Popular app Snaptube caught serving invisible ads and charging users for premium purchases they haven’t made
A popular video downloader app for Android has been found generating fake ad clicks and unauthorized premium purchases from its users, according to a security firm.
Snaptube, which boasts some 40 million users, allows users to download videos and music from YouTube, Facebook, and other major video sites. The app, developed in China, is not on Google Play because the app maker claims Google will not allow video downloader apps on the store. Some third-party app stores estimate Snaptube has been downloaded over a billion times to date. The app's developer says that the app is "safe" to use.
But researchers at London-based security firm Upstream, which shared its findings exclusively with TechCrunch, said the free app ends up costing consumers.
Upstream's chief executive Guy Krief said users are served invisible ads without their knowledge that run silently on the device, allowing the app maker to generate ad revenue at the expense of churning up a user's mobile data and battery power. The app also uses the same background click technique to rack up premium purchases charges that the user never asked for.
Krief said the only indication that a user's device might be used in this way is if their mobile data usage increases, their device gets warm, and the battery runs out faster than usual.
The company pinned the blame on a third-party software development kit (SDK) code, known as Mango, embedded inside Snaptube's app. Mango was also used in Vidmate, a similar video downloader app also accused of ad fraud behavior; as well as 4shared, a cloud storage app.
According to Uptream, this third-party code kit downloads additional components from a central server in order to engage in this fraudulent ad activity, and uses chains of redirection and obfuscation to hide its activity.
Mango is particularly sneaky, said Krief. Within hours of the news breaking that Vidmate's app was engaged in similar suspicious behavior, his company saw a Snaptube's suspicious activity drop almost immediately. "Our assumption back then was they're probably also using similar code and they went silent because of all the publicity," he said in a phone call.
Two months later, the same suspicious activity in Snaptube's app resumed.
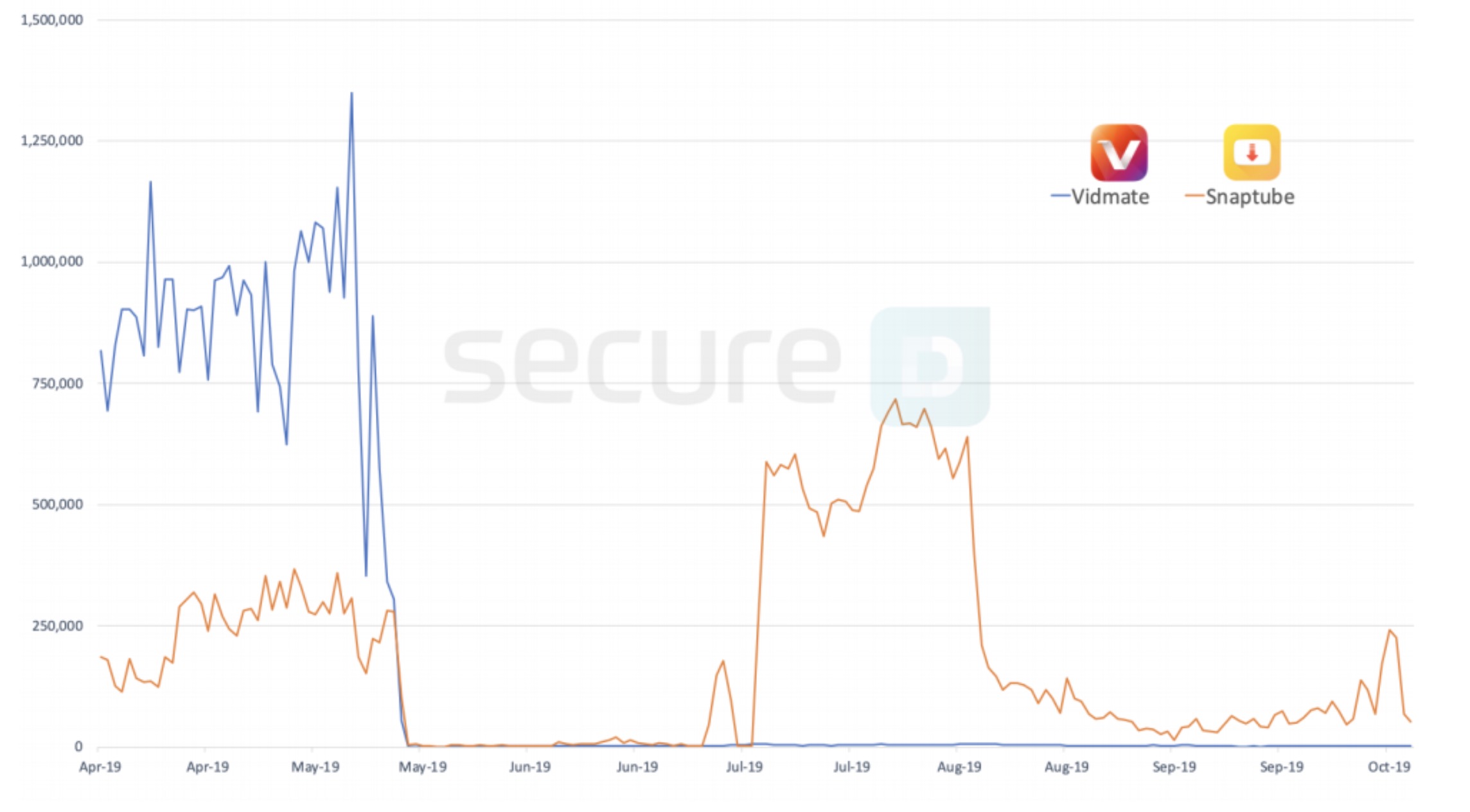
A graph showing Snaptube's suspicious activity dropping as soon as the Vidmate story is published. (Image: Upstream)
Krief said it was "very common" to see apps engaging in ad fraud to go through bursts of high levels of activity, followed by periods of quiet.
In recent weeks Upstream said it's blocked more than 70 million suspicious transactions originating from four million devices, according to data from its proprietary security platform. The company said consumers could have been charged tens of millions of dollars in unwanted premium charges had those clicks not been blocked.
Snaptube said in a statement: "We didn't realize the Mango SDK was exercising advertising fraud activities, which brought us major loss in brand reputation."
"After the user complained about the malicious behavior of the Mango SDK, we quickly responded and terminated all cooperations with them," a spokesperson said. "The versions on our official site as well as our maintained distribution channels are free of this issue already."
Snaptube said it was "considering" legal action against the Mango developers.
It's not the first time Snaptube has been caught out engaging in potentially fraudulent activity. In February, security firm Sophos found the app engaging in similar fraudulent behavior - generating and reporting fake ad clicks and racking up costs for the user. Later in the year, Snaptube responded to reports that Android devices were warning users that the app contained the suspicious third-party code, noting that it would "terminate" using the code "as soon as possible."
That promise was made in August. Yet, some three months later, the code remains in the app.
File-storage app 4shared caught serving invisible ads and making purchases without consent