Zombie POODLE and GOLDENDOODLE Vulnerabilities
Recently new vulnerabilities like Zombie POODLE, GOLDENDOODLE, 0-Length OpenSSL and Sleeping POODLE were published for websites that use CBC (Cipher Block Chaining) block cipher modes. These vulnerabilities are applicable only if the server uses TLS 1.2 or TLS 1.1 or TLS 1.0 with CBC cipher modes.
Update May 30, 2019: The grade change described below is now live on https://www.ssllabs.com/
SSL Labs identifies cipher suites using CBC with orange color and with text WEAK. This change won't have any effect on the grades, as it only means that SSL Labs discourages the use of CBC-based cipher suites further.
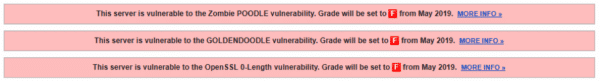
SSL Labs will start giving F" grade to the server affected by these vulnerabilities from end of May 2019. For now, SSL Labs will give only a warning for affected servers:
- Zombie POODLE (Invalid padding with valid MAC)
- GOLDENDOODLE (Valid padding with an invalid MAC)
- 0-Length OpenSSL (Invalid Mac/Valid Pad, 0-length record)
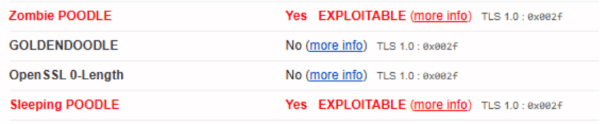
- Sleeping POODLE (invalid padding with valid MAC)

 Limitation in SSL Labs Detections
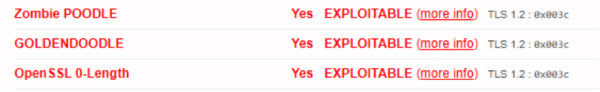
Limitation in SSL Labs Detections- These tests are specific to protocol/cipher suite, SSL Labs only checks with preferred Protocol and CBC Cipher suite. There is a probability that the server could be vulnerable with other set of protocol/cipher suite.
- SSL Labs only checks with a limited set of CBC cipher suite
- Zombie POODLE
- GOLDENDOODLE
- 0-Length OpenSSL
- Black Hat presentation by researcher
- TLS CBC Padding Oracles in 2019
Update April 26, 2019: The warning is live on https://dev.ssllabs.com/ and https://www.ssllabs.com/. As stated above, the grade change will be live by the end of May.