
It's hard not to look at one of Samsung's flagship phablets without feeling a pang of nostalgia for Palm's products back in the day, stylus and graffiti handwriting recognition and all. Samsung bucked the trend as Steve Jobs defiantly maintained, "if your device has a stylus, you have failed." Instead, Samsung's Note line of devices use an integrated, touch-sensitive stylus to permit new applications and unlock new ways of interacting with software.
The Note is in its 5th incarnation in 2016.
Engadget has taken a look at it and finds it pretty compelling overall, despite changes that will turn off many: no microSD support, no swappable battery, a wimpy single speaker, and only 32GB and 64GB options.
Let's cut to the chase: This is the most attractive, most comfortable-feeling Galaxy Note that Samsung has ever made. ... The generous curve of the backplate and the trimmed-down bezels surrounding the 5.7-inch, Quad HD, Super AMOLED screen make the Note 5 much easier to hold than any of the previous-gen Notes, ... More importantly, the screen is an absolute champ under the sweltering summer sun. With brightness cranked up all the way, I had no trouble ... If you've fiddled with a Galaxy S6, you know exactly what to expect here. The Note 5 comes with a TouchWiz-ified version of Android 5.1.1, and once again, I appreciate the lighter touch Samsung has been taking with its software. It's not my favorite skin and I still think it pales in comparison to the stock Google Now Launcher, but I'm pleasantly surprised by how much less obnoxious TouchWiz is these days. All of Samsung's mainstay features are here, and they all work as well as you'd expect them to.
Other reviews are similar. Check them out at
Gizmodo and
Tech Times.
Forbes has discovered you can screw up your device by sticking the stylus in its receptacle the wrong way. So, don't do that then, dummy.
With the rise of mobile computing came a swell of frustration by people who preferred their fancy, personal devices to the locked-down devices (if any) provided for them at work. Eventually, corporations relented, opening the door to a plethora of "bring your own device" policies that IT staff detest owing to increased security risk and the unacceptable co-mingling of personal and private data.
We've been working in this environment for a few years now, and increasingly, tech directors are willing to speak out about this model's deficiencies. But users aren't unanimously happy with the compromises made either. One small example:
In an interesting test case in California, a worker is reported to be suing her former employer for invasion of privacy and wrongful termination of employment.
The person claimed they were sacked after deleting an app (Xora iPhone app) from her company-issued handset that she believed allowed her employer to spy on her. She claims the app tracked where she was - using the device GPS - including how fast she was driving, even when she wasn't working.
The Register takes a look at the pros and cons of what has become a pre-selection of pre-approved devices, i.e. "CYOD" or "choose your own device."
What about |.ers? Are you bringing your own device, or saddled with the corporate choice, or avoiding pocket computing all together? Which model worked the best for you?
Based on anonymized data collected from users of an app designed to check for a newly revealed vulnerability in many Android devices, Check Point has discovered that
at least one application currently in the Google Play store is exploiting the vulnerability to gain root access to the Android OS - and bypassing Google's security scans of Play applications to do so.
While the app was discovered installed on an infinitesimal percentage of devices checked by Check Point, it shows that the vulnerability caused by insecure OEM and cell carrier software meant to provide remote access to devices for customer service engineers has already been exploited by "legitimate" phone applications-and the method used to bypass Google's security checks could be used for more malicious purposes on millions of devices. And there's no easy way for Google or phone manufacturers alone to patch the problem.
At the Black Hat security conference in Las Vegas earlier this month, Check Point's Ohad Bobrov and Avi Bashan presented research into an Android vulnerability introduced by software installed by phone manufacturers and cellular carriers that could affect millions of devices. Labeled by Bobrov and Bashan as "Certifi-Gate," the vulnerability is caused by insecure versions of remote administration tools installed by the manufacturers and carriers to provide remote customer service-including versions of TeamViewer, CommuniTake Remote Care, and MobileSupport by Rsupport. These carry certificates that give them complete access to the Android operating system and device hardware. The applications are commonly pre-installed on Samsung, LG, and HTC handsets.
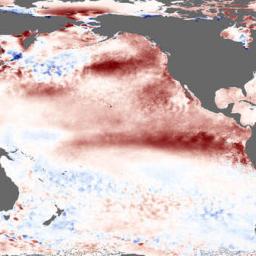
Scientists' understanding of the El Nino phenomenon - in which a reversal of warm and cool currents in the Pacific Ocean brings wet weather to America's West Coast and elsewhere while areas used to monsoon rainfall remain dry - is better than ever. But that hasn't helped our ability to accurately predict El Nino years, and of course even prediction does nothing for mitigating the sometimes disastrous effects.
El Nino-watchers at America's National Oceanic and Atmospheric Administration (NOAA) noted worrisome ENSO-related changes in both sea temperature and air pressure earlier this year. They declared the return of the Boy in March. Australia's Bureau of Meteorology decided to wait until May. Such forecasts can be wrong. Despite signs of the phenomenon last year, no monstrous event actually emerged. But during July the surface temperature of the central equatorial Pacific was almost 1C higher than expected, and its equivalent in the eastern Pacific was more than 2C above expectations. Among other things, that puts the temperatures in these areas well above the 26.5C minimum needed for the formation of tropical storms. Right on cue, on July 12th, six such cyclones spun in the Pacific-more than on any previous day in over four decades.
Mike Halpert, the deputy director of NOAA's Climate Prediction Centre, believes the current Nino could be among the strongest since records began in 1950. That one was responsible for 21,000 deaths and $36B in damages on houses, bridges, and culverts.
Time to get out the raincoats and umbrellas?
Adobe's Flash has earned a reputation for insecurity through a litany of vulnerabilities through the years since its inception in the late 1990s. But it hasn't made many friends among users, either, who are increasingly either turned off by bandwidth-sucking video advertisements, or are nervous that running Flash adverts leaves your machine open to all sorts of vulnerabilities.
Amazon.com is now coming around to that point of view as well. Since so many users either block or are fearful of flash adverts, the marketing juggernaut has decided to henceforth refuse to use them. Amazon is only one of many Internet sites, but it's a high profile one, and their refusal of Flash adverts may finally tip the market in a direction it should've headed long ago. Could this be the end of Adobe Flash?
 It's hard not to look at one of Samsung's flagship phablets without feeling a pang of nostalgia for Palm's products back in the day, stylus and graffiti handwriting recognition and all. Samsung bucked the trend as Steve Jobs defiantly maintained, "if your device has a stylus, you have failed." Instead, Samsung's Note line of devices use an integrated, touch-sensitive stylus to permit new applications and unlock new ways of interacting with software.
It's hard not to look at one of Samsung's flagship phablets without feeling a pang of nostalgia for Palm's products back in the day, stylus and graffiti handwriting recognition and all. Samsung bucked the trend as Steve Jobs defiantly maintained, "if your device has a stylus, you have failed." Instead, Samsung's Note line of devices use an integrated, touch-sensitive stylus to permit new applications and unlock new ways of interacting with software.
