Hackers are exploiting a platform-agnostic flaw to track mobile phone locations
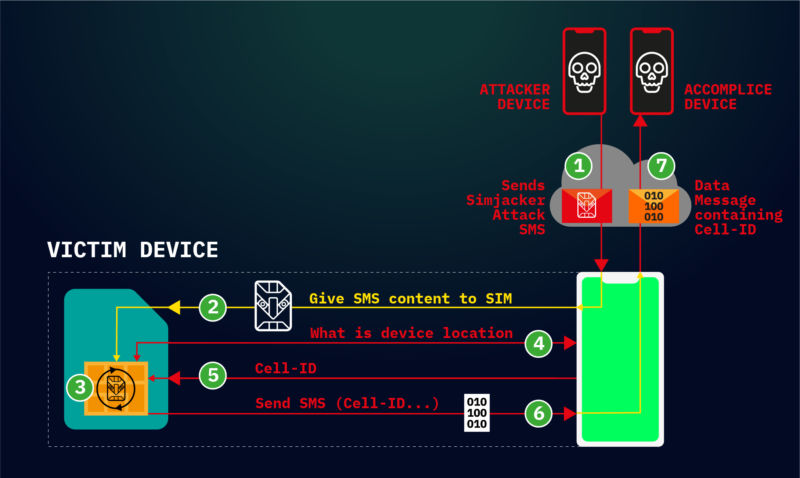
Enlarge / Simjacker attack flow. (credit: AdaptiveMobile Security)
Hackers are actively exploiting a critical weakness found in most mobile phones to surreptitiously track the location of users and possibly carry out other nefarious actions, researchers warned on Thursday.
The so-called Simjacker exploits work across a wide range of mobile devices, regardless of the hardware or software they rely on, researchers with telecom security firm AdaptiveMobile Security said in a post. The attacks work by exploiting an interface intended to be used solely by cell carriers so they can communicate directly with the SIM cards inside subscribers' phones. The carriers can use the interface to provide specialized services such as using the data stored on the SIM to provide account balances.
Simjacker abuses the interface by sending commands that track the location and obtain the IMEI identification code of phones. They might also cause phones to make calls, send text messages, or perform a range of other commands.
Read 13 remaining paragraphs | Comments