Deep learning delivers proactive cyber defense
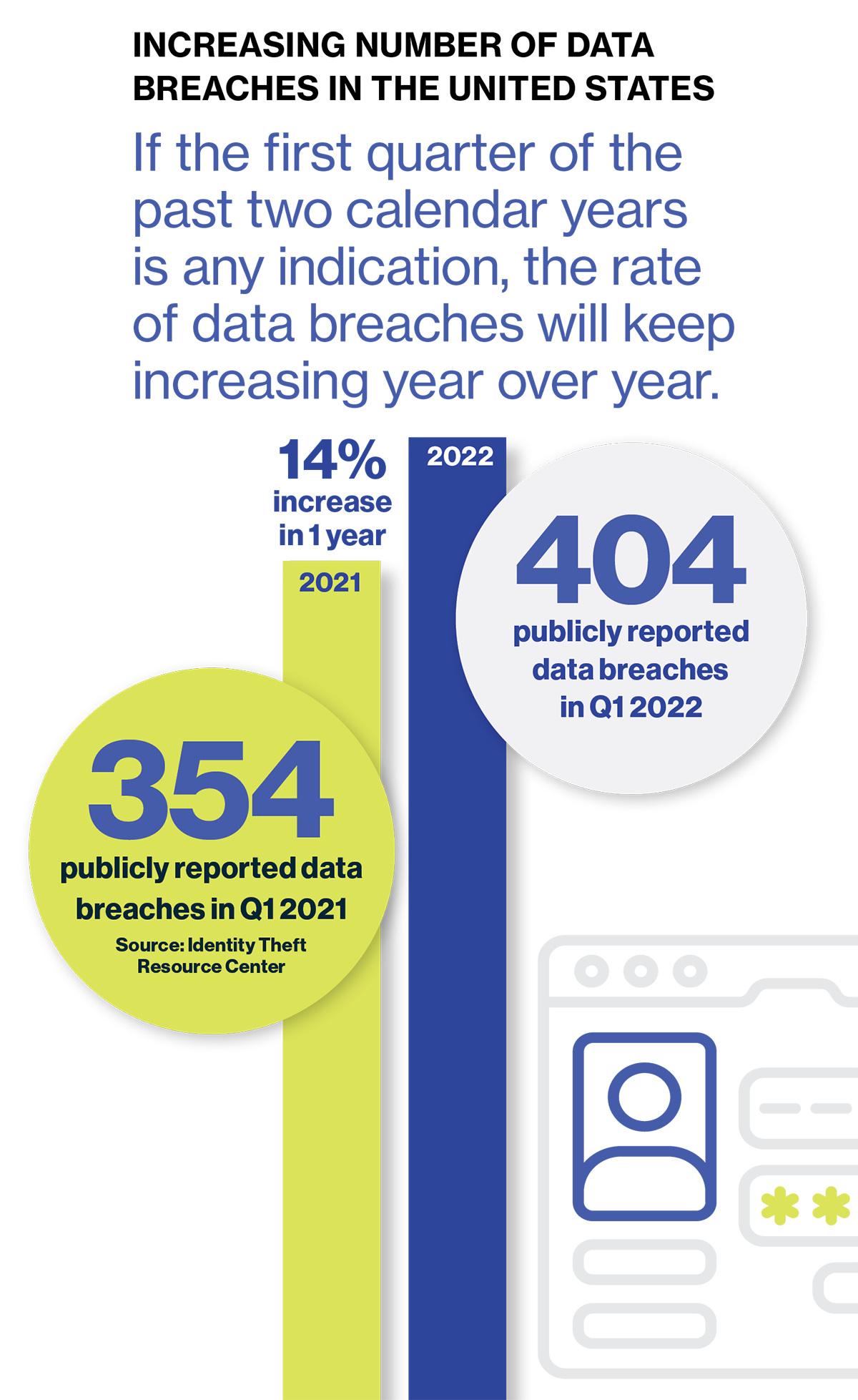
Cybersecurity professionals are constantly looking for new and innovative ways to stay one step ahead of attackers. Yet in the first quarter of 2022 alone, there were 404 publicly reported data breaches in the U.S.-a 14% increase compared to the first quarter of 2021, according to the Identity Theft Resource Center. Of particular concern is the alarming rise in ransomware breaches, which increased by 13% in a single year-representing a jump greater than the past five years combined, according to the 2022 Verizon Data Breach Investigations Report (DBIR).
No wonder an increasing number of organizations are beginning to explore how deep learning, and its ability to mimic the human brain, can outsmart and outpace the world's fastest and dangerous cyber threats.
The most advanced form of artificial intelligence (AI) technology, and a type of machine learning, deep learning uses neural networks to instinctively and autonomously anticipate and prevent unknown malware and zero-day attacks before they can wreak havoc on an IT environment.
Most cybersecurity technologies, such as endpoint detection and response (EDR) solutions, simply identify, track, record, and contain a threat once it has already entered an environment. Machine learning-based cybersecurity solutions are also an essential part of any security strategy, and use pre-labelled data, classified as either benign or malicious, to detect dangerous patterns.
But neither set of cybersecurity solutions can proactively defend against sophisticated attacks without constant human tweaking. Fortunately, deep learning can mimic the functionality and connectivity of neurons in the human brain, enabling neural networks to independently learn from raw and un-curated data and automatically recognize unknown threats.
Deep learning is the only family of algorithms that works on raw data to identify cybersecurity threats with unmatched speed and accuracy," says Guy Caspi, CEO of Deep Instinct, a cybersecurity company.
The result is a powerful solution that can accurately identify highly sophisticated attack patterns at record speeds.
Time for a different line of defenseAlthough deep learning has been around since the 1940s, the high cost and complexity of graphics processing units (GPUs) have kept the technology out of reach for many organizations. But that's changing with the increasing processing power and lower costs of graphics chips.
The timing couldn't be better. The increasing availability of ransomware-as-a-service offerings, such as ransomware kits and target lists, are making it easier than ever for bad actors-even those with limited experience-to launch a ransomware attack, causing crippling damage in the very first moments of infection. Other sophisticated attackers use targeted strikes, in which the ransomware is placed inside the network to trigger on command.
Another cause for concern is the increasing disappearance of an IT environment's perimeter as cloud compute storage and resources move to the edge. Today's organizations must secure endpoints or entry points of end-user devices, such as desktops, laptops, and mobile devices, from being exploited by malicious hackers-a challenging feat, according to Michael Suby, research vice president, security and trust, at IDC. Attacks continue to evolve, as do the endpoints themselves and the end users who utilize their devices," he says. These dynamic circumstances create a trifecta for bad actors to enter and establish a presence on any endpoint and use that endpoint to stage an attack sequence."
The increased pace of high-profile threats (e.g., ransomware) is up to double-digit (15.8%) growth. The result is a dangerous path most likely to lead to continued losses for organizations that fall victim to a cyberattack without any gains in defensive powers. Indeed, a 2021 data breach report by IBM and the Ponemon Institute reveals that the average cost of a data breach is $4.24 million.
Beyond costs, a cyberattack can cause irreparable damage to a company's brand, share price, and day-to-day operations. According to a recent Deloitte survey, 32% of respondents cited operational disruption as the biggest impact of a cyber incident or breach. Other repercussions cited by surveyed companies include intellectual property theft (22%), a drop in share price (19%), reputational loss (17%), and a loss of customer trust (17%).
Given these significant risks, organizations simply can't afford to accept the status quo on protecting digital assets. If we are to ever get ahead of our adversaries, the world needs to change the mindset from detection to one of prevention," says Caspi. Organizations need to change the way they perform security and combat hackers."
 Deep learning can be the difference
Deep learning can be the differenceUp until now, many cybersecurity experts have viewed machine learning as the most innovative approach to safeguarding digital assets. But deep learning is ideally suited to change the way we prevent cybersecurity attacks. Any machine learning tool can be understood, and theoretically reverse engineered to introduce a bias or vulnerability that will weaken its defenses against an attack. Bad actors can also use their own machine learning algorithms to pollute a defensive solution with false data sets.
Fortunately, deep learning addresses the limitations of machine learning by circumventing the need for highly skilled and experienced data scientists to manually feed a solution data set. Rather, a deep learning model, specifically developed for cybersecurity, can absorb and process vast volumes of raw data to fully train the system. These neural networks become autonomous, once trained, and do not require constant human intervention. This combination of a raw data-based learning methodology and larger data sets means that deep learning is eventually able to accurately identify much more complex patterns than machine learning, at far faster speeds.
Deep learning outshines any deny list, heuristic-based, or standard machine learning approach," says Mirel Sehic, vice president general manager for Honeywell Building Technologies (HBT), a multinational corporation and provider of aerospace, performance materials, and safety and productivity technologies. The time it takes for a deep learning-based approach to detect a specific threat is much quicker than any of those elements combined."
This content was produced by Insights, the custom content arm of MIT Technology Review. It was not written by MIT Technology Review's editorial staff.