Identity protection is key to metaverse innovation
If today's metaverse were a shopping mall, you could visit any number of department stores, each with its own rich selection of products and experiences. You could pop into virtual platforms like Roblox to buy a new outfit for your avatar or stop by Decentraland to gauge the latest valuation of digital real estate. You couldn't, however, take your Roblox avatar into Decentraland or to a VR movie on another brand's platform. The hallways, elevators, kiosks, and reference maps-the infrastructure that makes it possible to carry your shopping bags from store to store-are still being built.

Another unfinished element of the metaverse is its security: the guards, the CCTV cameras, the shoplifting alarms. Common cybersecurity protocols-the technologies equivalent to the https" of today's internet-are still a work in progress in the metaverse. So too are the governance standards that will protect your privacy, property-and perhaps most importantly-identity.
Even in today's 2D version of the internet, digital identity is a complicated affair. Phishing has become so sophisticated that an email from your bank, a call from your auto insurer, or even a text message from your mother may not be what it seems. The immersive nature of the metaverse, however, may set the stage for even more elaborate forms of identity theft or mimicry.
The threat of social engineering will potentially be even more effective in a 3D world, where deepfakes will be prevalent and an imposter is even more capable of tricking victims," says Jeff Schilling, global chief information security officer at the digital business services firm Teleperformance. He emphasizes the importance of digital identity: No matter the medium- telephone or metaverse-the best way to resist social engineering is by having a foolproof way to validate who is on the other end of the conversation."
Identity protection will be a critical part of successful business operations in the metaverse-and it's an especially important consideration for those getting in on the ground floor.
Metaverse innovators can lead on cybersecurityAlthough the metaverse is currently a patchwork of individual companies' siloed experiences, that won't be the case for long. Major technology players are already hard at work constructing the aforementioned infra- structure. So are organizations like the Open Metaverse Interoperability (OMI) Group, an open-source community of tech industry veterans working to help companies achieve meta-traversal" capabilities-that ability to move seamlessly from Saks to Starbucks. Before long, these innovators will want to integrate those environ- ments to create a seamless experience for their shared customers.

David Truog, vice president and principal analyst at Forrester, points out that the metaverse will be the next iteration of the internet-and like the early web, it will go through some growing pains. In the web's infancy, he notes, it had no encryption or e-commerce. Nobody used site passwords or had an online bank account. Very rapidly, there was a need for systems and social contracts and infrastructure that mirrored some of what we expect in the physical world," he says. These systems were necessary so that people could engage in private communications, buy things, trust that they could submit a credit card number online, and so on."
In the metaverse, the role of cybersecurity in establishing similar interactions will be an order of magnitude or two" more important, says Truog. As such, first movers in the space are in a unique position to anticipate security gaps and build in safeguards from the get-go.
In this early era of the metaverse, there's an opportunity for companies to learn from past technological evolutions and resulting security snafus. The advent of AI algorithms, for instance, showcased the gravity of guarding against bias. Migration to the cloud highlighted the importance of encryption. When the business community was first transitioning from the typical data center environment to the public cloud, everybody went there with great excitement-but they forgot to bring their security with them," says Schilling. I see a similar scenario building with the metaverse."
One way to ensure a safer experience this time around is to give the right people a seat at the table early on. A chief information security officer (CISO) or chief technology officer (CTO), for instance, who has in-depth knowledge of the cloud technology likely to underpin much of the metaverse, is a valuable investment for these startup companies.
Many startup companies with great ideas start with five people sitting around the table. I think today one of those five people should be a security person," says Schilling.
Identity protection counters new threatsIn addition to more sophisticated social engineering schemes, other security threats could become more menacing in the metaverse. New kinds of ransomware, for instance, could lead to large-scale cryptojacking," taking over systems for use in cryptocurrency mining. Consumer-facing malware and Trojan horses could become more insidious, with malicious code taking the form, for example, of free swag for an avatar.
Some people are saying that the metaverse is just a three-dimensional representation of the IT environment we have today-but that's not necessarily true," explains Schilling. There are some operational differences, and there are a lot of gaps and seams when it comes to threat scenarios."
Identity and authentication present an especially thorny arena. How will a celebrity-or CEO-protect his or her avatar from copycats or copyright infringement? How will companies ensure their employees are who they say they are, both in internal and customer-facing contexts?
Avatars that look like the people they're claiming to represent may be able to slip more effectively past people's guard, because they tap into our natural human inclination to base our decisions about someone's identity on recognizing their face and mannerisms," says Truog.
As a result, identity protection-which encompasses passwords, biometric logins, multi-factor authentication (MFA), and end-to-end encryption, among other technologies-has ballooned into a billion-dollar industry. The identity protection global market size was around $12.3 billion in 2020, and it's projected to nearly double that by 2025, according to the Identity Management Institute.
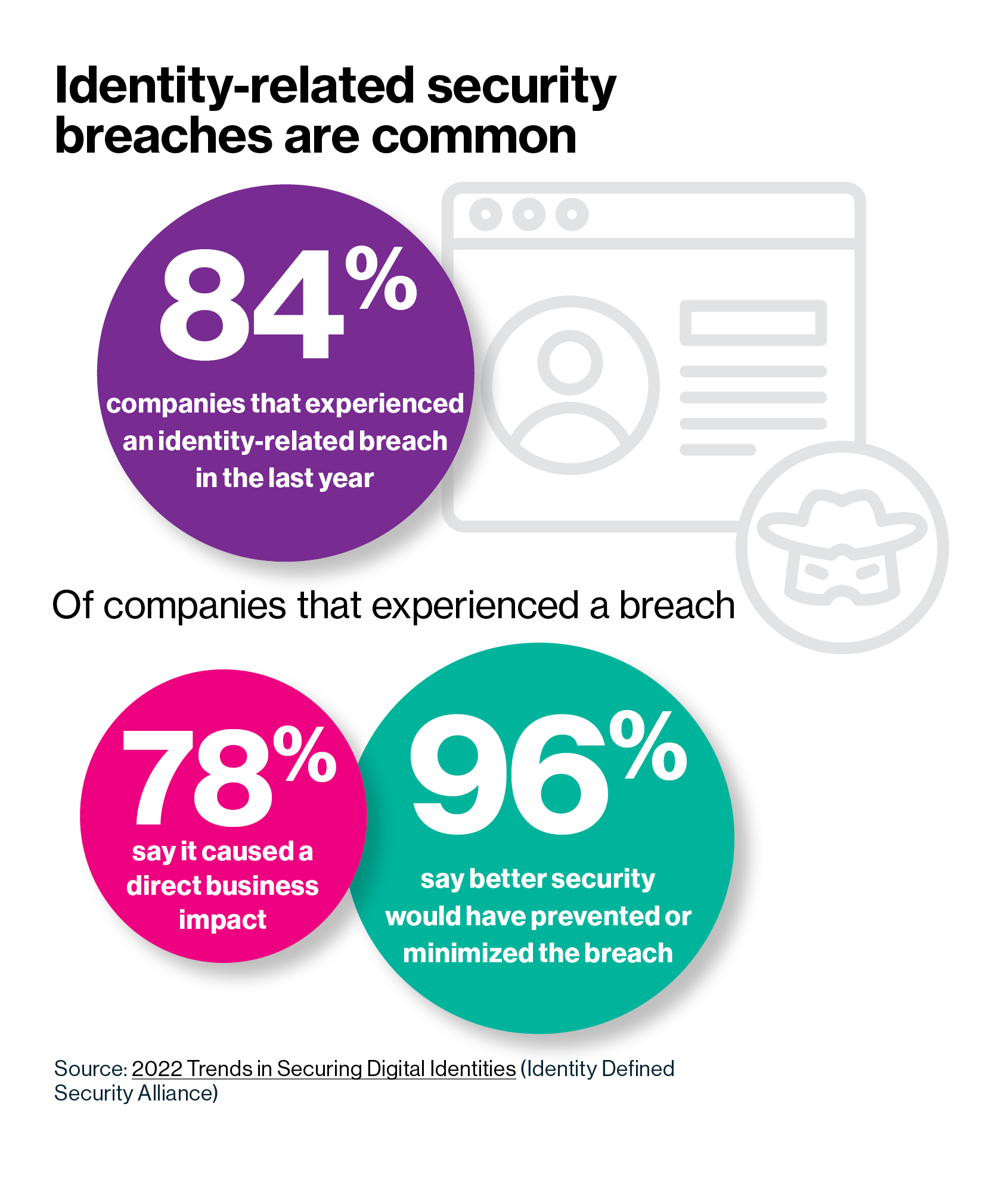
Robust identity protection can help resist unauthorized access to sensitive data, ransomware attacks, identity fraud, and theft. Still, keeping pace with hackers' latest scams is often a game of cat and mouse. A 2020 report by the Identity Defined Security Alliance (IDSA) found that 79% of respondent organizations had experienced an identity-related data breach in the preceding two years. Those metrics continue to worsen: in a 2022 follow-up, 84% of respondents reported an identity- related data breach in the last year.
That's not to say identity protection is futile. Of the 2020 IDSA survey respondents who experienced an identity- related breach, a full 99% believe these types of attacks are preventable. Data from the report also suggests that proactivity makes a difference-34% of companies with a forward-thinking" security culture reported an identity-related breach in the year preceding the survey, versus 54% of companies with a reactive" culture.
We've already seen glimpses of how a lack of identity protection could manifest in the metaverse. Social media companies have invested significant sums in removing fake users and bots over the last few years. At the start of the covid-19 pandemic, as teams adopted videoconferencing for remote work, many companies saw firsthand the necessity for security parameters around virtual meetings.
This content was produced by Insights, the custom content arm of MIT Technology Review. It was not written by MIT Technology Review's editorial staff.