A new Android bug, Strandhogg 2.0, lets malware pose as real apps and steal user data
Security researchers have found a major vulnerability in almost every version of Android, which lets malware imitate legitimate apps to steal app passwords and other sensitive data.
The vulnerability, dubbed Strandhogg 2.0 (named after the Norse term for a hostile takeover) affects all devices running Android 9.0 and earlier. It's the evil twin" to an earlier bug of the same name, according to Norwegian security firm Promon, which discovered both vulnerabilities six months apart. Strandhogg 2.0 works by tricking a victim into thinking they're entering their passwords on a legitimate app while instead interacting with a malicious overlay. Strandhogg 2.0 can also hijack other app permissions to siphon off sensitive user data, like contacts, photos, and track a victim's real-time location.
The bug is said to be more dangerous than its predecessor because it's nearly undetectable," Tom Lysemose Hansen, founder and chief technology officer at Promon, told TechCrunch.
The good news is that Promon said it has no evidence that hackers have used the bug in active hacking campaigns. The caveat is that there are no good ways" to detect an attack. Fearing the bug could still be abused by hackers, Promon delayed releasing details of the bug until Google could fix the critical"-rated vulnerability.
A spokesperson for Google told TechCrunch that the company also saw no evidence of active exploitation. We appreciate the work of the researchers, and have released a fix for the issue they identified." The spokesperson said Google Play Protect, an app screening service built-in to Android devices, blocks apps that exploit the Strandhogg 2.0 vulnerability.

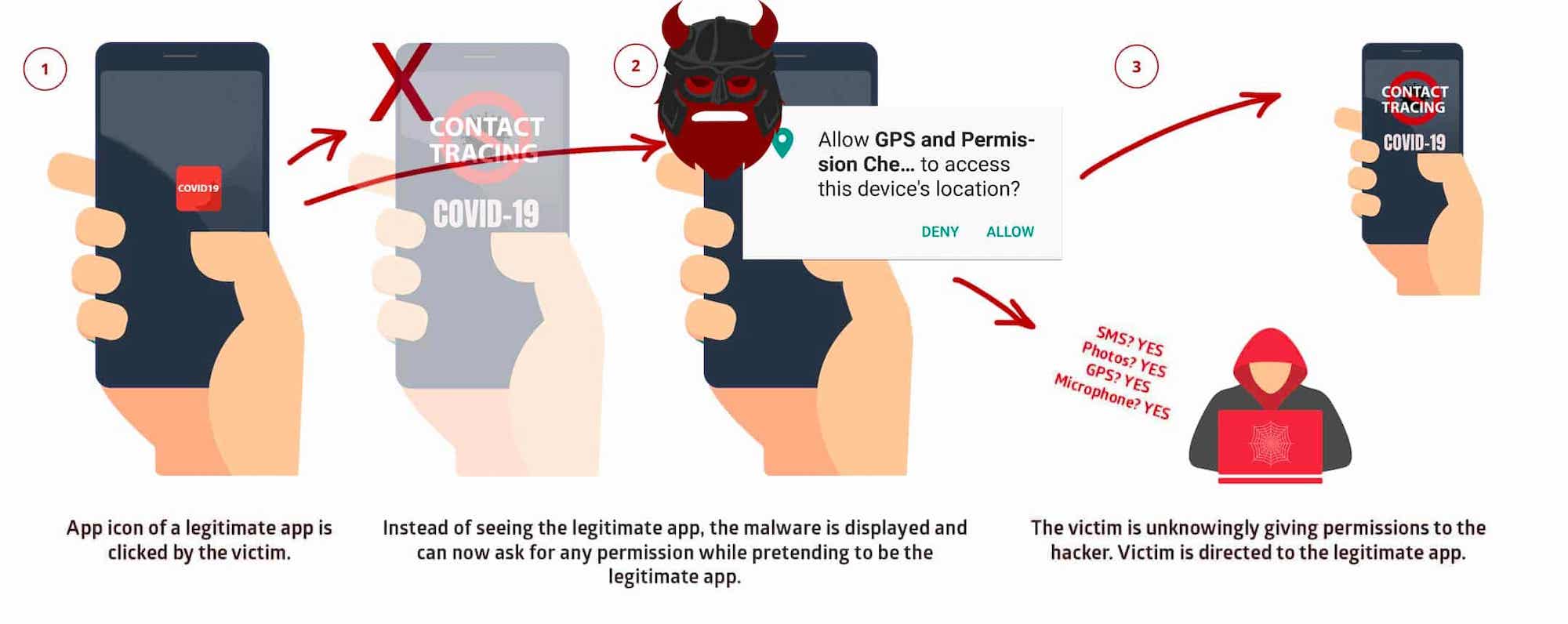
Standhogg 2.0 works by abusing Android's multitasking system, which keeps tabs on every recently opened app so that the user can quickly switch back and forth. A victim would have to download a malicious app - disguised as a normal app - that can exploit the Strandhogg 2.0 vulnerability. Once installed and when a victim opens a legitimate app, the malicious app quickly hijacks the app and injects malicious content in its place, such as a fake login window.
When a victim enters their password on the fake overlay, their passwords are siphoned off to the hacker's servers. The real app then appears as though the login was real.
Strandhogg 2.0 doesn't need any Android permissions to run, but it can also hijack the permissions of other apps that have access to a victim's contacts, photos, and messages by triggering a permissions request.
If the permission is granted, then the malware now has this dangerous permission," said Hansen.
Once that permission is granted, the malicious app can upload data from a user's phone. The malware can upload entire text message conversations, said Hansen, allowing the hackers to defeat two-factor authentication protections.
The risk to users is likely low, but not zero. Promon said updating Android devices with the latest security updates - out now - will fix the vulnerability. Users are advised to update their Android devices as soon as possible.
Millions downloaded dozens of Android apps from Google Play that were infected with adware