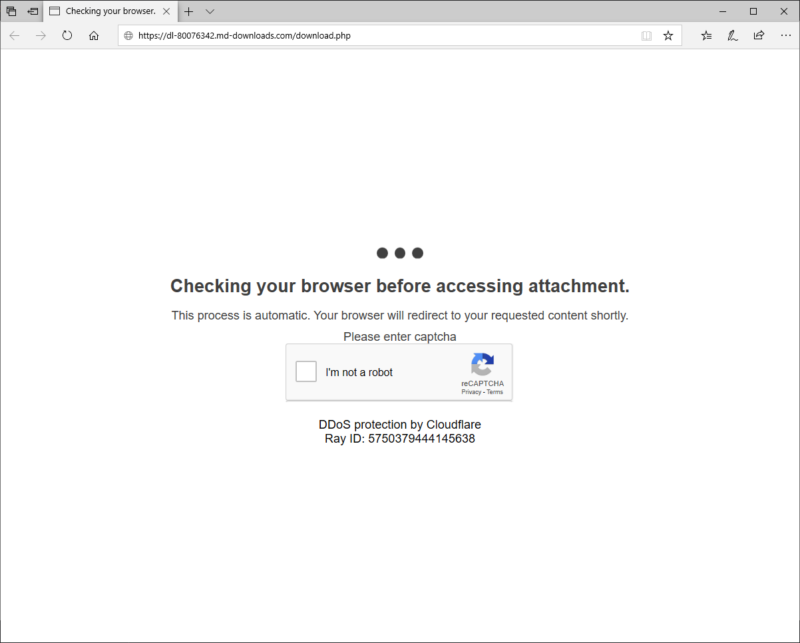
To evade detection, hackers are requiring targets to complete CAPTCHAs
Enlarge (credit: Microsoft Security Intelligence)
CAPTCHAs, those puzzles with muffled sounds or blurred or squiggly letters that websites use to filter out bots (often unsuccessfully), have been annoying end users for more than a decade. Now, the challenge-and-response tests are likely to vex targets in malware attacks.
Microsoft recently spotted an attack group distributing a malicious Excel document on a site requiring users to complete a CAPTCHA, most likely in an attempt to thwart automated detection by good guys. The Excel file contains macros that, when enabled, install GraceWire, a trojan that steals sensitive information such as passwords. The attacks are the work of a group Microsoft calls Chimborazo, which company researchers have been tracking since at least January.
Previously, Microsoft observed Chimborazo distributing the Excel file in attachments included in phishing messages and later spreading through embedded Web links. In recent weeks, the group has begun sending phishing emails that change things up again. In some cases, the phishes include links that lead to redirector sites (usually legitimate sites that have been compromised). In other cases, the emails have an HTML attachment that contains a malicious iframe tag.
Read 9 remaining paragraphs | Comments