Group sex dating app has "the worst security for any dating app"
One of the wonderful and terrible things about the internet is how it allows people seeking others with hard-to-find traits to find them: advertisers can find people thinking about buying a refrigerator; people who think they might be trans can find others in the same boat and make common cause; people with the same rare disease can form support groups, and Nazis can find sociopaths to march through the streets of Charlottesville carrying tiki torches and chanting "Jews will not replace us."
This has been especially pronounced in human sexuality. Anonymous access to porn lets people explore different sexual activities. Online dating services lets people find those who share their kinks, interests, or special needs.
Enter 3fun, an online dating service for those seeking group sex with others. While there is nothing wrong with this activity, and while it's one that dates back to antiquity and probably before, there is still substantial social stigma associated with it, so apps are a great way of finding partners without exposing yourself to retaliation from employers, family, peers and friends.
That is, unless 3fun is designed with security as an afterthought in a way that exposes its users to snoops who could use the data it leaks to harass, blackmail, or expose its users.
Guess what!
Pen Test Partners's audit of 3fun revealed "probably the worst security for any dating app we've ever seen."
The audit revealed vulnerabilities that would allow attackers to enumerate all 3fun users, including sexual orientation, preferred matches, usernames, ages, partners' usernames, full-rez profile photos, and some dates of birth. None of the data is encrypted.
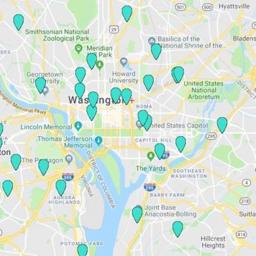
Attackers could extract users by location, and Pen Test Partners were able to locate 3fun users inside the White House, CIA headquarters, and the Pentagon.
Pen Test Partners notified 3fun of the defect on July 1, but it was not remediated for "weeks."
In its report, Pen Test Partners notes that it has only scratched the surface of the defects in 3fun's security, and speculates that there could be more (and even graver) defects in the system.
3fun claims 1,500,000 users, quoting 'top cities' as New York, Los Angeles, Chicago, Houston, Phoenix, San Antonio, San Diego, Philadelphia, Dallas, San Jose, San Francisco, Las Vegas & Washington, D. C.
Several dating apps including grindr have had user location disclosure issues before, through what is known as 'trilateration'. This is where one takes advantage of the 'distance from me' feature in an app and fools it. By spoofing your GPS position and looking at the distances from the user, we get an exact position.
But, 3fun is different. It just 'leaks' your position to the mobile app. It's a whole order of magnitude less secure.
Group sex app leaks locations, pics and personal details. Identifies users in White House and Supreme Court [Pen Test Partners]
Threesome app 3fun exposed user locations and profile data [Zack Whittaker/Techcrunch]