Gone in 130 seconds: New Tesla hack gives thieves their own personal key

Enlarge (credit: Getty Images)
Last year, Tesla issued an update that made its vehicles easier to start after being unlocked with their NFC key cards. Now, a researcher has shown how the feature can be exploited to steal cars.
For years, drivers who used their Tesla NFC key card to unlock their cars had to place the card on the center console to begin driving. Following the update, which was reported here last August, drivers could operate their cars immediately after unlocking them with the card. The NFC card is one of three means for unlocking a Tesla; a key fob and a phone app are the other two.
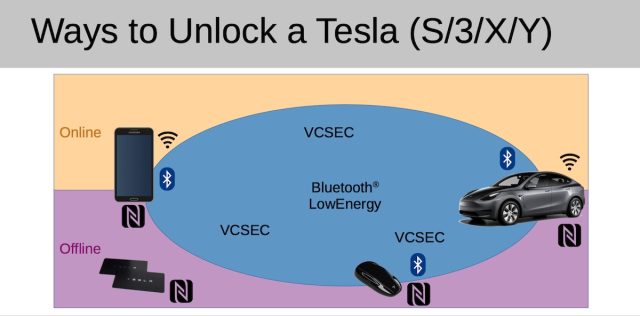
An image from Herfurt's recent presentation at the REcon conference in Montreal. (credit: https://trifinite.org/Downloads/20220604_tempa_presentation_recon22_public.pdf)
Enrolling your own keyMartin Herfurt, a security researcher in Austria, quickly noticed something odd about the new feature: Not only did it allow the car to automatically start within 130 seconds of being unlocked with the NFC card, but it also put the car in a state to accept entirely new keys-with no authentication required and zero indication given by the in-car display.