Apple’s AirDrop leaks users’ PII, and there’s not much they can do about it
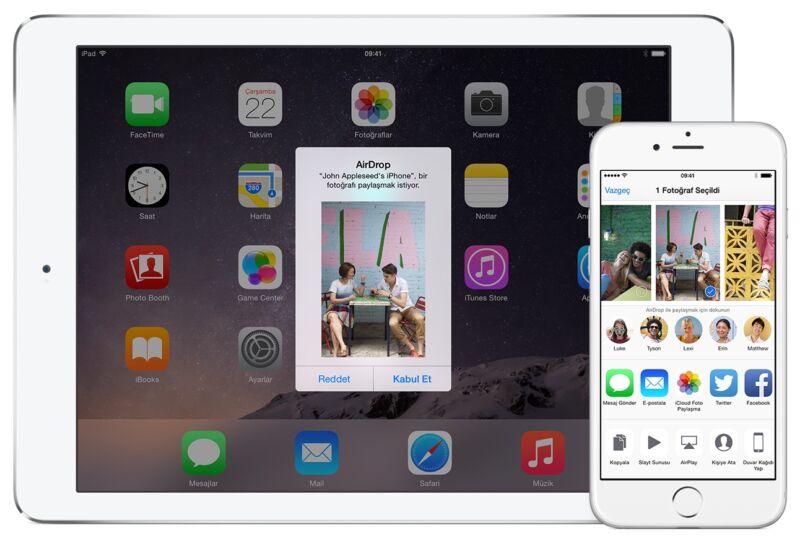
AirDrop, the feature that allows Mac and iPhone users to wirelessly transfer files between devices, is leaking user emails and phone numbers, and there's not much anyone can do to stop it other than to turn it off, researchers said.
AirDrop uses Wi-Fi and Bluetooth Low Energy to establish direct connections with nearby devices so they can beam pictures, documents, and other things from one iOS or macOS device to another. One mode allows only contacts to connect, a second allows anyone to connect, and the last allows no connections at all.
A matter of millisecondsTo determine if the device of a would-be sender should connect with other nearby devices, AirDrop broadcasts Bluetooth advertisements that contain a partial cryptographic hash of the sender's phone number and email address. If any of the truncated hashes matches any phone number or email address in the address book of the receiving device or the device is set to receive from everyone, the two devices will engage in a mutual authentication handshake over Wi-Fi. During the handshake, the devices exchange the full SHA-256 hashes of the owners' phone numbers and email addresses.
Read 13 remaining paragraphs | Comments