Hackers actively exploit WordPress plugin flaw to send visitors to bad sites
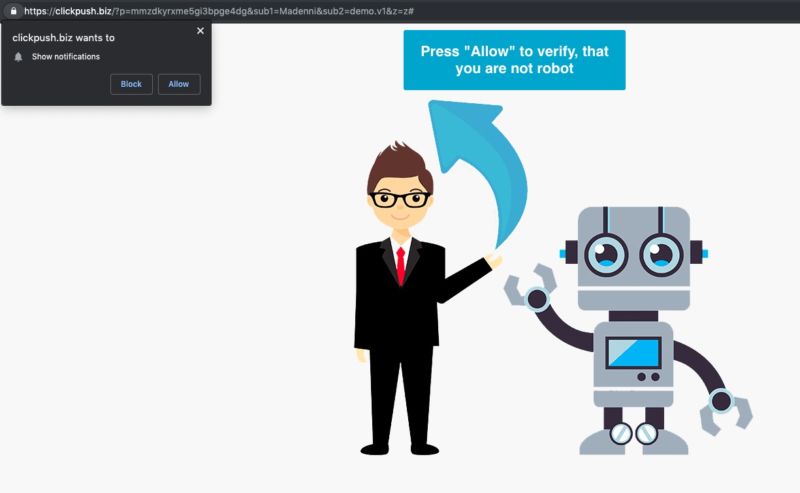
Enlarge / A redirection from a site still running a vulnerable version of the plugin.
Hackers have been actively exploiting a recently patched vulnerability in some websites that causes the sites to redirect to malicious sites or display misleading popups, security researchers warned on Wednesday.
The vulnerability was fixed two weeks ago in WP Live Chat Support, a plugin for the WordPress content management system that has 50,000 active installations. The persistent cross-site scripting vulnerability allows attackers to inject malicious JavaScript into sites that use the plugin, which provides an interface for visitors to have live chats with site representatives.
Researchers from security firm Zscaler's ThreatLabZ say attackers are exploiting the vulnerability to cause sites using unpatched versions of WP Live Chat Support to redirect to malicious sites or to display unwanted popups. While the attacks aren't widespread, there have been enough of them to raise concern.
Read 3 remaining paragraphs | Comments