Telegram messages are a focus in newly uncovered hack campaign from Iran
Enlarge / Rampant Kitty has been targeting Telegram like a feline to twine. (credit: Check Point)
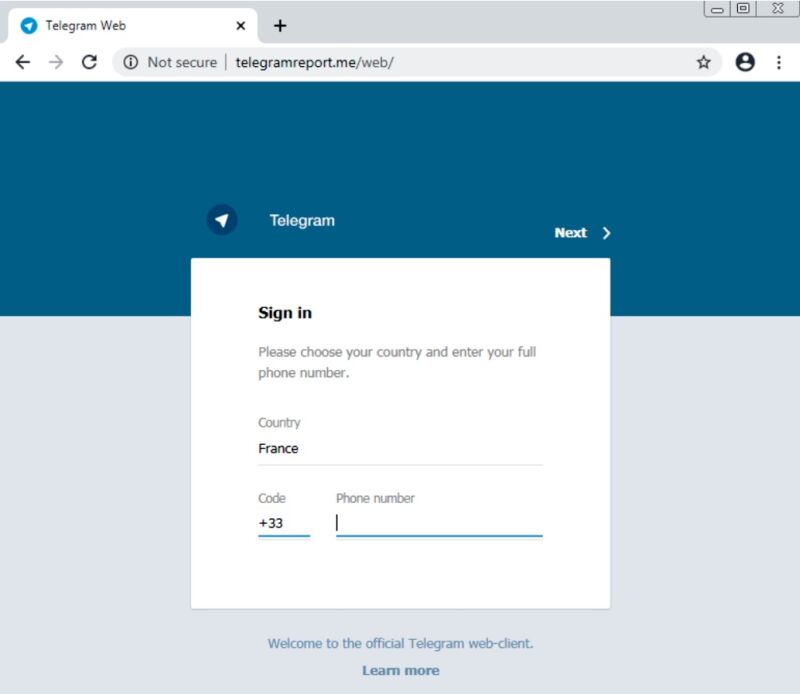
Researchers said they have uncovered an ongoing surveillance campaign that for years has been stealing a wide range of data on Windows and Android devices used by Iranian expatriates and dissidents.
The campaign, which security firm Check Point has named Rampant Kitten, comprises two main components, one for Windows and the other for Android. Rampant Kitten's objective is to steal Telegram messages, passwords, and two-factor authentication codes sent by SMS and then also take screenshots and record sounds within earshot of an infected phone, the researchers said in a post published on Friday.
The Windows infostealer is installed through a Microsoft Office document with a title that roughly translates to The Regime Fears the Spread of the Revolutionary Cannons.docx." Once opened, it urges readers to enable macros. If a user complies, a malicious macro downloads and installs the malware. The Android infostealer is installed through an app that masquerades as a service to help Persian-language speakers in Sweden get their driver's license.
Read 8 remaining paragraphs | Comments