 |
by Mark Frauenfelder on (#12NWX)
The Stratio LinkSquare is small spectrometer that connects to a smartphone. This video shows the reflected light spectrum of three pills - a "fraud" Viagra pill, a generic pill, and the real thing – compared to a genuine Viagra spectrum reference. Stratio will crowdfund the LinkSquare this year and it will sell for $200.From MIT Technology Review:Stratio says it eventually plans to branch out beyond pills to testing other items that can be mislabeled, like food (fish, for instance), and thinks it could be useful for consumers and companies, too.“We’re hoping people can use this to assuage some of their fears about the things they consume,†says Leslie Grothaus, a Stratio cofounder and its head of business development and communications.
|
| Link | http://feeds.boingboing.net/ |
| Feed | http://feeds.boingboing.net/boingboing/iBag |
| Updated | 2026-03-04 14:02 |
 |
by Rose Eveleth on (#12NKY)
Hello and welcome to newest addition to the Boing Boing podcast family! Flash Forward is a podcast produced and hosted by me, Rose Eveleth. Every week we really overthink what the future has in store for us. Every episode we tackle one possible (or, not so possible) future scenario — everything from a sudden ice age, to the end of antibiotic effectiveness, to a world in which contact sports are banned due to head injury — and try to work out how that future would really go down.Today, about two percent of the population has prosopagnosia — a condition that makes them unable to remember faces. But what if we all had it? On this week’s episode, we travel to a future where nobody can recognize one another by face.Flash Forward: RSS | iTunes | Twitter | Facebook | Web | PatreonIn the episode we discuss what causes face blindness and the tricks that people use to remember their friends. We also go through all the things that would be easier (spying, hiding) and harder (police lineups, cocktail parties) in a world where we were all faceblind. ▹▹ Full show notes
|
 |
by Rob Beschizza on (#12NHW)
It's like something out of Mad Max: a Russian biker gang-cum-militia wearing wolfy helmets, operating in the ruins of Eastern Ukraine. They are "fiercely loyal" to Vladimir Putin and to Christ, but not to families they left behind.
|
 |
by Xeni Jardin on (#12KB9)
Another brutal attack is reported to have taken place in Nigeria, led by the Islamic armed group Boko Haram. On Saturday night, Boko Haram militants carrying machine guns rolled into the village of Dalori on motorcycles, opening fire on every living thing in sight. (more…)
|
 |
by Xeni Jardin on (#12K8H)
As protests continue over the death of Mario Woods, who was shot and killed by an SFPD cop in December, the Justice Department announces it will conduct a “comprehensive review†of the San Francisco Police Department. (more…)
|
 |
by Xeni Jardin on (#12K4V)
With the release of its fourth-quarter earnings report today, Google parent company Alphabet became the world's most valuable company, and kicked Apple out of that coveted spot. (more…)
|
 |
by Cory Doctorow on (#12J50)
In Mumbai, cab drivers vie to make their vehicles stand out from their competitors', decorating them with exuberant expressions of the driver's personality. (more…)
|
 |
by David Pescovitz on (#12J1Y)
Amateur Radio Club visited the border of Area 51 and noticed some new "no drone" signage added to the classic warnings signs around the infamous US Air Force facility. I assume that policy also applies to extraterrestrial spacecraft and Alien Reproduction Vehicles. Yours anyway. (Foxtrot Alpha via Mysterious Universe)
|
 |
by Mark Frauenfelder on (#12HSF)
La Fabrique DIY built a cool Frisbee launcher using a bike wheel an electric drill.
|
 |
by Mark Frauenfelder on (#12HNW)
Since 2008, the Church of the SubGenius has been waiting for Time Warner to pay $30 for the unauthorized use of Bob Dobb's likeness. It should totally pay the fee, because it will become a SubGenius minister and can start calling itself Reverend Time Warner.
|
 |
by Rob Beschizza on (#12HJR)
Ed Piskor, creator of Hip Hop Family Tree (which debuted right here at Boing Boing) shared with us some of the ancient artistic tools that inspires his unique technique.While drawing a splendid Happy Mutant, he takes us through his "war chest": zip-a-tone sheets, letraset, a Leroy lettering gadget, risography, and the immortal spirit of great cartooning.He also muses on what it's like to teach students who know every corner of a Wacom tablet, but recoil in horror when the only undo level is a splodge of white-out.Enjoy the 35-minute visit to his studio! And keep an eye out for the Happy Mutant you see below—we'll be auctioning them for a good cause soon.
|
 |
by Mark Frauenfelder on (#12HJ8)
According to Wikipedia, "Cybernetic Serendipity was an exhibition of cybernetic art curated by Jasia Reichardt, shown at the Institute of Contemporary Arts, London in 1968." This film shows some of the art that was on display. It looks fantastic.In 2014, ICA produced a short film about the exhibition, with commentary by Reichardt.https://youtu.be/oSwovB28B34One part of the exhibition was concerned with algorithms and devices for generating music. Some exhibits were pamphlets describing the algorithms, whilst others showed musical notation produced by computers. Devices made musical effects and played tapes of sounds made by computers. Peter Zinovieff lent part of his studio equipment - visitors could sing or whistle a tune into a microphone and his equipment would improvise a piece of music based on the tune.Another part described computer projects such as Gustav Metzger's self-destructive Five screens with computer, a design for a new hospital, a computer programmed structure, and dance choreography.The machines and installations were a very noticeable part of the exhibition. Gordon Pask produced a collection of large mobiles with interacting parts that let the viewers join in the conversation. Many machines formed kinetic environments or displayed moving images. Bruce Lacey contributed his radio-controlled robots and a light-sensitive owl. Nam June Paik was represented by Robot K-456 and televisions with distorted images. Jean Tinguely provided two of his painting machines. Edward Ihnatowicz's biomorphic hydraulic ear turned toward sounds and John Billingsley's Albert 1967 turned to face light. Wen-Ying Tsai presented his interactive cybernetic sculptures of vibrating stainless-steel rods, stroboscopic light, and audio feedback control. Several artists exhibited machines that drew patterns that the visitor could take away, or involved visitors in games. Cartoonist Rowland Emett designed the mechanical computer Forget-me-not, which was commissioned by Honeywell.Another section explored the computer's ability to produce text - both essays and poetry. Different programs produced Haiku, children's stories, and essays.Computer generated movies were represented by John Whitney's permutations and a Bell Labs movie on their technology for producing movies. Some samples included images of teseracts rotating in four dimensions, a satellite orbiting the earth, and an animated data structure.Computer graphics were also represented, including pictures produced on cathode ray oscilloscopes and digital plotters. There was a variety of posters and graphics demonstrating the power of computers to do complex (and apparently random) calculations. Other graphics showed a simulated Mondrian and the iconic decreasing squares spiral that appeared on the exhibition's poster and book. The Boeing Corporation exhibited their use of wireframe graphics.
|
 |
by Cory Doctorow on (#12HJA)
In Investigatory Powers Bill: technology issues, the UK Parliament's Science and Technology select committee takes the government to task for its signature mass surveillance law, the "Snoopers Charter" whose provisions are so broad and vague that companies can't figure out how much of their customers' data they're supposed to be storing, and whether they're meant to be backdooring all the crypto they distribute. (more…)
|
 |
by Mark Frauenfelder on (#12H8W)
https://youtu.be/Qu3xxq5F3GwHere's behind-the-scenes footage of Jack Nicholson muttering, running in place, and taking practice chops in preparation for the famous "Here's Johnny!" scene in The Shining.[via]
|
 |
by Cory Doctorow on (#12ECP)
Years before the complaints from Flint's citizenry about their water provoked action from the state, Governor Rick Snyder spent $440,000 to supply better water to the GM factory, where the new water supply was corroding the car parts on the assembly line. (more…)
|
 |
by Rob Beschizza on (#12ECC)
This video depicts an angry cop lying about the law—"it's illegal to take photographs of me"—then, after he confiscates the camera but forgets to turn it off, his discussion with a fellow officer about now to "cover our ass." The Hartford Courant reports they're in some superficial degree of trouble over this, which is a start.Michael Picard, 27, of East Hartford, was charged with creating a public disturbance and reckless use of the highway for the Sept. 11 incident in which a trooper can be heard saying on a recording of the encounter, "We gotta cover our asses."
|
 |
by Xeni Jardin on (#12CNZ)
How cool of an internet-age entertainer is Louis C.K.? Here's what I got in my inbox this morning, as a subscriber to his email updates: (more…)
|
 |
by Xeni Jardin on (#12CHF)
In his weekly address, President Barack Obama this week pledged $4 billion in federal funding for computer science education in schools throughout the nation. (more…)
|
 |
by Rob Beschizza on (#12BV0)
80 percent of Chicago PD dashcam videos have been tampered with or otherwise damaged, according to technicians' reports, with audio missing due to 'intentional destruction' in many cases.Radley Balko: At minimum, intentionally destroying dash-cam equipment is destruction of public property. You could argue that it’s also tampering with or destroying evidence, particularly if there’s proof that it was done after a shooting or other major incident. [state’s attorney Anita] Alvarez tried to imprison a woman for recording the alleged harassment she received from police while attempting to file a report alleging sexual assault by another police officer. But when cops tamper with evidence of a police shooting of an unarmed man, all she can say is that it’s “frustrating†and that she’d “prefer to have the audio�The lack of consequences is the thing. This goes for everything from internet comment trolls right up to killer cops.
|
 |
by Cory Doctorow on (#12BN1)
The Gulfstream, tail number N977GA, was given permission to land in and fly over Denmark, and spent some time parked in Copenhagen, waiting to snatch Edward Snowden and kidnap him to America. (more…)
|
 |
by Boing Boing's Store on (#12B37)
No big deal, but you’re kind of a champion. You’ve used your fingertips to dominate the online competition. And now it’s time to take the hammer to the next level. With this development pack that’s now 87% off you can actually design the very kinds of games that you’re used to playing and crushing like a boss. But you could be the one in charge. You don’t have to have a single minute of coding experience to get going, that’s how easy this is. You’ll be a master in no time, winning the design game.Construct 2 is a super user friendly development engine that lets its users build games with zero programming experience. This pack offers over 423 lectures and 34 hours of content. That’s a lot of learning on your hands. From total scratch you’ll start from the basics and work your way up with this visual, interactive content to create 60 games that you can add to your portfolio. Using Photoshop you’ll tackle artwork and design and be learning all the while from an actual professional builder who’s released dozens of successful games.Being a game designer totally sounds like the dream job, and now it could be yours. After plowing through this pack of classes you’ll have a rad portfolio to show new employers, or impress the one you already have. For 87% off, that’s a pretty solid investment in the future of your awesome career. Check out the link below for details on all this amazing content.
|
 |
by Xeni Jardin on (#12A2S)
Sensitive electronic files from America’s biggest police union were posted online this week after a hacker breached the Fraternal Order of Police website. The ill-gotten dump includes officers' names and addresses, message board posts bashing Barack Obama, and details of eyebrow-raising contracts made between the union and city authorities. (more…)
|
by Mark Frauenfelder on (#126C0)
See sample pages of Dinomania at Wink.Cartoonist Winsor McCay was best known as the creator of the hallucinatory Little Nemo in Slumberland and Dreams of the Rarebit Fiend newspaper comic strips. Fewer people know that he was also the creator of the first animated dinosaur to appear in the movies (Gertie the Dinosaur, 1914). But hardly anyone knows that when McCay died in 1934, he was at work on a new comic strip called Dino, about a dinosaur that awakens after sleeping for 65-million years and befriends a young girl and her brother in New York City.One person who knows is McCay historian Ulrich Merkl, who has put together a massive, astounding book about McCay and his influence in depictions of rampaging dinosaurs, robots, apes, and monsters in popular culture. Every page is loaded with eye-popping art from the early 20th century, much of it never reprinted before now. People of that era were just as hungry for city-destroying cinematic behemoths as we are today, and Merkl convincingly makes the case that it was McCay who whetted our appetite for them. If you like illustrations from the 1900s, you will go ape over Dinomania.Dinomania: The Lost Art of Winsor McCay, The Secret Origins of King Kong, and the Urge to Destroy New York by Ulrich MerklFantagraphics2015, 304 pages, 11.9 x 15.9 x 1.2 inches$54 Buy one on Amazon
 |
by Mark Frauenfelder on (#129ER)
On Reddit, OmerRAnderson explains how to remove people from a photo. The idea is to put a camera on tripod and take several pictures every ten seconds or so over the course of a few minutes or more. Then open Photoshop and go to File > Scripts > Statistics, and select "median." This operation will remove the things that don't appear in every photo, leaving only the things that didn't move.
|
 |
by Mark Frauenfelder on (#129D0)
Fox News invited bullshitting fraudster Wayne Simmons to appear on its "news" programs over 100 times posing as a CIA operative. Based on his hawkish proclamations, the Pentagon hired Simmons as a shill analyst to propagandize for them. Now that Simmons has been exposed, arrested, and charged with with multiple counts of fraud, he will never appear on Fox News again, but the lies he told on the network will forever be regarded as gospel truth by fear-addicted Fox TV viewers.From Rolling Stone:Simmons claimed to have spent 27 years with the CIA, but Paul Nathanson, the assistant U.S. attorney prosecuting the case, said in a court filing that Simmons "never had any association whatsoever with the CIA." (The CIA declined to comment – as a rule, it never confirms or denies agents – but said it is "working closely with the Justice Department on this matter.") Instead, prosecutors say Simmons spent those 27 years doing just about everything else: He ran a limousine service, a gambling operation and an AIDS-testing clinic; worked for a hot-tub business, a carpeting company and a nightclub; and briefly played defensive back for the New Orleans Saints. Along the way, he accrued criminal convictions, including multiple DUIs, plus charges for weapons possession and assault, and an arrest for attacking a cabdriver in Annapolis, Maryland, in 2007. "Fuck you, you can't do shit to me – do you know who I am?" Simmons told a cop, according to a police report, before insisting that he was CIA, and that the cabbie, who was Pakistani, had a bomb. A police dog found no explosives, and a CIA representative told the cops to take whatever actions they deemed necessary.
|
 |
by Rob Beschizza on (#1294T)
The FBI has released footage that shows militiaman LaVoy Finicum's death at the hands of law enforcement officers manning a roadblock.In the video, Finicum's vehicle tries to evade the block only to plunge into a roadside snowbank after narrowly missing one of the officers manning it. He jumps out the car with his hands up, but keeps moving and reaches into his pocket. Someone shoots him and he falls to the snow.The 8-minute version is above. The confrontation begins at about 5:30m. They also published a longer tape of the event. The moment when Finicum is shot is embedded below. https://www.youtube.com/watch?v=xvzzyNFFIWc&feature=youtu.beOne one hand, his movements seem more confused than aggressive. On the other hand, he's an armed man, running around and reaching for his pockets after almost mowing a guy down at a roadblock. He did not have his hands in the air when he was shot (as at least one witness claimed) but he didn't have his piece out, either.What are the key facts, legally speaking?
|
 |
by Cory Doctorow on (#128W5)
They're handmade and the tiny mountains change color based on the color of the drink you serve in them, come in a gorgeous gift box, but they're also a whopping $88 each. (more…)
|
 |
by Rob Beschizza on (#128JX)
In 2004, a more legible typeface, Clearview, was approved to improve America's road signs. But after a decade of use, U.S. Federal Highway Administration has decided to return to the old typeface, publicly available as Highway Gothic. The reasoning isn't clear—they claim that it's actually more legible than Clearview, but are yet to explain why or offer research to back up the decision. Highway Gothic, designed in the 1940s, has peculiarities held to compromise its legibility. Clearview's letter forms were designed to be visible at greater distances and under less favorable lighting and weather conditions.“Helen Keller can tell you from the grave that Clearview looks better,†(designer) Meeker says. At the time, the FHWA agreed. In its 2004 approval memo, the agency noted that Clearview boosted highway-sign legibility for drivers traveling at 45 miles per hour by 80 feet of reading distance—or 1.2 seconds of bonus reading time… From the start, Clearview was greeted as a civic, social, and design success. Around 30 states have adopted the font, making it arguably the dominant design paradigm on U.S. roads. Print magazine called it one of the 10 typefaces of the decade in 2010. The Clearview typeface family was the first digital font ever acquired by the Cooper-Hewitt, Smithsonian Design Museum. People behind the font spoke about it with swagger.One possibility is that Clearview must be licensed on a per-user basis, making it too expensive. Also mentioned is its resemblance to other official signage typefaces such as Transport. It may, therefore, be insufficiently exceptional for official U.S. tastes.How about Papyrus, guys?
|
 |
by Boing Boing's Store on (#127JS)
You throw this drone up into the air, and it’s gone. OK, not really, but it really might look that way. It’s sky blue and will indeed appear to disappear. That’s what makes it awesome. This sunny-day stealth is going for 50% off right now and if you’re going to get a drone, which you totally should because they’re awesome, make it this tiny blue and white beast. Is that a cloud? Or is that the awesome, picture-taking flying machine that you can control with your hands? Only you can say.Unlike other drones, this nano actually has eight frequency points which means it really knows boundaries. It won’t crash or bump into anything around it while in the air, even when it’s flying with other drones in a pack. It has 6-axis gyro technology and calibration for maximum stability and maneuverability. It can even do 360 degree flips like a boss. The LED lights indicate which channel it’s on and because of its super sensitive design it can cut tight corners and navigate crazy narrow spaces. It’s quick and easy to charge up and once the battery is locked and loaded, you’ve got nearly ten minutes of fly time.[embed]https://youtu.be/SALW315JrtI[/embed]Coolest of all? This drone’s a team player and doesn’t like to fly solo. It’s actually designed to fly in a pack of other drones so call up your friends and throw up a whole flock of flying cameras. It’s 50% off right now so you could even stock up yourself. Check out the link below for even more details, plus a picture of this little high tech flyer in action.
|
by Cory Doctorow on (#125MS)
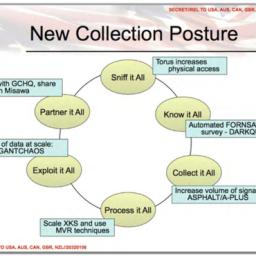
“I’d tell you, but I’d have to kill you.†This is what I shout at the TV (or the Youtube window) whenever I see a surveillance boss explain why none of his methods, or his mission, can be subjected to scrutiny. I write about surveillance, counter surveillance, and civil liberties, and have spent a fair bit of time in company with both the grunts and the generals of the surveillance industry, and I can always tell when one of these moments is coming up, the flinty-eyed look of someone about play Jason Bourne. The stories we tell ourselves are the secret pivots on which our lives turn.So when Laura Poitras approached me to write a piece forthe Astro Noise book and offered me access to the Snowden archive forthe purpose, I jumped at the opportunity.Fortuitously, the Astro Noise offer coincided perfectly with anotheroffer, from Laurie King and Leslie Klinger. Laurie is a bestselling Holmes writer; Les is the lawyer who won the lawsuit that put Sherlock Holmes in the public domain, firmly and unequivocally. Since their legal victory, they've been putting together unauthorized Sherlock anthologies, and did I want to write one for"Echoes of Holmes," the next one in line?The two projects coincided perfectly. Holmes, after all, is the masterof HUMINT, (human intelligence), the business of following peoplearound, getting information from snitches, dressing up in putty nosesand fake beards... Meanwhile, his smarter brother Mycroft is acorpulent, sedentary presence in the stories, the master of SIGINT(signals intelligence), a node through which all the intelligence ofthe nation flows, waiting to be pieced together by Mycroft and hisenormous intellect. The Mycroft-Sherlock dynamic perfectly embodies the fraternal rivalry between SIGINT and HUMINT: Sherlock chases all around town dressed like an old beggar woman or similar ruse, catches his man and hands him over to Scotland Yard, and then reports in to Mycroft, who interrupts him before he can get a word out, arching an eyebrow and saying, "I expect you found that it was the Bohemian stable-hand all along, working for those American Freemasons who were after the Sultan's pearls, was it not?"In 2014, I watched Jennifer Gibson from the eminent prisoners’ rights group Reprieve talking about her group's project to conduct a census of those killed by US drone strikes in Yemen and Pakistan. The CIA conducts these strikes, using SIGINT to identify mobile phones belonging to likely targets and dispatch killer drones to annihilate anything in their vicinity. As former NSA and CIA director Michael Hayden once confessed: "We kill people based on metadata."But the CIA does not specialize in SIGINT (that's the NSA's job). Formost of its existence, the CIA was known as a HUMINT agency, the mastersof disguise and infiltration..That was the old CIA. The new CIA is just another SIGINT agency. Signals Intelligence isn’t just an intelligence methodology, it’s a great business. SIGINT means huge procurements -- servers, administrators, electricity, data-centers, cooling -- while HUMINT involves sending a lot of your friends intoharm's way, potentially never to return. We are indeed in the “golden age of SIGINTâ€. Despite security services' claims that terrorists are "going dark" with unbreakable encryption, the spooks have done much to wiretap the whole Internet. The UK spy agency GCHQ really tipped their hand when they called their flagship surveillance program "Mastering the Internet." Not "Mastering Cybercrime," not "Mastering Our Enemies." Mastering the *Internet* -- the very same Internet that everyone uses, from the UK's allies in the Five Eyes nations to the UK Parliament to Britons themselves. Similarly, a cursory glance at the logo for the NSA’s Special Source Operations -- the fiber-tapping specialists at the NSA -- tells the whole story. These mass surveillance programs would likely not have withstood public scrutiny. If the NSA’s decision to launch SSO had been attended by a nightly news broadcast featuring that logo, it would have been laughed out of the room. The program depended on the NSA by telling its story to itself, and not to the rest of us. The dotcom boom would have been a very different affair if the majorlegislative debate of the day had been over whether to allow thesurveillance agencies of Western governments to monitor all the fiber cables, and harvest every click and keystroke they can legally lay claim to, parcel it into arbitrary categories like “metadata†and “content†to decide what to retain indefinitely, to and run unaccountable algorithms on that data to ascribe secret guilt.As a result, the entire surveillance project has been undertaken insecrecy, within the bubble of people who already think that surveillanceis the answer to virtually any question. The surveillance industry is a mushroom, grown in dark places, and it has sent out spores into every corner of the Internet, which have sprouted their own surveillance regimes. While this was happening, something important was happening to theInternet: as William Gibson wrote in 2007's "Spook Country, "cyberspaceis everting" -- turning inside out. Computers aren’t just the things in our bags in the trunks of our cars. Today, our cars are computers. This is why Volkswagen was able to design a car that sensed when it was undergoing regulatory inspection and changed its behavior to sneak through tests. Our implanted defibrillators are computers, which is why Dick Cheney had the wireless interface turned off on his defibrillator prior to its implantation. Everything is a networked computer.Those networked devices are an attack surface that is available to theNSA and GCHQ's adversaries -- primarily other governments, as well asnon-government actors with political ambitions -- and to gardenvariety criminals. Blackmailers, voyeurs, identity thieves andantisocial trolls routinely seize control over innocents' computers andattack them in every conceivable way. Like the CIA and its drones, theyoften don't know who their victims are: they find an exploit, write ascript to find as many potential victims as possible, and harvest them.For those who are high-value targets, this lurking insecurity is even more of a risk -- witness the recent takeover of the personal email accounts of US Director of National Intelligence James Clapper by a group of self-described teenagers who previously took over CIA Director John Brennan's email account.This is the moment when the security services could shine. We needcyber defense and we need it badly. But for the security services toshine, they'd have to spend all their time patching up the leaky boat ofnetworked security, while their major project for a decade and more hasbeen to discover weaknesses in the network and its end-points andexpand them, adding vulnerabilities that they can weaponize againsttheir adversaries -- leaving these vulnerabilities wide open for theiradversaries to use in attacking *us*. The NSA and GCHQ have weaponized flaws in router operating systems, rather than telling the vendors about these flaws, leaving the world’s electronic infrastructure vulnerable to attack by the NSA and GCHQ’s adversaries. Our spies hack core routers and their adversaries' infrastructure, but they have made themselves reliant upon the continuing fragility and insecurity of the architectures common to enemy and ally alike, when they could have been making us all more secure by figuring out how to harden it. The mission of making it as hard as possible for the enemy to attack us is in irreconcilable tension with the mission of making it as easy as possible for our security services to attack their adversaries.There isn't a Bad Guy Internet and a Good Guy Internet. There's no Bad Guy Operating System and Good Guy Operating System. When GCHQ discovers something breakable in a computer system that Iranians depend upon, they've also discovered something amiss that Britons rely upon. GCHQ can't keep that gap in Iran's armor intact without leaving an equally large gap open in our own armor. For my Sherlock story, I wanted to explore what it means to have asecurity methodology that was all attack, and precious little defense, particularly one that proceeded in secret, without any accountability or even argumentfrom people who thought you were doing it all wrong.The DocumentsThough I reviewed dozens of unpublished documents from the Snowdenarchive in writing my story, I relied upon three documents, two of which we are releasing today.First, there's the crux of my Sherlock story, drawn from a March 2010 GCHQ document titled "What's the worst that could happen?" marked "TOP SECRET STRAP 1." This is a kind of checklist for spies who are seeking permission to infect their adversaries' computersor networks with malicious software.It's a surprising document in many regards. The first thing that caughtmy eye about it is the quality of the prose. Most of the GCHQ documentsI've reviewed read like they were written by management consultants, dryand anodyne in a way that makes even the famously tortured prose of themilitary seem juicy by comparison. The story the authors of those documents are telling themselves is called something like, “Serious grownups, doing serious work, seriously.â€"What's the worst..." reads like the transcript of a lecture by afascinating and seasoned mentor, someone who's seen all the pitfalls andwants to help you, their protege, navigate this tricky piece of theintel business without shooting yourself in the foot.It even tells a kind of story: we have partners who help us with ourmalware implantation. Are they going to help us with that business inthe future if their names get splashed all over the papers? Remember, there are clever people like you working for foreign governments -- they're going to try and catch us out! Imagine what might happen if one of our good friends got blamed for what we did -- or blamed us for it! Let's not forget the exploits themselves: our brilliant researchers quietly beaver away, finding the defects that the best and the brightest programmers at, say, Apple and Microsoft have left behind in their code: if you get caught, the companies will patch the vulnerabilities and we will lose the use of them forever.On it goes in this vein, for three pages, until the very last point:“Who will have direct access to the data resulting from the operationand do we have any control over this? Could anyone take action on itwithout our agreement, eg could we be enabling the US to conduct adetention op which we would not consider permissible?â€That's where the whole thing comes to something of a screeching halt.We're not talking about Tom Clancy net-wars fantasies anymore -- nowwe're into the realm of something that must haunt every man and woman of good will and integrity who works in the spy agencies: the possibility that a colleague or ally, operating without oversight or consequence, might descend into barbarism based on something you did. Reading this, I thought of the Canadian officials who incorrectly told US authorties that Maher Arar, a Canadian citizen of Syrian origin was suspected of being connected to Al Qaeda.Arar was detained by the United States Immigration and Naturalization Service (INS) during a stopover in New York on his way home from a family vacation in Tunis. The Americans, acting on incomplete intelligence from the Canadian Royal Canadian Mounted Police (RCMP), deported Arar to Syria, a country he had not visited since his move to Canada, and which does permit the renunciation of citizenship. Arar claims he was tortured during his imprisonment which lasted almost a year, and bombarded with questions from his torturers that seemed to originate with the US security services. Finally, the Syrian government decided that Arar was innocent of any terrorist connections and let him go home to Canada. The US authorities refused to participate in the hearings on the Arar affair and the DHS has kept his family on the no-fly list[[TK]]. p* Why did Syrian officials let him go? "Why shouldn't we leave him to go? We thought that would be a gesture of good will towards Canada, which is a friendly nation. For Syria, second, we could not substantiate any of the allegations against him," says Moustapha. He added that the Syrian government now considers Arar completely innocent.Is this what the unnamed author of this good-natured GCHQ document meantby "a detention op which we would not consider permissible?" TheCanadian intelligence services apparently told their US counterpartsearly on that they'd been mistaken about Arar, but when a serviceoperates with impunity, in secret, it gets to steamroller on, withoutletting facts get in the way, refusing to acknowledge its errors.The security services are a system with a powerful accelerator and inadequate brakes. They’ve rebranded “terrorism†as an existential risk to civilization (rather than a lurid type of crime). The War on Terror is a lock that opens all doors. As innumerable DEA agents have discovered, the hint that the drug-runner you’re chasing may be funding terror is a talisman that clears away red-tape, checks and balances, and oversight.The story of terrorism is that it must be stopped at all costs, that there are no limits when it comes to the capture and punishment of terrorists. The story of people under suspicion of terrorism, therefore, is the story of people to whom no mercy is due, and of whom all cunning must be assumed.Within the security apparatus, identification as a potential terrorist is a life sentence, a “FAIR GAME†sign taped to the back of your shirt , until you successfully negotiate a kafka-esque thicket of secretive procedures and kangaroo courts. What story must the author of this document have been telling themself when they wrote that final clause, thinking of someone telling himself the DIE HARD story, using GCHQ’s data to assign someone fair game status for the rest of their life? Holmes stories are perfectly suited to this kind of problem. From "A Scandal in Bohemia" to "A Study in Scarlet," to "The Man With the Twisted Lip" Holmes's clients often present at his doorstep wracked with guilt or anxiety about the consequences of their actions. Often as not, Holmes's solution to their problems involves not just unraveling the mystery, but presenting a clever way for the moral question to be resolved as well. The next document is the "HIMR Data Mining Research Problem Book," afascinating scholarly paper on the methods by which the massivedata-streams from the deep fiber taps can be parsed out intoidentifiable, individual parcels, combining data from home computers,phones, and work computers. It was written by researchers from the Heilbronn Institute for Mathematical Research in Bristol, a â€partnership between the UK Government Communications Headquarters and the University of Bristol.†Staff spend half their time working on public research, the other half is given over to secret projects for the government. The Problem Book is a foundational document in the Snowden archive, written in clear prose that makes few assumptions about the reader’s existing knowledge. It likewise makes few ethical assertions about its work, striking a kind of academic posture in which something is â€good†if it does some task efficiently, regardless of the task. It spells out the boundaries on what is and is not â€metadata†without critical scrutiny, and dryly observes that â€cyber†is a talisman -- reminiscent of â€terrorist†-- that can be used to conjure up operating capital, even when all the other government agencies are having their budgets cut. The UK government has recognized the critical importance of cyber to our strategic position: in the Comprehensive Spending Review of 2010, it allocated a significant amount of new money to cyber, at a time when almost everything else was cut. Much of this investment will be entrusted to GCHQ, and in return it is imperative for us to use that money for the UK’s advantage.
 Some of the problems in this book look at ways of leveraging GCHQ’s passive SIGINT capabilities to give us a cyber edge, but researchers should always be on the look-out for opportunities to advance the cyber agenda.
The story the Problem Book tells is of scholars who’ve been tasked with a chewy problem: sieving usable intelligence out of the firehoses that GCHQ has arogated to itself with its fiber optic taps.Somewhere in that data, they are told, must be signatures that uniquely identify terrorists. It’s a Big Data problem, and the Problem Book, dating to 2010, is very much a creature of the first rush of Big Data hype. For the researchers, the problem is that their adversaries are no longer identifiable by their national affiliation. The UK government can’t keep on top of its enemies by identifying the bad countries and then spying on their officials, spies and military. Now the bad guys could be anyone. The nation-state problem was figuring out how to spy on your enemies. The new problem is figuring out which people to spy on."It is important to bear in mind that other states (..) are not bound by the same legal framework and ideas of necessity and proportionality that we impose on ourselves. Moreover, there are many other malicious actors in cyberspace, including criminals and hackers (sometimes motivated by ideology, sometimes just doing it for fun, and sometimes tied more or less closely to a nation state). We certainly cannot ignore these non-state actors". The problem with this is that once you accept this framing, and note the happy coincidence that your paymasters just happen to have found a way to spy on everyone, the conclusion is obvious: just mine all of the data, from everyone to everyone, and use an algorithm to figure out who’s guilty.The bad guys have a Modus Operandi, as anyone who’s watched a cop show knows. Find the MO, turn it into a data fingerprint, and you can just sort the firehose’s output into â€terrorist-ish†and â€unterrorist-ish.†MoMOnce you accept this premise, then it’s equally obvious that the whole methodology has to be kept from scrutiny. If you’re depending on three â€tells†as indicators of terrorist planning, the terrorists will figure out how to plan their attacks without doing those three things.This even has a name: Goodhart's law. "When a measure becomes a target, it ceases to be a good measure." Google started out by gauging a web page’s importance by counting the number of links they could find to it. This worked well before they told people what they were doing. Once getting a page ranked by Google became important, unscrupulous people set up dummy sites (“link-farmsâ€) with lots of links pointing at their pages. The San Bernardino shootings re-opened the discussion on this problem. When small groups of people independently plan atrocities that don’t require complicated or unusual steps to plan and set up, what kind of data massaging will surface them before it’s too late?Much of the paper deals with supervised machine learning, a significant area of research and dispute today. Machine learning is used in "predictive policing" systems to send cops to neighborhoods where crime is predicted to be ripening, allegedly without bias. In reality, of course, the training data for these systems comes from the human-directed activity of the police before the system was set up. If the police stop-and-frisk all the brown people they find in poor neighborhoods, then that's where they'll find most of thecrime. Feed those arrest records to a supervised machine algorithm andask it where the crime will be and it will send your officers back tothe places where they're already focusing their efforts: in other words,"predictive policing" is great at predicting what the police will do,but has dubious utility in predicting crime itself.The part of the document I was most interested in was the section onreading and making sense of network graphs. They are the kind of thing you’d use in a PowerPoint slide when you want to represent an abstraction like "the Internet". Network graphs tell you a lot about the structures oforganizations, about the relative power relationships between them. Ifthe boss usually communicates to their top lieutenants after beingcontacted by a trusted advisor, then getting to that advisor is a greatway to move the whole organization, whether you're a spy or a sales rep.The ability of data-miners to walk the social and network graphs oftheir targets, to trace the "information cascades" (that is, to watchwho takes orders from whom) and to spot anomalies in the network andzero in on them is an important piece of the debate on "going dark." Ifspies can look at who talks to whom, and when, and deduce organizationalstructure and upcoming actions, then the ability to read the contentof messages -- which may be masked by cryptography -- is hardly themake-or-break for fighting their adversaries.This is crucial to the debate on surveillance. In the 1990s, there was a seminal debate over whether to prohibit civilian access to working cryptography, a debate that was won decisively for the side of unfettered access to privacy tools. Today, that debate has been renewed. David Cameron was re-elected to the UK Prime Minister's office after promising to ban strong crypto, and the UK government has just introduced a proposed cryptographic standard designed to be broken by spies. The rubric for these measures is that spies have lost the ability to listen in on their targets, and with it, their ability to thwart attacks. But as the casebook demonstrates, a spy's-eye view on the Internet affords enormous insight into the activities of whole populations -- including high-value terrorism suspects.The Problem Book sets up the Mycroftian counterpoint to Sherlock's human intelligence -- human and humane, focused on the particulars of each person in his stories.Sherlock describes Mycroft as an all-knowing savant: The conclusions of every department are passed to him, and he is the central exchange, the clearinghouse, which makes out the balance. All other men are specialists, but his specialism is omniscience.While Sherlock is energized by his intellectual curiosity, his final actions are governed by moral consequences and empathy. Mycroft functions with the moral vacuum of a software: tell him to identify anomalies and he'll do it, regardless of why he's been asked or what happens next. Mycroft is a Big Data algorithm in human form.The final document I relied upon in the story is one we won't bepublishing today: an intercepted transcript of a jihadi chat roomThis document isn't being released because there were many people inthat chat room, having what they thought was an off-the-recordconversation with their friends. Though some of them were espousingextreme ideology, mostly they were doing exactly what my friends and Idid when I was a teenager: mouthing off, talking about our love lives,telling dirty jokes, talking big.These kids were funny, rude, silly, and sweet -- they were lovelorn andfighting with their parents. I went to school with kids like these. Iwas one of them. If you were to judge me and my friends based onour conversations like these, it would be difficult to tell usapart from these children. We all talked a big game, we all fretted aboutmilitary adventurism, we all cursed the generals who decided thatcivilian losses are acceptable in the pursuit of their personal goals.I still curse those generals, for whatever it's worth.I read reams of these chat transcripts and I am mystified at their value to national security. These children hold some foolish beliefs, but they're not engaged in anything more sinister than big talk and trash talk. Most people -- including most people like these kids -- are not terrorists. You can tell, because we're not all dead. An indiscriminate surveillance dragnet will harvest far more big talkers than bad guys. Mass surveillance is a recipe for creating an endless stream of Arars, and each Arar serves as inspiration for more junior jihadis.In my fiction, I've always tried to link together real world subjects of social and technological interest with storytelling that tries to get into the way that the coming changes will make us feel. Many readers have accused me of prdicting the future because I've written stories about mass surveillance and whistleblowers.But the truth is that before Snowden, there was Wikileaks and Chelsea Manning, and Bill Binney and TK before them, and Mark Klein before them. Mass surveillance has been an open secret since the first GW Bush administration, and informed speculation about where it was going was more a matter of paying attention to the newspaper than peering into a crystal ball.Writing a Sherlock Holmes story from unpublished leaks was a novel experience, though, one that tied together my activist, journalist and fiction writing practices in a way that was both challenging and invigorating. In some ways, it represented a constraint, because once I had the nitty-gritty details of surveillance to hand, I couldn't make up new ones to suit the story. But it was also tremendous freedom, because the mass surveillance regimes of the NSA and GCHQ are so obviously ill-considered and prone to disastrous error that the story practically writes itself.I worry about "cybersecurity," I really do. I know that kids can docrazy things. But in the absence of accountability and independentscrutiny, the security services have turned cyberspace into abattleground where they lob weapons at one another over our heads, andwe don't get a say in the matter. Long after this round of the war onterror is behind us, we'll still be contending with increasingly smallcomputers woven into our lives in increasingly intimate, life-or-deathways. The the parochial needs of spies and the corporations that supplymustn't trump the need for a resilient electronic nervous system for thetwenty first century.Henrik Moltke contributed research to this story. What-Is-the-Worst-That-Can-Happen-March-2010 (PDF) What-Is-the-Worst-That-Can-Happen-March-2010 (Text) Problem-Book-Redacted (PDF) Problem-Book-Redacted (Text)
 |
by David Pescovitz on (#125CC)
Watch legendary jazz drummer Elvin Jones, known for his playing with the John Coltrane Quartet and, of course, the Elvin Jones Jazz Machine, construct a killer post-bop beat, c. 1979. (Thanks, Jordan Kurland!)
|
 |
by Rob Beschizza on (#125AF)
https://soundcloud.com/beschizza/433-8-bit-hi-nrg-chiptune-bloopcore-remixYou're welcome.
|
 |
by Cory Doctorow on (#1250S)
Rob Joyce runs the NSA's Tailored Access Operations group, the spies who figure out how to hack systems, publishing a spook's version of the Skymall catalog, filled with software and hardware that other spies can order for use. (more…)
|
 |
by Cory Doctorow on (#124SX)
Orange County has many claims to fame: Richard Nixon, the S&L scandal, subprime boiler-rooms, Disneyland, an airport honoring a cowboy named Marion, and now, the revelation that its police force secretly uses low-flying surveillance aircraft to break the encryption of thousands of cellphone users, track their movements, and intercept their communications. (more…)
|
 |
by Boing Boing's Store on (#123T6)
One pocket to rule them all. Now, if you have a wallet, you have a battery. This slim, powerful charger is a paragon of efficiency and can make your mobile life a heckuva lot easier. For 66% off right now you can be the proud owner of this ultra thin battery that slides right into your wallet and can charge up any of your devices. Having a white cord hanging out of your back pocket isn’t exactly the greatest look, so switch to this charger and save the cords for when you’re on the couch. Today, you’re on the go.Right off the bat, you’ll notice this thing’s fit and feel. It’s crazy thin, no larger than five credit cards together which would fit into any wallet. It’s housed in billet aluminum for maximum sleekness and durability, which is mandatory if it’s going to get sat on in your back pocket. With its tiny flip-out charging cables, you can juice up any device at a lightning speed of one percent every minute. Never worry about your battery dying at a restaurant, party or event again. It’s also available with a micro USB cord, if that’s more your speed.This is charging perfection in an aluminum nutshell. Once you’ve got this resting comfortably and inconspicuously in your wallet, you’ll never need or want to use those cords again. The device itself charges up fast with a long lasting battery too so you’ll never go without. Your wallet can become a power hub for 66% off and your friends will be begging to use it when you’re out and about.
|
 |
by Xeni Jardin on (#122RN)
https://youtu.be/2GjW5HSOpiUThey say this 28-year-old guy tossed 2 tomatoes at presidential candidate Donald Trump, during the noted racist shitbag's Iowa campaign stop. He missed. But his t-shirt slogan did not. (more…)
|
 |
by Cory Doctorow on (#122QW)
Catherine Elhoffer from Elhoffer Design created these awesome "The Force, Fashioned" dresses that riff off the costume designs in The Force Awakens. (more…)
|
 |
by Xeni Jardin on (#122K5)
https://youtu.be/Qv0eWN8v_tgThis video is pretty rabid Reddit rage-fodder today. Certainly, selective video edits by someone with a point to make can be damning where nothing wrong has been done, but--come on. This looks pretty bad. [From Brandon Farley (MischiefMaker37), YouTube » Reddit]Looks like there are a bunch of these newly out, via Reddit. But it's been brewing for weeks, or months, really. Vox has a good explainer here. I am not the comedy police, so I do not know.
|
 |
by Xeni Jardin on (#122GY)
Social media giant Facebook today reported sales and earnings that well exceeded Wall Street's expectations, as both the number of users and mobile ad dollars rose from October to December. (more…)
|
 |
by Mark Frauenfelder on (#121JR)
This foldable step stool is 11 inches high, and is only 1.5 inches thick when folded up. It has replaced a non-folding plastic step stool that we'd kept in on the floor in the closet. It's on sale at Amazon for $10.
|
 |
by Cory Doctorow on (#121DA)
Transylvania's Salina Turda themepark is housed in an ancient salt mine with millennia of history. Visitors use its vertical shafts to access vast underground salt caverns and lakes dotted with a concert hall, mini-golf courses, bowling alleys, and rowboats. (more…)
|
 |
by Cory Doctorow on (#121CX)
It's not just dissident Hong Kong booksellers who're being snatched -- China's snatch-squads have kidnapped expatriate dissidents (including those with foreign passports) from Sweden, Burma and Thailand. (more…)
|
 |
by Cory Doctorow on (#12140)
Despite the fact that it "takes the privacy and security of our members' information seriously," the health insurance company Centene can't find six unencrypted hard drives with 950,000 customers' private health data, addresses, dates of birth and social security data. (more…)
|
 |
by Ruben Bolling on (#1212C)
Follow @RubenBolling on Twitter and Facebook.Please join Tom the Dancing Bug's subscription club, the INNER HIVE, for early access to comics, and more. And/or buy Ruben Bolling’s new book series for kids, The EMU Club Adventures. Book One here. Book Two here. More Tom the Dancing Bug comics on Boing Boing! (more…)
|
 |
by Rob Beschizza on (#1210Y)
The Passport Index ranks passports according to their "power", defined around how many countries will let you in without a visa. British and American passports share the top spot. Meanwhile, a South Sudanese or Palestinian passport wouldn't get you into a candy store.Visa Free ScorePassports accumulate points for each visa free country that their holders can visit without a visa, or they can obtain a visa on arrival.Passport Power RankPassports are ranked based on their Visa Free Score. The higher the Visa Free Score, the better the Passport Power Rank.MethodologyThe country list is based on the 193 UN member countries and 6 territories (Macao, Kosovo, etc.) for a total of 199. Territories annexed to other countries such as Norfolk Island, French Polynesia, etc. are excluded. Data is based on research from publicly available sources, as well as information shared by government agencies.The best part of the site is the page where you can sort the passport cover images by color.
|
 |
by Cory Doctorow on (#120W0)
Obama wrote an op-ed in the Washington Post (bio: "Barack Obama is president of the United States") explaining his suite of penal reform policies, which begin with ending the barbaric practice of putting children into solitary confinement, deemed a form of torture, "an affront to our common humanity." (more…)
|
 |
by David Pescovitz on (#11YQD)
Classical nude statues at Italy's Capitoline Museum were covered up this week in anticipation of Iranian President Hassan Rouhani's visit. Some politicians and art critics called out the stupidity. From The Telegraph:The president’s aides were also reportedly anxious that he not be photographed too close to a giant bronze statue of the Roman emperor Marcus Aurelius on horseback.The Iranians objected to what one Italian newspaper delicately described as “the attributes†or genitalia of the huge horse, which dates from the second century AD.
|
 |
by Mark Frauenfelder on (#11YP4)
https://youtu.be/KY43Vytro60If you're a cop in Oregon, I guess the way to get promoted is to rear end your unmarked patrol car into a motorcycle and then violently kick the nonresistant rider with enough force to break his collarbone. It'll cost taxpayers $180,000 to settle the lawsuit against you, but that not your problem!
|
 |
by Cory Doctorow on (#11YNG)
Earlier this month, Ben "and Jerry's" Cohen spitballed with an MSNBC reporter about his idea for a Bernie Sanders ice-cream flavor: "Bernie's Yearning," a pint of mint with a disk of solid chocolate on the top, representing the fortunes of the 1%. Before you eat it, you use a spoon to smash the wealth and distribute it evenly through the pint. (more…)
|
 |
by David Pescovitz on (#11YKM)
D. Allan Drummond, the University of Chicago biologist who recently 3D printed and cast a fascinating model of a yeast cell dividing, also creates exquisite bronze sculptures of trilobites, marine arthropods that went extinct 250 million years ago. Images and video below.See more at Professor Drummond's Instagram feed.(via SciAm)
|