Security of Cyber-Physical Systems

Cyber-physical systems" are the next generation of closely integrated physical and cyber systems. Several critical systems such as the power grid, autonomous transportation systems, and process control systems are examples of cyber-physical systems. They are liable to be attacked by malicious agents who can compromise the sensor measurements being used to control them. Indeed, there have been several reported attacks. It is, therefore, important to detect when a cyber-physical system is under attack.
The dynamic watermarking" method offers a new approach to this task. A secret signal is injected onto a control input, and the reported sensor measurements are analyzed to detect an attack. Dynamic watermarking has been tested on several systems of interest, including attacks on automatic generation control (AGC) and power electronics interfaces of grid-tied distributed energy resources.
Danger of Attacks on Open, Integrated SystemsWith the convergence of communication, computing, and control, we are entering the age of cyber-physical systems in which these technologies are tightly integrated." Examples include autonomous vehicles, the power grid, and process control plants.
These systems contain at their heart a physical system with inputs and outputs. The control inputs to the physical system are provided by actuators, and some of its outputs are measured by sensors. The output measurements are used to choose the control inputs in a closed-loop fashion. The loop between the sensors and the actuators may be closed over a communication/computation network, as depicted on the left panel in Figure 1.
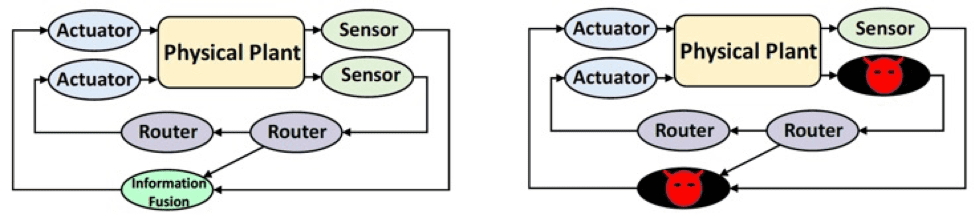 1. A cyber-physical system is shown on the left, while a cyber-physical system with compromised sensor measurements is shown on the right. Courtesy: P.R. Kumar
1. A cyber-physical system is shown on the left, while a cyber-physical system with compromised sensor measurements is shown on the right. Courtesy: P.R. KumarWith the advent of networking, many previously closed systems are becoming open to malicious agents. Many reported cyberattacks on cyber-physical systems have been reported; a well-known example is the Stuxnet worm of 2010 that attacked computers controlling centrifuges in a uranium enrichment facility. In networked cyber-physical systems, sensors can be compromised, or false sensor measurements can be provided over the communication network, as shown on the right panel in Figure 1. The compromised sensor measurements can cause the control system to take wrong actions that can damage the physical system.
An example of concern with respect to the power grid is AGC, where generators in individual areas respond to frequency measurements by increasing or decreasing their generation. A malicious agent reporting a false frequency measurement from a phasor measurement unit could cause generation to be decreased rather than increased. In a chemical process control system governing an oil refinery, a malicious agent could cause a pressure sensor to report a false measurement of the level of a tank to a flow-control loop, causing a dangerous overflow from the tank. Because economic or physical harm can result from their malfunction in safety- or economy-critical applications, it is important to protect cyber-physical systems from such attacks.
Detecting Stealthy Attacks on Cyber-Physical SystemsTo protect a cyber-physical system that is under attack-by various strategies such as switching a control system from automatic to manual control, rebooting a system, or shutting it down (if that is permissible, depending on the particular context)-it is first necessary to know when the system is under attack.
The dynamic watermarking-based attack detector is a general-purpose methodology to detect attacks on cyber-physical systems. This approach consists of adding a secret random signal to an actuator input, as shown in Figure 2. The dynamic watermark percolates through the system, gets transformed appropriately by the dynamics of the system, and is an indelible portion of the sensor outputs. By comparing the reported sensor measurements with the watermark, an attack detector can be designed to detect whether the sensor measurements have been corrupted. There are theoretical guarantees that can be provided on the ability of the attack detector to detect any stealthy attacks.
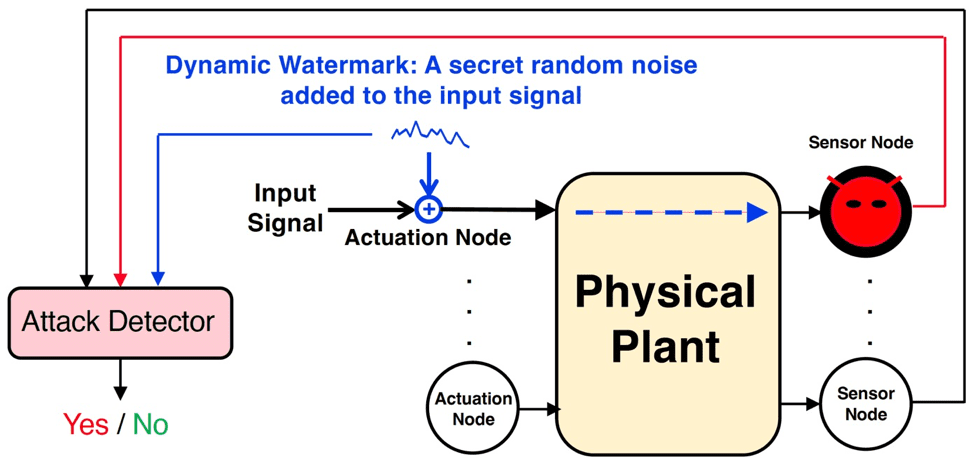 2. Dynamic watermarking to detect attacks on sensor measurements. Courtesy: P.R. KumarApplications of the Watermark-Based Attack Detector
2. Dynamic watermarking to detect attacks on sensor measurements. Courtesy: P.R. KumarApplications of the Watermark-Based Attack DetectorThe dynamic watermark-based detector has been tested on various applications through simulations, in laboratory models of systems, and in field prototypes. For example, it has been tested via simulation for its capability to detect attacks on AGC.
As shown in Figure 3, AGC employs measurements of frequencies and power flows to adjust generations in areas. These measurements can potentially be corrupted, causing instability or bad performance of the system. Dynamic watermarking injects a small, secret noise" into the generation commands, but is so small that it does not otherwise disrupt the normal performance of the system.
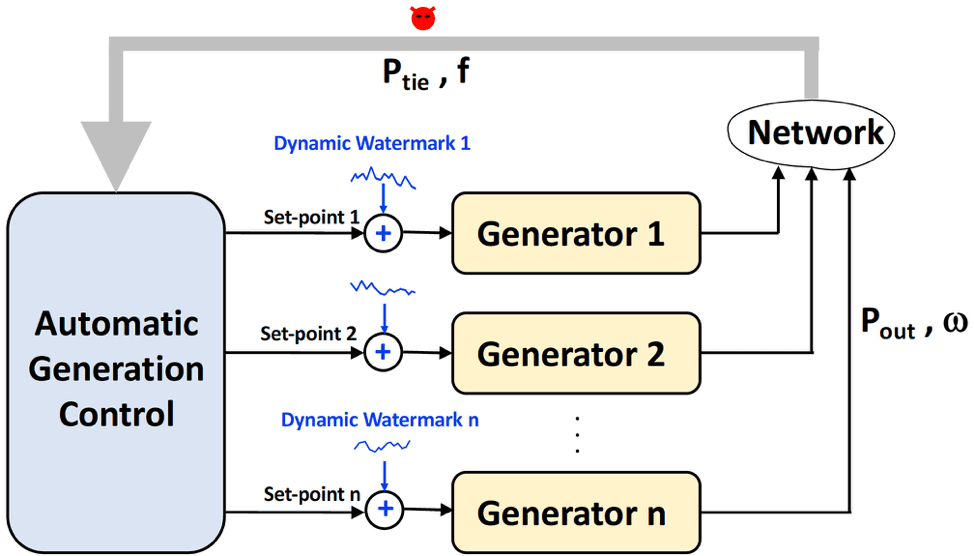 3. Dynamic watermarking to detect attacks on sensor measurements. Courtesy: P.R. Kumar
3. Dynamic watermarking to detect attacks on sensor measurements. Courtesy: P.R. KumarA simulation study was performed on a four-area synthetic system with AGC in each area. Whereas, a destabilizing attack that begins at 10 minutes would normally have been detected by an operator only at time 18 minutes, the dynamic watermarking allows it to be detected almost instantaneously at 11 minutes, thereby potentially preventing damage, as shown in Figure 4.
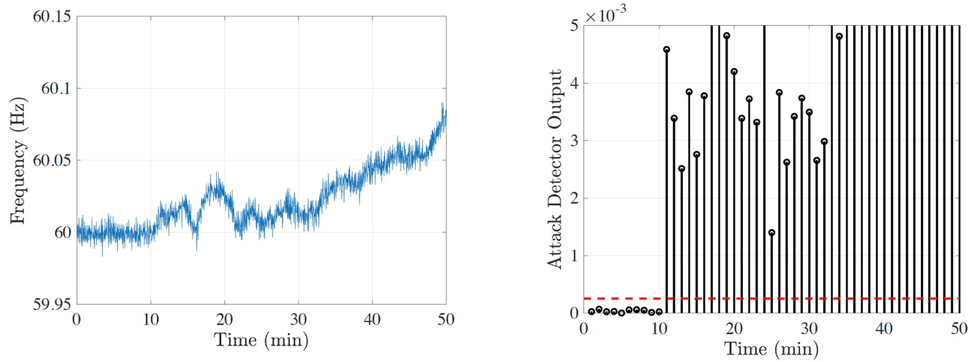 4. The attack on AGC begins at 10 minutes. The dynamic watermarking-based attack detector's signal, shown on the right, raises a flag at time 11 minutes, signifying that an attack has been detected. Courtesy: P.R. Kumar
4. The attack on AGC begins at 10 minutes. The dynamic watermarking-based attack detector's signal, shown on the right, raises a flag at time 11 minutes, signifying that an attack has been detected. Courtesy: P.R. KumarAnother attack scenario of potential concern arises from the increasing penetration of distributed energy resources (DERs). In grid-connected photovoltaic (PV) installations, smart power electronics inverters interface between the DERs and the grid. A cybershield" for a grid-following inverter is shown in Figure 5.
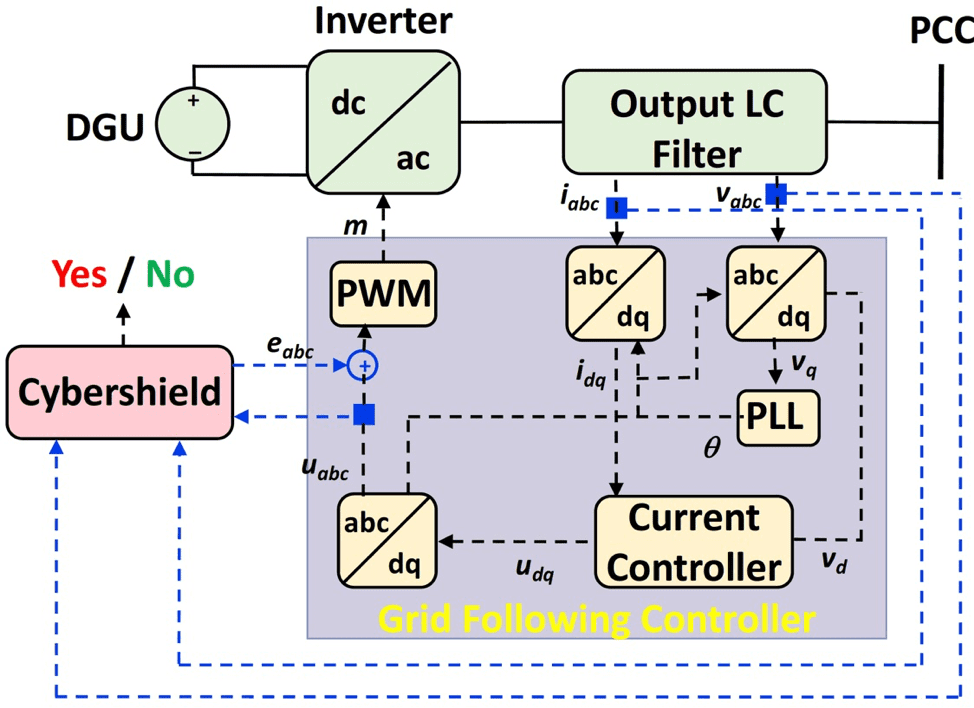 5. A dynamic watermarking-based cybershield for a grid-following inverter. Courtesy: P.R. Kumar
5. A dynamic watermarking-based cybershield for a grid-following inverter. Courtesy: P.R. KumarVarious measurements could potentially be compromised in grid-following/forming mode, including:
- The three-phase instantaneous terminal voltage and current measurements.
- In secondary control, the bus voltage magnitudes and frequencies at buses in a microgrid.
- In tertiary control, the real and reactive power exchange between a microgrid and the distribution system.
Several simulation studies and an experimental validation have been conducted. In addition to the power system applications already described, the dynamic watermarking method also has been tested on an intelligent autonomous vehicular system, a process control system, and a helicopter system. The first application of dynamic watermarking-based attack detector was on a laboratory model of an intelligent autonomous vehicular system, and subsequently in proving ground tests on an instrumented autonomous Lincoln MKZ. It has been tested on a laboratory-scale model of a process control system, a two-tank system, and a laboratory model of a two-rotor aerial vehicle flight control system, that is, a helicopter.
A Widely Tested Approach to Quickly Detecting AttacksCyber-physical systems are the next generation of systems where the cyber and physical worlds are tightly integrated. Examples include several infrastructure systems, such as the power grid, as well as several intelligent systems, such as autonomous vehicular systems. They can be subject to attacks by malicious agents who can compromise the sensor measurements on which the control loops in the system rely. Such attacks can cause economic damage or physical harm, since the systems can be economically, socially, and safety critical. It is, therefore, important to quickly detect when such systems are under attack.
The dynamic watermarking method adds a small secret signal to the control inputs at the actuators. The measurements reported by the sensors, or the communication network, can be examined to see whether the reported measurements contain the appropriately transformed versions of the secret signal to yield an attack detector. This method has been tested in simulations, laboratory experiments, and on prototypes in the field. For power systems, it has been tested by simulation for its ability to detect attacks on automatic generation control and in laboratory prototype for attacks on the power electronic interface between DERs and the grid with which they are tied.
-P.R. Kumar (prk@tamu.edu) is a professor in the Department of Electrical and Computer Engineering at Texas A&M University in College Station, Texas. He received the 2022 IEEE Alexander Graham Bell Medal for seminal contributions to the modeling, analysis, and design of wireless networks" at the 2022 IEEE Vision, Innovation, and Challenges Summit (IEEE VIC Summit) and Honors Ceremony on May 6 in San Diego, California.
The material in this article is based upon work partially supported by the U.S. Department of Energy's (DOE's) Office of Energy Efficiency and Renewable Energy (EERE) under the Solar Energy Technologies Office Award Number DE-EE0009031; U.S. Department of Homeland Security (DHS) under 70RSAT20CB0000017; U.S. National Science Foundation (NSF) under IIS-1636772; U.S. Office of Naval Research (ONR) under N00014-21-1-2385; and U.S. Army Research Office (ARO) under W911NF1810331 and W911NF2120064. The views expressed herein, and conclusions contained in this document, are those of the author and should not be interpreted as representing the views or official policies, either expressed or implied, of the DOE, DHS, NSF, ONR, ARO, or the U.S. Government. The U.S. Government is authorized to reproduce and distribute reprints for Government purposes notwithstanding any copyright notation herein.
The post Security of Cyber-Physical Systems appeared first on POWER Magazine.