Security researcher successfully jailbreaks an Apple AirTag
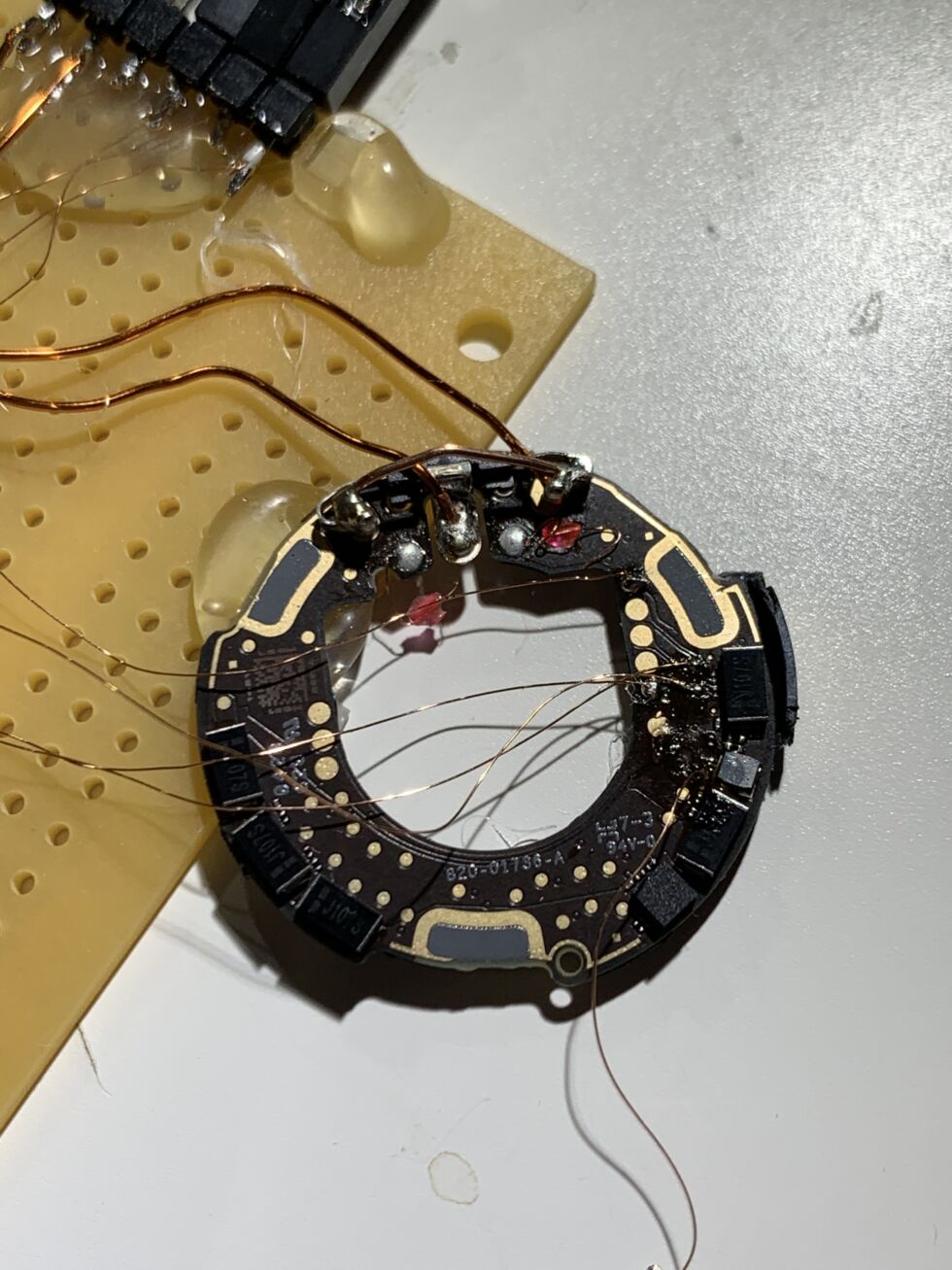
After permanently bricking two AirTags, stacksmashing succeeded in breaking into and reprogramming a third. [credit: stacksmashing ]
This weekend, German security researcher stacksmashing declared success at breaking into, dumping, and reflashing the microcontroller of Apple's new AirTag object-location product.
Breaking into the microcontroller essentially meant being able both to research how the devices function (by analyzing the dumped firmware) and to reprogram them to do unexpected things. Stacksmashing demonstrated this by reprogramming an AirTag to pass a non-Apple URL while in Lost Mode.
Lost Mode gets a little more lostWhen an AirTag is set to Lost Mode, tapping any NFC-enabled smartphone to the tag brings up a notification with a link to found.apple.com. The link allows whoever found the lost object to contact its owner, hopefully resulting in the lost object finding its way home.
Read 7 remaining paragraphs | Comments