Colonial Pipeline Ransomware Attack Rattles Power Industry, Renews Vulnerability Concerns
The post Colonial Pipeline Ransomware Attack Rattles Power Industry, Renews Vulnerability Concerns appeared first on POWER Magazine.

A ransomware incident on May 7 that prompted Colonial Pipeline Co., owner of the nation's largest refined products pipeline, to proactively shut it down underscores the punch cyberthreats can pose to organizations, regardless of size or sector," the U.S. Cybersecurity and Infrastructure Security Agency (CISA) has warned.
Five days after Colonial Pipeline first learned it was the victim of a cyberattack, the Alpharetta, Georgia-headquartered company continued to restore operations on the 5,500-mile pipeline, which transports more about 45% of all fuel consumed on the East Coast from refineries primarily in the Gulf Coast. The White House on Monday said the Biden administration was continually assessing the impact of the ongoing incident" and evaluating every action" it could take to mitigate the impact as much as possible.
But fallout from the incident continued along with mounting concerns about commodities transported by the pipeline from the Gulf Coast and Northeast, including of various grades of gasoline, diesel fuel, home heating oil, jet fuel, and fuels for the U.S. military.
The attack is one of more than 4,000 ransomware attacks that have occurred daily since January 2016, according to CISA, but its high-stakes repercussions have alarmed a range of energy industry stakeholders.
While it does not seem to have directly affected the electricity sector, the incident has put members of the North American Reliability Corp.'s (NERC's) Electricity Information Sharing and Analysis Center (E-ISAC) on critical guard. As Manny Cancel, NERC senior vice president and E-ISAC's CEO, told POWER in a statement on Monday, the organization isolated from the federally designated electric reliability organization (ERO) to essentially provide bulk power system (BPS) stakeholders with resources to prepare for and reduce cyber and physical security threats has so far shared a cyber bulletin informing them of the breach and advising diligence in their own systems."
This incident is a clear example of the increasing amount of cyber activity impacting our nation's critical infrastructure," said Cancel. NERC and the E-ISAC remain dedicated to working with our public-private sector partners, including the Department of Energy and the Electricity Subsector Coordinating Council, to maintain awareness of key security matters and look for lessons learned applicable to our industry."
The Federal Energy Regulatory Commission (FERC), meanwhile, also urged renewed action to secure and safeguard the nation's energy infrastructure. While FERC and NERC have established and enforced cybersecurity standards for the BPS, there are no comparable mandatory standards for the nearly 3 million miles of natural gas, oil, and hazardous liquid pipelines that traverse the United States," noted FERC Chairman Richard Glick and Commissioner Allison Clements on Monday.
It is time to establish mandatory pipeline cybersecurity standards similar to those applicable to the electricity sector," their statement read. Simply encouraging pipelines to voluntarily adopt best practices is an inadequate response to the ever-increasing number and sophistication of malevolent cyber actors. Mandatory pipeline security standards are necessary to protect the infrastructure on which we all depend."
FBI Confirms DarkSide Is Responsible; DarkSide Claims Apolitical MotivesOn Monday, the Federal Bureau of Investigations (FBI) issued a brief statement confirming industry speculation throughout the weekend that DarkSide, a ransomware group, was responsible for the pipeline compromise.
According to cyber-defense firm Cybereason, DarkSide groups, first observed in August 2020, operate on a ransomware-as-a-service" model. Like many other ransomware variants, DarkSide follows the double extortion trend, which means the threat actors not only encrypt the user's data, but first exfiltrate the data and threaten to make it public if the ransom demand [ranging from $200,000 to $2 million] is not paid," the firm said in April. This technique effectively renders the strategy of backing up data as a precaution against a ransomware attack moot."
DarkSide, which is very active on hack forums and keeps its customers updated with news related to the ransomware," has grown increasingly sophisticated. Recently, for example, it announced the release of DarkSide 2.0, a new version of the ransomware strain that is equipped with the fastest encryption speed on the market," Cybereason wrote. More significantly, perhaps, in an effort to grow and expand their operations, the group has started an affiliates program for potential users," it said.
Cybereason suggests the group targets English-speaking countries, while appearing to avoid targets in countries associated with former Soviet Bloc nations." Paired with its sophisticated tactics, speculation over the weekend pointed to a state-sponsored motive for the attack.
But on Monday, DarkSide reportedly posted a notice (tweeted by cybercriminal intelligence platform DarkTracer) claiming it is apolitical"-and that its motive is purely financial. The notice reads: We do not participate in geopolitics, do not need to tie us with a defined government and look for other our motives." The notice emphasized: Our goal is to make money, and not creating problems for society." To that end, the notice suggests, the group will introduce moderation and check each company that our partners want to encrypt to avoid social consequences in the future."
Guarding Against RansomwareDarkSide ransomware gang, which shut down the largest oil pipeline in the U.S., posted a notice that their only goal was money. pic.twitter.com/uZUkWz6rpi- DarkTracer : DarkWeb Criminal Intelligence (@darktracer_int) May 10, 2021
However, CISA-which styles itself as the nation's risk advisor"-warns DarkSide isn't the only ransomware threat actor. Other sophisticated actors include TrickBot, a 2016-identified Trojan and suspected creator of BazarLoader malware; Ryuk, which has been deployed as a payload from banking Trojans; and Conti, which emerged in May 2020, and also deploys a double extortion" model.
Recognizing the insidious and widespread complexity of ransomware attacks by these varied actors, the agency in January launched a campaign aimed at reducing ransomware risks. A key concern, it noted, is that ransomware attacks are having increasingly prevalent" impacts on critical infrastructure, it said.
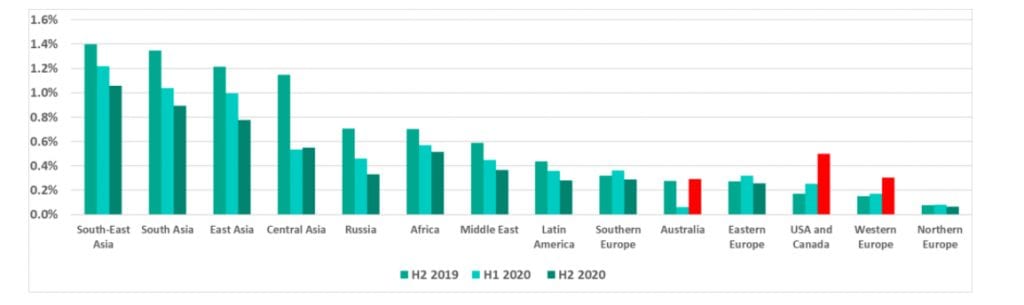 Percentage of industrial control systems computers on which ransomware was blocked by the distributed antivirus network,Kaspersky Security Networkover 2019 and 2020. Courtesy: Kaspersky ICS-CERT/Threat landscape for industrial automation systems. Statistics for H2 2020 (March 2021)
Percentage of industrial control systems computers on which ransomware was blocked by the distributed antivirus network,Kaspersky Security Networkover 2019 and 2020. Courtesy: Kaspersky ICS-CERT/Threat landscape for industrial automation systems. Statistics for H2 2020 (March 2021)In 2020 alone, nine attacks shut down physical operations at industrial sites through targeted ransomware, as Andrew Ginter, vice president of Industrial Security at Waterfall Security Solutions, highlighted in an April report. Eight of the nine attacks causing physical shutdowns in 2020 impacted multiple plants simultaneously," he noted. These include the January 2020 attack on Picanol Group, a large manufacturer of high-tech weaving machines, which lost 196 plant days, and U.S.-based office furniture giant Steelcase, which suffered a two-week shutdown owing to a Ryuk ransomware attack.
While CISA describes several tactics these actors use to infect victims with ransomware, it suggests the most common means are through:
- Email phishing campaigns. These include generic, broad-based spamming strategies," as well as precursor malware, which enables a hacker to use a victim's email account to spread the infection further.
- Remote desktop protocol (RDP) vulnerabilities. Criminals have used both brute-force methods" (using trial-and-error to obtain user credentials) and dark web credential purchases to gain access to RDP, a proprietary network protocol that allows individuals to control the resources and data of a computer over the internet.
- Software vulnerabilities. Criminals may exploit security weaknesses in widely used software programs to control victim systems and deploy ransomware.
Ginter, notably, also warned organized ransomware criminals could very likely" try and emulate the staggering scope of recent cyberattacks, including the SolarWinds Orion/Sunburst supply chain incidents. His firm Waterfall postulates-as a proactive defense measure-a nightmare attack that combines ransomware, supply chain, and cloud connectivity to exploit poorly defended Industrial Internet of Things (IIoT) cloud vendors.
The attacker chooses a vendor whose cloud-connected industrial controllers are essential to continuous operation of a given class of industrial process," such as steam, hydropower, and gas turbine management systems in power plants, the firm hypothesized in April.
The threat actor embeds malicious software in a firmware security update. The malware disables all further firmware updates and disables the industrial controllers. The attacker also takes control of the IIoT vendor's software update system. Instead of installing the firmware update under the control of the industrial site, the modified update system ignores software update settings and pushes the update immediately to all devices connected to the compromised cloud site. Thousands of IIoT devices and systems are now disabled and no longer respond to firmware update attempts. Hundreds of production sites are shut down," it says. Again, this overwhelms incident response teams, leading to a significant number of ransomware payments to the criminal organization."
Garret Grajek, CEO of cyber regulatory compliance specialist firm YouAttest, on Monday told POWER DarkSide's model-to create the malware and others are financially motivated via an embedded affiliate' code to other hacking groups for a successful delivery of the malware"-is especially troubling. This means that there's not just one threat vector to close off, but dozens if not more attack entries to block," he said.
Darkside has often created malware targeted domain controllers-so traditional hardening approaches are crucial, including patching and a fanatical lockdown of admin and service accounts. We must not only be performing regular access reviews of our key admin accounts, but also have instantaneous alerts on any attempts at privilege escalation on these accounts," Grajek added.
However, International Association of IT Asset Managers (IAITAM) President and CEO Dr. Barbara Rembiesa suggested the issue will require a much wider scope of coordinated vigilance. She urged more rigorous asset management. The problem here comes down to one central reality: If you are not managing your assets, you're not managing your business ... and you can't secure what you don't know you have," she said.
This country is way behind where it needs to be in ensuring that every single device and piece of software associated with these [old and new] infrastructure projects is accounted for, secure, and up to date. Old infrastructure is already under attack today because of a lack of rigorous IT Asset Management, and the prospect of the federal government adding billions of dollars to infrastructure without proper management will only add to the problem and open up more security loopholes," Rembiesa warned.
Some experts, like Tobias Whitney, vice president of Energy Security Solutions at Fortress Information Security, also called for more details about the incident. Ransomware is no longer a nuisance. It is a threat to our nation's critical infrastructure. It is time that industry understands the details of yesterday's attack," he told POWER. Among questions that would help industry understand the scope of the attack are: How did the hackers get access? How much and what data did they infiltrate?" he said. Now, is the time for information sharing-real information across the industry that not only shares post-mortem information after an attack but enables proactive measures to prevent an attack before it happens again."
If there is a silver lining, it is that we are taking some positive steps in our approach to calamities like this one," Whitney added. While the Biden administration's 100-day bulk power cybersecurity plan announced on April 20 is pretty balanced," he said, we need to be sure cybersecurity is a part of the critical infrastructure bill going forward. Government funding is critical to support and develop private sector solutions grounded in information sharing and focused on shoring up defenses for the utility, power, oil and gas industries," he said.
E-ISAC's Cancel told POWER the power sector's first line of defense, for now, is rooted in its distinctive efforts to coordinate awareness and information sharing. That includes lessons learned from other industries.
Information sharing is critical for an effective cyber defense, which requires substantial partnership and collaboration between industry and its government partners. The E-ISAC plays a significant role in this process by providing a central clearinghouse for information and sharing mitigation strategies to industry," he noted. Compared to other critical infrastructure industries, the power sector also has a long history of cooperation and mutual assistance," he said.
-Sonal Patelis a POWER senior associate editor (@sonalcpatel,@POWERmagazine).
The post Colonial Pipeline Ransomware Attack Rattles Power Industry, Renews Vulnerability Concerns appeared first on POWER Magazine.