Shutdown: Dot-gov websites vulnerable to cyberattacks, certificates expiring amid funding pause
Federal workers went without their paychecks Friday, as Trump's shutdown of the U.S. government continues for 21 days and counting. With no end in sight, concerns are rising that dozens of U.S. government websites have become insecure or completely unreachable, as their transport layer security (TLS) certificates expire.
A Thursday report from Netcraft estimates that the .gov websites are using 80 or more expired TLS certificates.
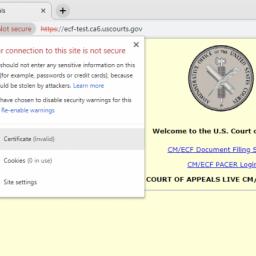
Sites like NASA, the U.S. Department of Justice, and the Court of Appeals are affected.
Funding to renew the certificates is on hold while the shutdown continues.
Any of the government websites with an expired cert becomes newly vulnerable to any number of internet-based assaults, including man-in the-middle (MITM) attacks that enable third-party bad guys to intercept what passes between an internet user and a web application on the affected site. Bad guys can eavesdrop on traffic, assume the identity of the government website, and siphon off data input by the user.
What kind of data? Maybe your name, your social security or tax ID number, a whole lot of people are going to be poking around on IRS dot gov this month. This could get bad.
From Netcraft:
With around 400,000 federal employees currently furloughed, more than 80 TLS certificates used by .gov websites have so far expired without being renewed. To compound the situation, some of these abandoned websites can no longer be accessed due to strict security measures that were implemented long before the shutdown started.
One such example is https://ows2.usdoj.gov, a U.S. Department of Justice website which uses a certificate that expired in the week leading up the shutdown. The certificate has been signed by a trusted certificate authority, GoDaddy, but it has not been renewed since it expired on 17 December 2018.
In a twist of fate, the usdoj.gov domain - and all of its subdomains - are included in Chromium's HSTS preload list.
This is a prudent security measure which forces modern browsers to only use secure, encrypted protocols when accessing the U.S. DoJ websites; however, it will also prevent users from visiting the HTTPS sites when an expired certificate is encountered. In these cases, modern browsers like Google Chrome and Mozilla Firefox deliberately hide the advanced option that would let the user bypass the warning and continue through to the site.
While this behaviour is bound to frustrate some users, in this case, security is arguably better than usability when you can't have both. If users were to ignore such warnings, they would be vulnerable to the type of man-in-the-middle attacks that TLS certificates were intended to combat.
Security before accessibility. But it sure would be nice to have both again.
"With Donald Trump seemingly unwilling to compromise on his demands for a wall along the border with Mexico, and Democrats refusing to approve a budget containing $5.7B for the wall, the hundreds of thousands of unpaid federal employees might not be the only ones hurting," said Netcraft. "As more and more certificates used by government websites inevitably expire over the following days, weeks - or maybe even months - there could be some realistic opportunities to undermine the security of all U.S. citizens."
[via ThreatPost]
IMAGE: The DigiCert certificate used by this U.S. Court of Appeals website expired on 5 January 2019 and has not yet been renewed. The site provides links to a document filing system and PACER (Public Access to Court Electronic Records).