Need to get root on a Windows box? Plug in a Razer gaming mouse

Enlarge (credit: Razer)
This weekend, security researcher jonhat disclosed a long-standing security bug in the Synapse software associated with Razer gaming mice. During software installation, the wizard produces a clickable link to the location where the software will be installed. Clicking that link opens a File Explorer window to the proposed location-but that File Explorer spawns with SYSTEM process ID, not with the user's.
Have mouse, will root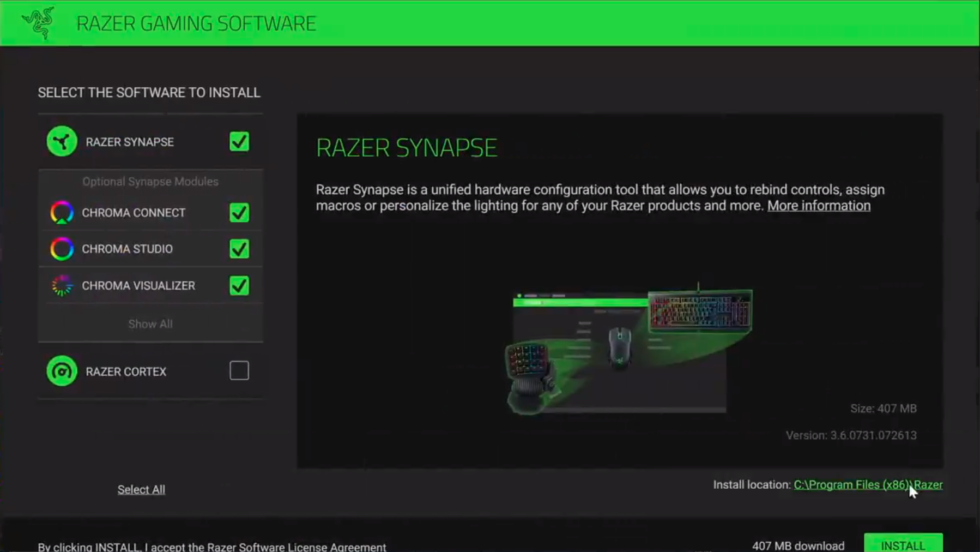
The "Install Location" at the lower right is a clickable link that opens a File Explorer window to browse for non-standard locations. [credit: jonhat ]
By itself, this vulnerability in Razer Synapse sounds like a minor issue-after all, in order to launch a software installer with SYSTEM privileges, a user would normally need to have Administrator privileges themselves. Unfortunately, Synapse is a part of the Windows Catalog-which means that an unprivileged user can just plug in a Razer mouse, and Windows Update will cheerfully download and run the exploitable installer automatically.
Jonhat isn't the only-or even the first-researcher to discover and publicly disclose this bug. Lee Christensen publicly disclosed the same bug in July, and according to security researcher _MG_, who demonstrated it using an OMG cable to mimic the PCI Device ID of a Razer mouse and exploit the same vulnerability, researchers have been reporting it fruitlessly for more than a year.
Read 2 remaining paragraphs | Comments