New Android vulnerability Strandhogg 2.0 exploits user trust
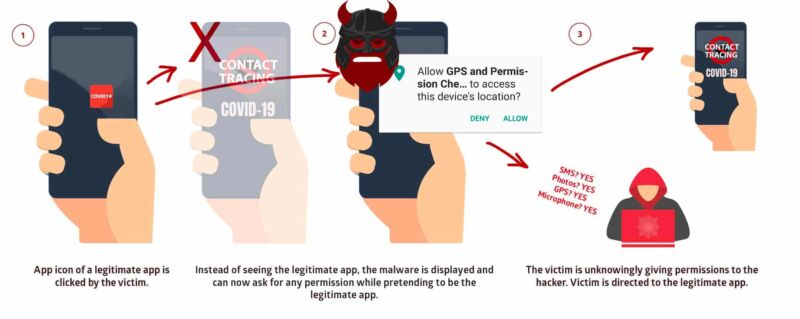
Enlarge / Strandhogg 2.0 can be thought of as the ultimate phishing attack. When the user taps a legitimate icon-which could be for email, camera, etc-the malware intercepts the tap and can present a copycat dialog instead. (credit: Promon)
A Norwegian infosec firm discovered a new Android vulnerability, which they've dubbed Strandhogg 2.0. Security firm Promon says "Strandhogg" is an old Norse strategy for coastline raids and abductions, and today's vulnerability is the "evil twin" of a similar one discovered in 2019.
The original Strandhogg used an Android feature called taskAffinity to hijack applications-by setting the taskAffinity of one of its activities to match the packageName of any other app, then setting allowTaskReparenting="true" in its own manifest, the Strandhogg app would be launched in place of the target app.
Imagine tapping the legitimate Gmail icon on your phone and getting what appears to be a legitimate login prompt, pixel-for-pixel identical with the one you'd see if your account had been logged off. Would you enter your credentials? If one of the free games or apps you or a child might have installed was a Strandhogg vessel, you just gave your credentials to an attacker-which might even launch the Gmail application itself immediately after testing your credentials, leaving no obvious sign you had been compromised.
Read 5 remaining paragraphs | Comments