Social media boosting service exposed thousands of Instagram passwords
A social media boosting startup, which bills itself as a service to increase a user's Instagram followers, has exposed thousands of Instagram account passwords.
The company, Social Captain, says it helps thousands of users to grow their Instagram follower counts by connecting their accounts to its platform. Users are asked to enter their Instagram username and password into the platform to get started.
But TechCrunch learned this week Social Captain was storing the passwords of linked Instagram accounts in unencrypted plaintext. Any user who viewed the web page source code on their Social Captain profile page could see their Instagram username and password in plain sight, so long as they had connected their account to the platform.
Making matters worse, a website bug allowed anyone access to any Social Captain user's profile without having to log in - simply plugging in a user's unique account ID into the company's web address would grant access to their Social Captain account - and their Instagram login credentials.
Because the user account IDs were for the most part sequential, it was possible to access any user's account and view their Instagram password and other account information with relative ease.
A security researcher, who asked not to be named, alerted TechCrunch to the vulnerability and provided a spreadsheet of about 10,000 scraped user accounts. (A recent court ruling found that scraping websites does not fall afoul of U.S. computer hacking laws.) The spreadsheet contained about 4,700 complete sets of Instagram usernames and passwords. The rest of the records contained just the user's name and their email address.
The data also showed if the accounts were free trial or paid premium accounts. Only about 70 accounts were paying customers, the data said, but many of those premium accounts also contained the customer's billing addresses.
We verified the bug by creating a dummy Instagram account and connecting it to a new Social Captain account, and viewing the web page source code of our profile page on Social Captain.
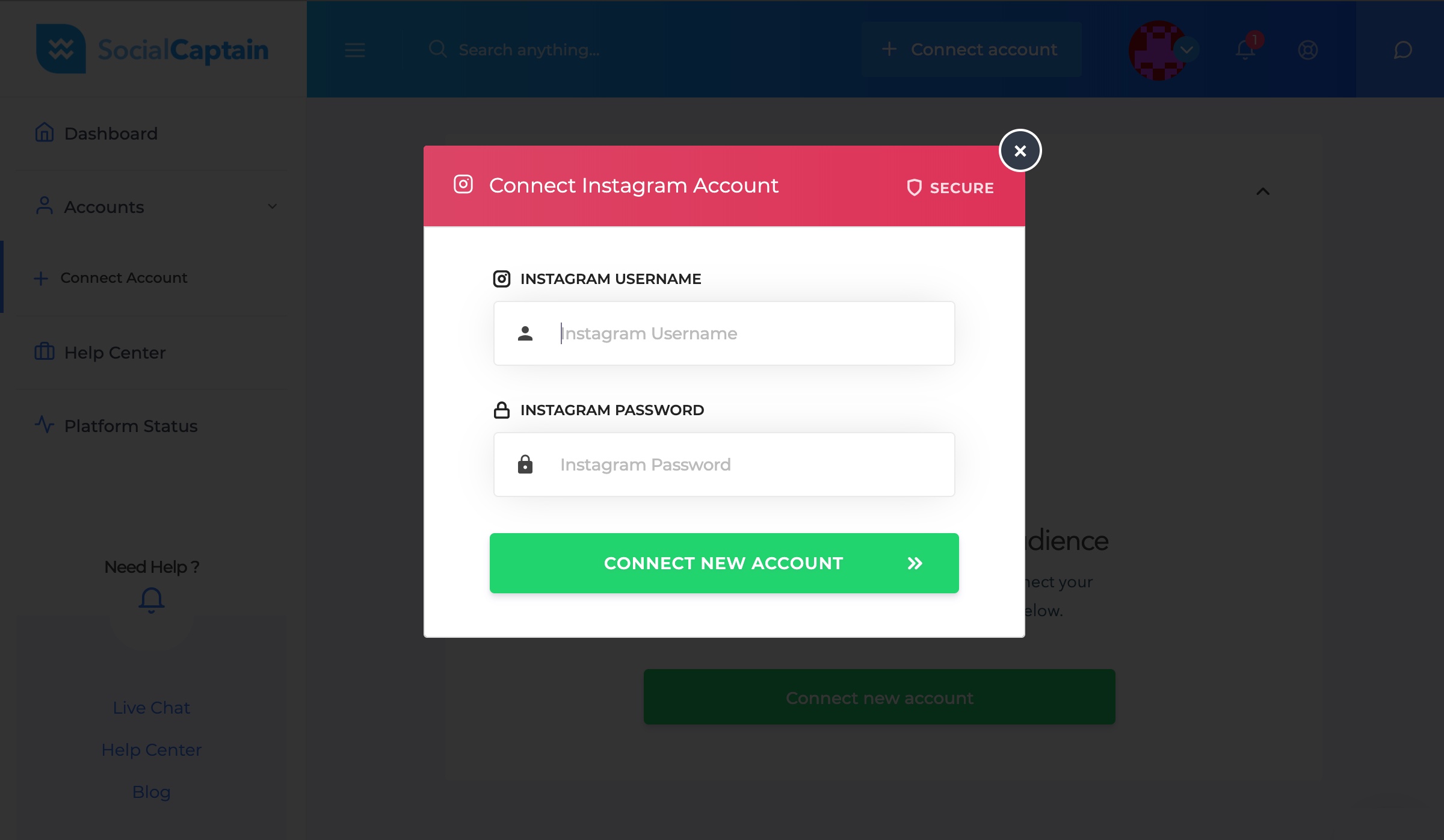
Users were asked to connect their Instagram accounts to the service by entering their username and password. Despite the claim it was "secure," passwords were collected and stored in plaintext. (Image: TechCrunch)
After TechCrunch reached out, Social Captain confirmed it had fixed the vulnerability by preventing direct access to other users' profiles.
But passwords and other account information are still visible in the web page source code of a user's profile page.
"Early analysis indicates that the issue was introduced during the past weeks when the endpoint, meant to facilitate integration with a third-party email service, has been temporarily made accessible without token-based authentication," said Anthony Rogers, chief executive at Social Captain.
"As soon as we finalize the internal investigation we will be alerting users that could have been affected in the event of a breach and prompt them to update the associated username and password combinations," he said.
Rogers did not say how long that investigation would take.
Instagram said the service breached its terms of service by improperly storing login credentials.
"We are investigating and will take appropriate action. We strongly encourage people to never give their passwords to someone they don't know or trust," said an Instagram spokesperson.
Users who signed up to Social Captain should change their Instagram passwords immediately.
It's the latest security incident to hit Instagram users, even if the Facebook -owned social media giant was not directly culpable for the lapse. Last year, Instagram expanded its bug bounty to include misuse of account data just months after an Indian social media firm scraped the contact information of Instagram influencers on a massive scale. Instagram also last year cut off a trusted ad partner for secretly collecting and storing the locations and other data on millions of users.
Instagram kills off fake followers, threatens accounts that keep using apps to get them