With help from Google, impersonated Brave.com website pushes malware

Enlarge (credit: Getty Images)
Scammers have been caught using a clever sleight of hand to impersonate the website for the Brave browser and using it in Google ads to push malware that takes control of browsers and steals sensitive data.
The attack worked by registering the domain xn--brav-yva[.]com, an encoded string that uses what's known as punycode to represent brav[.]com, a name that when displayed in browser address bars is confusingly similar to brave.com, where people download the Brave browser. Brav[.]com (note the accent over the letter E) was almost a perfect replica of brave.com, with one crucial exception: the Download Brave" button grabbed a file that installed malware known both as ArechClient and SectopRat.
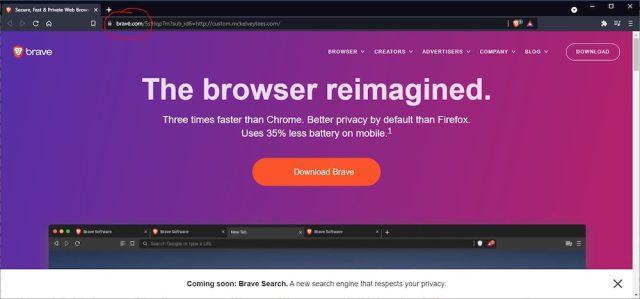
(credit: Jonathan Sampson)
From Google to malware in 10 seconds flatTo drive traffic to the fake site, the scammers bought ads on Google that were displayed when people searched for things involving browsers. The ads looked benign enough. As the images below show, the domain shown for one ad was mckelveytees.com, a site that sells apparel for professionals.
Read 10 remaining paragraphs | Comments