A new age of disaster recovery planning for SMEs
Today's cyberthreat landscape has become increasingly complex. Gone are the days when devastation to enterprises' data and IT systems was caused solely by force majeure events and physical terrorist attacks. Rising geopolitical tensions, fast-tracked digital transformation, and remote and hybrid working styles driven by the pandemic have made both public and private organizations across the globe increasingly vulnerable to cyberattacks via ransomware, malware, or hacking.
Today's data is generated and distributed across highly complex ecosystems-multicloud, hybrid cloud, edge, and internet of things. Enterprises' surface exposure to risks has ballooned. It's not just big corporations that are at risk. Smaller, less sophisticated companies are easier targets due to their lack of resources and expertise.
According to Accenture, more than one-third of cyberattacks are aimed at small businesses, but only 14% of them are prepared to defend themselves.1 Cyberattacks could leave many small and midsize enterprises (SMEs) reeling from financial and productivity losses, operation disruptions, extortion payments, settlement costs, and regulatory fines.
Given this backdrop, experts say it's time to plan for when, not if. Clear backup and disaster recovery plans-focusing on IT infrastructure, data, and applications-to execute recovery processes after a disaster are vital in every enterprise's business continuity strategy. This report explores what disaster recovery planning entails and how SMEs can implement it in today's fast-evolving cyber landscape.
The following are the report's key findings:
- Cyberattacks have grown more frequent and sophisticated, and SMEs are in the firing line. The data tells a worrying story. With the pandemic, along with geopolitical factors, causing shifts in how we live and work, the case for disaster recovery planning has never been more urgent.
According to one cross-industry study, midsize companies were almost 500% more likely to be targeted by the end of 2021 than two years ago.2 Experts say artificial intelligence-based attacks are rising. Ransomware-as-a-service and, in some cases, deepfakes are also increasing, although most SMEs become victims because of human error.
- A well-built disaster recovery plan can significantly minimize and even eliminate downtime. Disaster recovery plans are a key component of business continuity plans. While business continuity focuses on overall strategy, including policies and procedures for recovery following an incident, disaster recovery focuses on IT infrastructure, data, and applications.
- A well-crafted disaster recovery plan includes clear definitions of recovery time objective (RTO) and recovery point objective (RPO).3,4 Having such a plan is crucial for protecting data and applications against malware and ransomware attacks and could significantly minimize or even eliminate downtime.

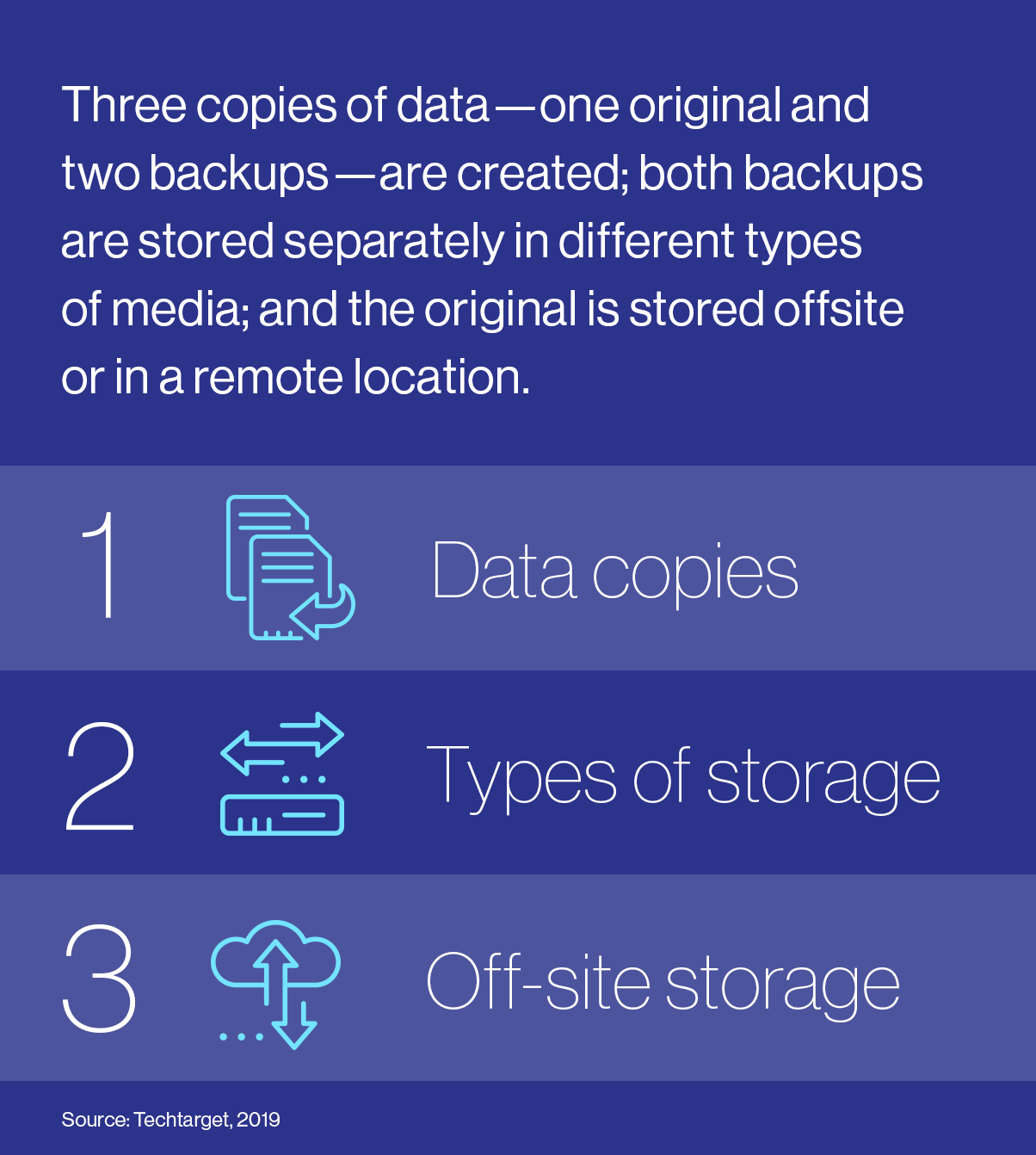
- Backups and replication of data are essential for disaster recovery. With cybercriminals spending over 200 days in companies' systems before being noticed5 and corrupting backups, SMEs need to store their data in multiple formats on different systems or look toward a data replication solution to ensure near-instantaneous recovery. While the longstanding 3-2-1 strategy6 is endorsed by cybersecurity experts, some organizations are seeking greater security with the 3-3-2 approach7, which includes an extra disconnected and inaccessible (air-gapped") copy.
- An unexamined disaster recovery plan could bring enterprises back to square one. Disaster recovery plans are essentially pointless without regular practice runs-and how often this practice should be done depends on how fast an organization is growing or adopting new technologies. Experts say such plans should be updated and tested at least annually, and ideally every quarter.
This content was produced by Insights, the custom content arm of MIT Technology Review. It was not written by MIT Technology Review's editorial staff.