Reverse engineering Android apps reveals important security flaws
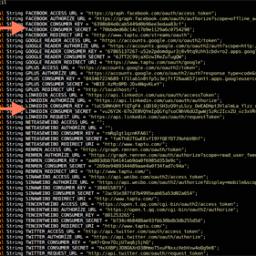 This story comes from CNet, who has dumbed the story down in a way that makes it a bit hard to understand [ed note: ironic]. But it appears security researchers have reverse engineered over 880,000 of the Android app store's 1.1M free apps, and found a number of important security concerns .
This story comes from CNet, who has dumbed the story down in a way that makes it a bit hard to understand [ed note: ironic]. But it appears security researchers have reverse engineered over 880,000 of the Android app store's 1.1M free apps, and found a number of important security concerns .The first concern is the existence of hard coded keys, which the article claims "username and password data -- which can then be used to steal user data or resources from entities such as Amazon and Facebook." That's not well explained, but that's CNet for you.
The second concern isn't so much a security issue as further evidence that the Android app store could use some better curating: the researchers discovered that roughly 25% of Android free apps are simply clones of other apps.
The researchers used a tool called "PlayDrone" which circumvents the App store's procedures to download apps and reverse engineer them to acquire source code. The source article at Columbia University is better , or PlayDrone yourself over at Github. A bit of nice work by researchers Jason Nieh and Nicolas Viennot.