The Flipper Zero: A Hacker’s Delight

Readers of this Hands On are likely to fall into one of two camps: those who'll view the Flipper Zero with fascination, and those who'll view it with loathing. Among the former are security researchers and hardware developers trying to debug a wireless setup. Among the latter are IT folks charged with defending their realm from physical or network attacks. But whatever camp you fall into, the Flipper is something you'll need to know about.
The Flipper is an open-source hacking tool of exceptional polish and functionality. Its official price is US $169, but it sells out as fast as it can be manufactured and so can often only be found at a hefty markup-I paid $250 from one reseller.
Hacking software and hardware tends to adopt, either consciously or unconsciously, design aesthetics that wouldn't be out of place in a William Gibson cyberpunk novel. Hardware is utilitarian, with boxy enclosures painted or printed black. Software often relies on opaque commands. They are serious tools for serious people. The Flipper stands this schema on its head. Its line of aesthetic descent is more Tamagotchi than tech dystopia, with a brightly colored white-and-orange case molded to fit your palm. An onscreen animated anthropomorphic dolphin pops up to guide you through setup menus. It looks and feels like a child's toy. It isn't.
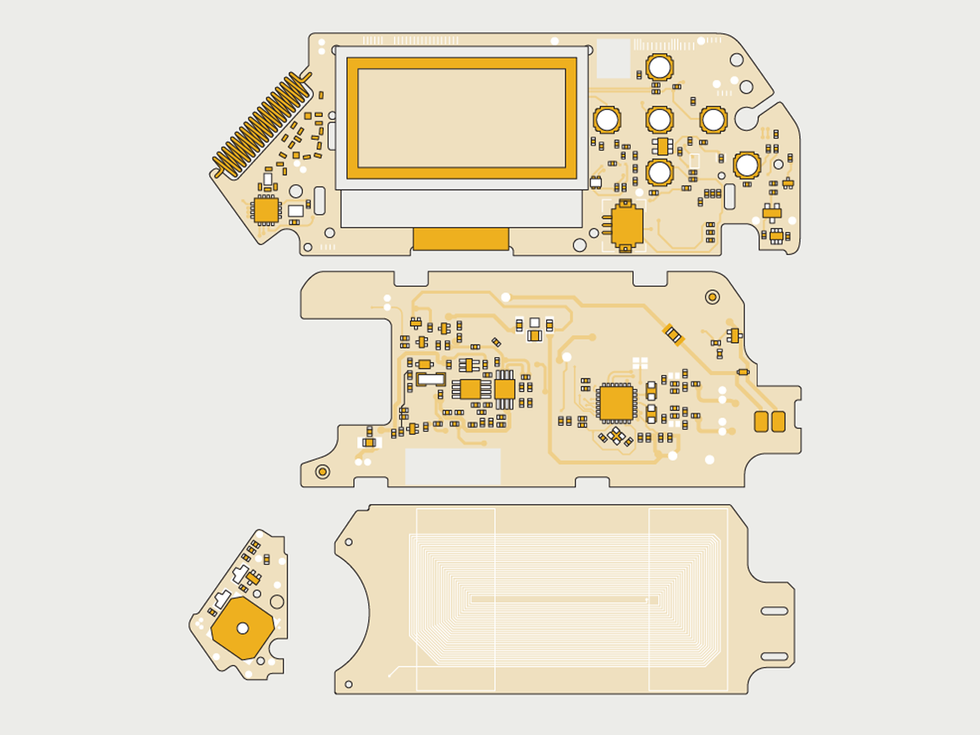 An open-source design, the Flipper is composed of a main board with an ARM-based CPU and transceiver chip, a board for NFC and RFID communications, a PCB antenna, and an extra board to handle IR and iButton interfacing.James Provost
An open-source design, the Flipper is composed of a main board with an ARM-based CPU and transceiver chip, a board for NFC and RFID communications, a PCB antenna, and an extra board to handle IR and iButton interfacing.James Provost
The Flipper is powered by a 32-bit Arm processor core with a top speed of 64 megahertz. That's hardly anything to get excited about, but the core is paired with a bunch of analog and serial peripheral interfaces and, most importantly, a sophisticated radio transceiver. Out of the box, the Flipper can do quite a few interesting things. For starters, it lets you read many common types of RFID key cards by holding them up to the Flipper, which stores the data on its SD card-and then you can use the Flipper to emulate those cards, opening, say, an office door as easily as if you had the original card. (It's flexible enough that I was even able to read the microchips implanted into my cats, which operate at a different frequency than RFID key cards.) This can be handy if, like me, you sometimes find yourself digging out a small sheaf of blank white cards from your wallet and trying each in turn to open a seldom-used door, but the implications for physical security are obvious. (It's true that you can also easily clone key cards at, for example, the kind of kiosk that also cuts keys, but you need to bring the card to the kiosk, something harder to do surreptitiously than simply cloning the card in situ.)
In a similar fashion, you can clone an iButton key fob, and many radio remotes that work in the popular 433-MHz band. It can also read near-field communication (NFC) devices, such as MIFARE key cards, and even pick up the signals your contactless credit card's EMV chip puts out (although this is of very limited use, since the Flipper can't duplicate the output of the algorithms used to create a per-transaction one-time code). There's even an infrared port that allows you to clone, say, a TV remote, a la a universal remote control, and if you don't have access to the original remote control, it can cycle through a set of common infrared protocols for basic commands like on/off and changing the channel, making it a superpowered version of the TV-B-Gone. This last capability is popular for petty mischief, judging by the numerous videos online showing people turning off lecture hall projectors, or fast-food-restaurant menu displays.
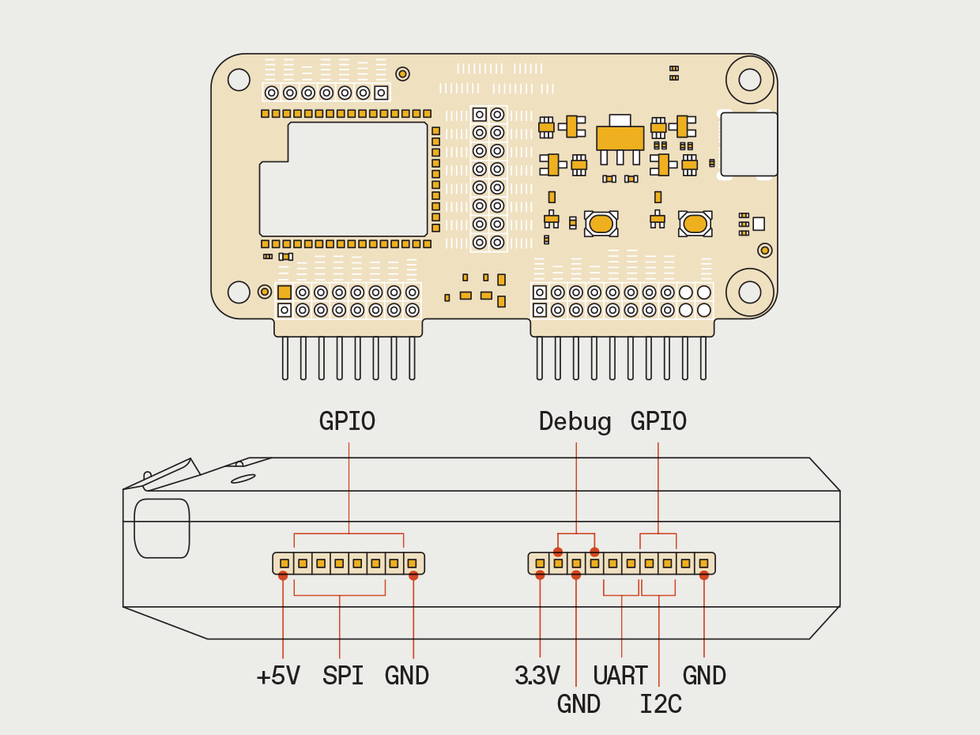 The Flipper's capabilities can be enhanced with add-on boards, such as a Wi-Fi board or other hardware that can communicate via a number of serial protocols. In addition, the Flipper can help debug hardware by generating various test signals, including PWM, which can be used to test a servo, for example.James Provost
The Flipper's capabilities can be enhanced with add-on boards, such as a Wi-Fi board or other hardware that can communicate via a number of serial protocols. In addition, the Flipper can help debug hardware by generating various test signals, including PWM, which can be used to test a servo, for example.James Provost
The Flipper also has the ability to emulate a USB keyboard and mouse, and can execute scripts that can control a graphical user interface-a boon for folks seeking to automate tasks, another security headache for others. You can also use the Flipper as a UART-to-USB bridge, allowing connectivity with many devices that don't support USB.
A $45 plug-in board adds Wi-Fi capabilities, although as shipped this merely enables over-the-air updates. But there are plenty of hacks of the Flipper and the Wi-Fi board themselves. It's possible to replace their firmware with alternatives that allow low-level control of Wi-Fi signals, albeit with a return to the land of cryptic commands. This opens up the ability to do a number of attacks on a Wi-Fi network. In one built-in example, you can spoof a series of access point names, so the list of Wi-Fi networks in your area is spammed, line by line, by the lyrics to Rick Astley's Never Going To Give You Up," in an unusual version of Rickrolling. (To test this without provoking the ire of either the IEEE's IT department or my neighbors, I took the Flipper to the end of a pier jutting 110 meters out from the aptly named Transmitter Park into New York City's East River). Another point-and-shoot attack lets you target an access point with a flood of deauthorization packets, killing active connections.
All this functionality is, in itself, legal. Just as with a set of lockpicks, the line is not the possession or even use of the tools, but how the tools are used. Attacking your own network or cloning your own key card is one thing, going after someone else's is another. But the modified firmware can also allow the Flipper to perform actions that are inherently illegal, such as removing regional restrictions on which ISM bands the device can transmit on: The moment you pump out a single photon on a band that's a no-no in your region, you are operating illegally.
Just like the smartphone, the Flipper is a demonstration of technological convergence, merging many different devices into one slick package. One wonders what the next-generation version will bring-and whether or not it'll look like a Furby.