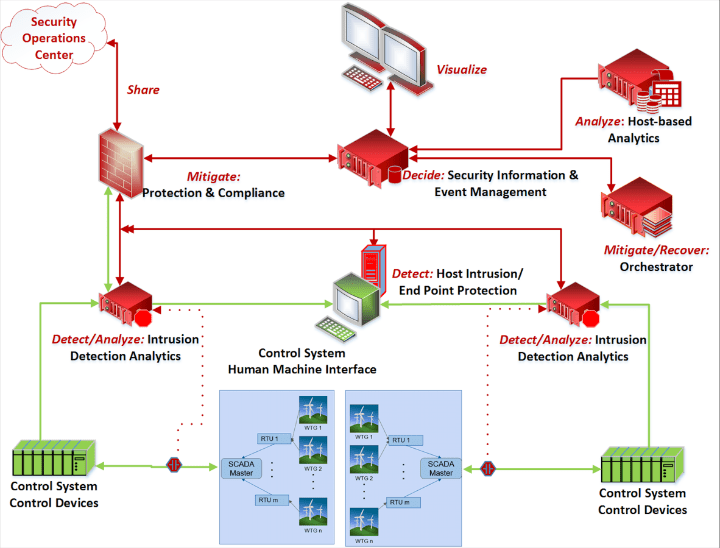
These security architecture element's functions are provided through the following security tools (Figure 1), noting that many of the tools provide multiple functions. (Also note that the proposed architecture is structurally agnostic and likely to be implemented in a hybrid manner. Energy resource data flow is no longer strictly hierarchical, thus functional security is essential regardless of alignment to traditional data hierarchies.):
- Detect, Analyze. Host/Network Intrusion Detection Systems (HIDS/NIDS).
- Decide/Visualize. Security Information and Event Management (SIEM).
- Mitigate/Recover. Security Orchestration, Automation, and Response (SOAR).
- Share. Structured Threat Information eXpression (STIX), Trusted Automated eXchange of Intelligence Information (TAXII).
 1. Reference architecture. Source: Idaho National Laboratory (INL)
1. Reference architecture. Source: Idaho National Laboratory (INL)Those surveyed were asked about their integration of said tools, and additionally, traditional access controls and encryption-provided perimeter defenses. The survey garnered insightful perspectives from both cybersecurity vendors and OEMs on the technologies listed. The full results can be found at: https://inlbox.app.box.com/s/oqy4x0r398fgd31of3ox53w00n36uuai.
As an example of the results analysis, Figure 2 provides a summary example for NIDS from cybersecurity vendors. Each table provides the company, product, renewables domains impacted, and common capabilities of each product. In addition, for each capability (using categories provided), it also shows how many respondents indicated the same capability support.
 2. Example survey results summary for the SIEM security technology. Source: INL
2. Example survey results summary for the SIEM security technology. Source: INLMany cybersecurity vendors responded to the survey, but only a limited number of OEM renewables vendors chose to (Figure 3). Evident from the cybersecurity vendors is the belief that their products may provide benefits in this domain. Less evident is a similar level of engagement on and enthusiasm for cybersecurity from the renewables industry OEMs.
 3. OEM survey of cybersecurity application. Source: INL
3. OEM survey of cybersecurity application. Source: INLClearly, more discussion on cybersecurity reference architectures is warranted, with more substantial industry participation. Specifically, a greater understanding of the tools, benefits, and costs of investment would be helpful. While large asset owners have integrated security, further discussion/evaluation is needed on the security of distributed renewables to ensure high-level protection and resilience is designed in. The resulting discussion should illuminate the need for decision-making tools that align benefits with investments. To achieve and maintain a common threat posture between large-scale utilities and renewables, integration of security capabilities that aggregate seamlessly is necessary.
Planning for a Cyber-Resilient Power SystemAn integrated security reference architecture will establish a resilient foundation for countering threats through, among other things, comprehensive real-time awareness. Building upon this foundation will include automated and autonomous responses, firing off in real time, and distributed mitigations to maintain operations of the system in spite of damaging storms and cyberattacks. Achieving comprehensive resilience for the nation's power system requires not only a high confidence correlation of mis-operation versus malicious attack, but also recognition that the power system lives in continuously contested space. In establishing distributed protection approaches, the ability to recognize/respond to threats localizes impact and prevents catastrophic loss. It also reduces the time to recognition and response, limiting the adversary's ability to compromise the power system.
As we look to advance, if not accelerate, the integration of distributed renewables, it is important to ensure that the appropriate, tailored cybersecurity approach is applied consistently across all interfaces to establish the secure reference architecture suggested. As we progress toward this goal, it is important to understand the positions and perspectives of industry. In so doing, a more precise understanding of where government investments are required can assist prioritization.
The survey presented in this article provides some of this perspective, but we would like to hear from additional industry representatives to ensure an accurate correlation of the need. To that end, please take a moment to complete a short Qualtrics industry survey. The results of the updated survey will be shared broadly with the renewables industry.
-Craig Rieger, PhD, PE is the Chief Control Systems Research Engineer and a directorate fellow at the INL; Jake Gentle is a senior power systems engineer at the INL, where he is the program manager for Infrastructure Security, supervisor of Secure Power Systems and Controls, and laboratory relationship manager to the U.S. Department of Energy's Wind Energy Technologies Office; Andy Bochman is senior grid strategist-Defender at the INL; and Jeremiah Miller is director of storage markets and policy with the Solar Energy Industries Association (SEIA).
The post Distributed Renewables Cyber Resilience appeared first on POWER Magazine.