In epic hack, Signal developer turns the tables on forensics firm Cellebrite
Enlarge (credit: Moxie Marlinspike/Signal)
For years, Israeli digital forensics firm Cellebrite has helped governments and police around the world break into confiscated mobile phones, mostly by exploiting vulnerabilities that went overlooked by device manufacturers. Now, Moxie Marlinspike-creator of the Signal messaging app-has turned the tables on Cellebrite.
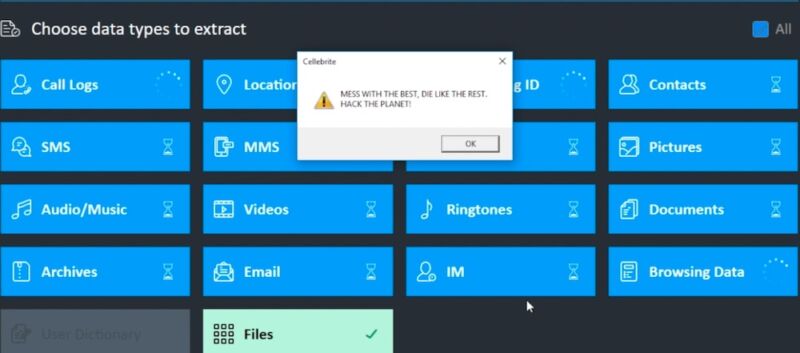
On Wednesday, Marlinspike published a post that reported vulnerabilities in Cellebrite software that allowed him to execute malicious code on the Windows computer used to analyze devices. The researcher and software engineer exploited the vulnerabilities by loading specially formatted files that can be embedded into any app installed on the device.
Virtually no limitsThere are virtually no limits on the code that can be executed," Marlinspike wrote.
Read 13 remaining paragraphs | Comments