DROWN attack breaks TLS wide open using SSLv2
by from Techreport on (#15N45)
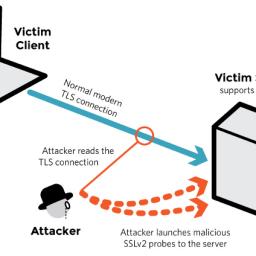
An international group of researchers has discovered that web traffic encrypted with Transport Layer Security (TLS) can be decrypted if a server also supports the antiquated SSLv2 cryptographic protocol. The researchers estimate that a staggering 33% of HTTPS-enabled sites are vulnerable to this attack, which they call DROWN, for Decrypting RSA using Obsolete and Weakened eNcryption.
While the SSLv2 protocol has long been known to be weak , the attack is significant because traffic encrypted with the stronger TLS protocol is potentially vulnerable. Communication from a client-like a web browser or mail transfer agent-that insists on TLS encryption may still be subject ...