Malvertisers target Mac users with steganographic code stashed in images
Enlarge / One of the malicious ads displayed in a campaign from VeryMal. (credit: Confiant)
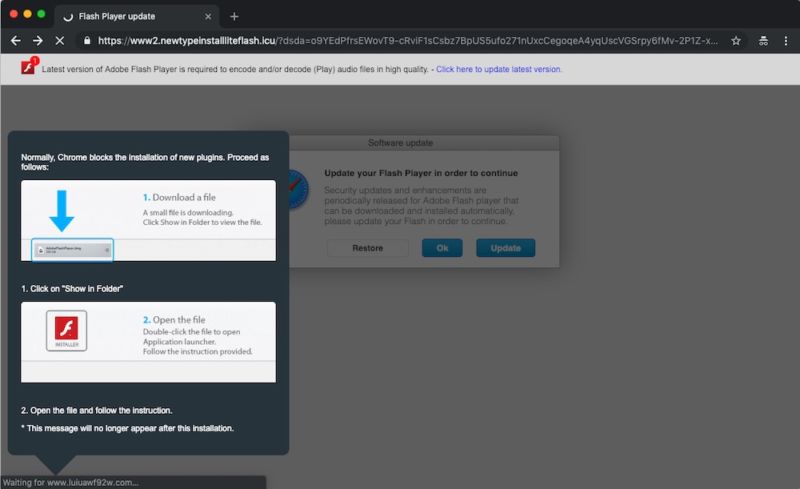
Researchers have uncovered a recent malicious advertisement campaign that's notable for its size, scope, and resourcefulness: a two-day blitz triggered as many as 5 million times per day that used highly camouflaged JavaScript stashed in images to install a trojan on visitors' Macs.
The ads were served by a group security firm Confiant has dubbed VeryMal, a name that comes from veryield-malyst.com, one of the ad-serving domains the group uses. A run that was active from January 11 to January 13 on about 25 of the top 100 publisher sites triggered the image as many as 5 million times a day. In an attempt to bypass increasingly effective measures available to detect malicious ads, the images used steganography-the ancient practice of hiding code, messages, or other data inside images or text-to deliver its malicious payload to Mac-using visitors.
In a blog post published Wednesday, Confiant researcher Eliya Stein wrote:
Read 6 remaining paragraphs | Comments