Intrusion-Tolerant SCADA Demonstrated at Power Plant
Researchers have successfully demonstrated an open-source supervisory control and data acquisition (SCADA) system designed to withstand attacks and compromises on the power grid. The intrusion-tolerant system-called "Spire"-keeps power flowing even if part of the system is compromised, and it may be a breakthrough for grid resiliency, industry observers said.
Spire was built from the ground up with all open-source components by Yair Amir, professor and chair of the Department of Computer Science at Johns Hopkins University, PhD students Amy Babay and Tom Tantillo, and undergraduate student Trevor Aron, with funding from the U.S. Department of Defense. Project documents show that the system was developed to counter SCADA security concerns, which have mounted as systems move from specialized networks to IP networks. SCADA systems are also more vulnerable to malware like STUXNET, a virus used by sophisticated attackers to target an Iranian SCADA system in 2010.
According to its developers, the event-based SCADA system essentially comprises a SCADA master and a programmable logic controller (PLC)/remote terminal unit (RTU) proxy designed from scratch to support intrusion intolerance, as well as two human-machine interfaces (HMIs) based on an open-source SCADA software solution (pvbrowser). The SCADA master is replicated using Prime, a Byzantine fault-tolerant replication engine that the researchers also developed. The system runs over a Spines intrusion-tolerant messaging system.
"The Spire PLC/RTU proxy can interact with any devices that use the Modbus or DNP3 communication protocols over IP. We use OpenPLC to emulate PLCs that can be monitored and controlled by the system," the team said.
Experimental HackingThe developers tested the system in a 12-day-long experiment in April 2017 at Pacific Northwest National Labs, backed by network and software engineering firm Resurgo The experiment essentially compared a NIST-compliant SCADA architecture with Spire. Each system was attacked by a hacker team from Sandia National Laboratories.
Sandia's so-called "red team" was able to remotely obliterate the NIST-compliant simulated commercial grid control system within a couple of hours (via direct access to PLC from an operational network). However, it could not penetrate the Spire system for three days, despite attacks on the corporate and operational network-and even when given complete access to a replica and code. "On the third day, the Sandia attack team was given remote access to part of Spire, but still its test hackers could not disrupt the system's overall operations," says a news release from Johns Hopkins University.
In January, the developers tested the system again, this time at a mothballed Hawaiian Electric Company (HECO) power plant in Honolulu, which has a fully functional control system. Over two weeks, the team tested the Spire system on the power plant's equipment with the help of HECO engineers Keith Webster and John Tica. "After a few days of setup and integration, Spire ran continuously without interruption for almost a full week," the university said.
Using a device deployed to measure end-to-end reaction times of the commercial control system at the HECO plant as well as the Spire one, the researchers determined that the commercial system reflected a change in the grid's power state within 900 milliseconds to 1 second. Spire showed the same change within 400 to 500 milliseconds-within the timespan a power grid needs to respond to adverse events.
A System of ReplicasAccording to Amir, the system works with the help of replicas. The researchers built it to contain six copies of the main control server that work together to agree on updates in the system. That's the smallest number of replicas needed to get good protection, he said.
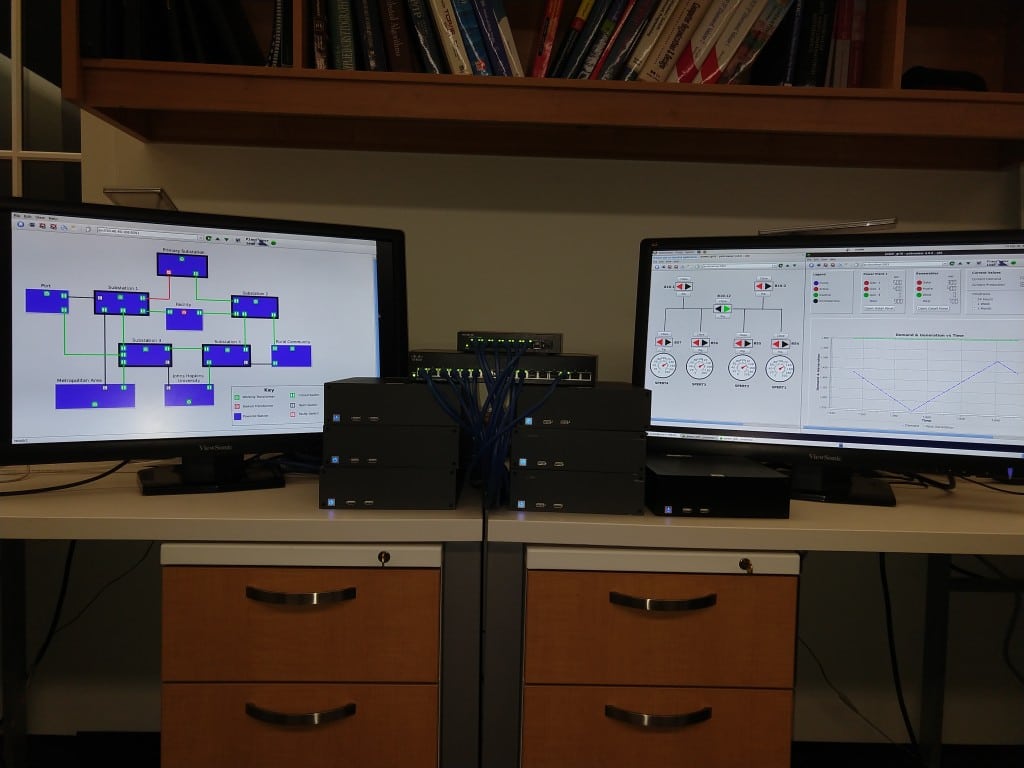
The Spire system in action. Each of the six computers in the center runs a SCADA Master replica, a Prime daemon, and two Spines daemons. The monitors show three HMIs. One switch connects the replicas to the HMI and a PLC proxy (not shown), while the other is exclusively for communication among the six replicas. Courtesy: John Hopkins University
"Each replica votes on every data and decision," he added. "If one of the replicas is compromised and another is going through maintenance, then the other good replicas will enable the system to continue working properly and in a timely manner."
The researchers plan to release Spire 1.1-the version tested at the HECO plant-within the coming weeks. Version 1.0, tested in April, is already available for download.
"We decided that we won't just publish our results, but we will release open-source solutions that will show people how to make control systems for the power grid secure, resilient, and intrusion-tolerant," Amir said. "We want to create a community of people who are really interested in that. We need to protect our critical infrastructure."
Promising but Still ChallengedCybersecurity experts that POWER talked to about the system expressed optimism at the concept. Phil Neray, vice president of Industrial Cybersecurity for Boston-based CyberX, said that the initiative looked promising for enhancing grid resiliency by adding new types of HMIs and other SCADA components.
"The challenge will be the speed at which these new components can be added to our existing network infrastructures, which still contain legacy 'insecure-by-design' components that were designed 10+ years ago," he said.
"In the interim, forward-thinking asset owners are adding compensating controls to their ICS/SCADA networks such as continuous monitoring and vulnerability management systems. These controls are non-intrusive and require no changes to existing networks, while reducing the risk of targeted attacks, malware, and insider threats."
-Sonal Patel is a POWER associate editor (@sonalcpatel, @POWERmagazine)
The post Intrusion-Tolerant SCADA Demonstrated at Power Plant appeared first on POWER Magazine.