UPnP flaw exposes millions of network devices to attacks over the Internet
Enlarge (credit: US GAO / Flickr)
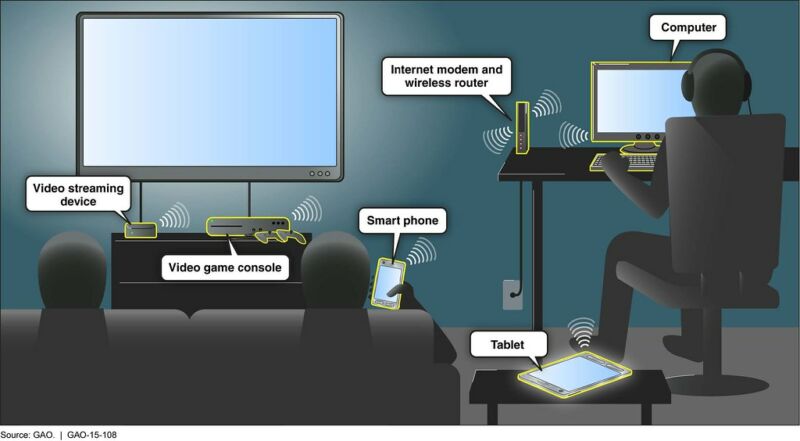
Millions of routers, printers, and other devices can be remotely commandeered by a new attack that exploits a security flaw in the Universal Plug and Play network protocol, a researcher said.
CallStranger, as the exploit has been named, is most useful for forcing large numbers of devices to participate in distributed denial of service-or DDoS-attacks that overwhelm third-party targets with junk traffic. CallStranger can also be used to exfiltrate data inside networks even when they're protected by data loss prevention tools that are designed to prevent such attacks. The exploit also allows attackers to scan internal ports that would otherwise be invisible because they're not exposed to the Internet.
Billions of routers and other so-called Internet-of-things devices are susceptible to CallStranger, Yunus Cadrc, a Turkish researcher who discovered the vulnerability and wrote the proof-of-concept attack code that exploits it, wrote over the weekend. For the exploit to actually work, however, a vulnerable device must have UPnP, as the protocol is known, exposed on the Internet. That constraint means only a fraction of vulnerable devices are actually exploitable.
Read 10 remaining paragraphs | Comments