Google-hosted malvertising leads to fake Keepass site that looks genuine

Enlarge (credit: Miragec/Getty Images)
Google has been caught hosting a malicious ad so convincing that there's a decent chance it has managed to trick some of the more security-savvy users who encountered it.
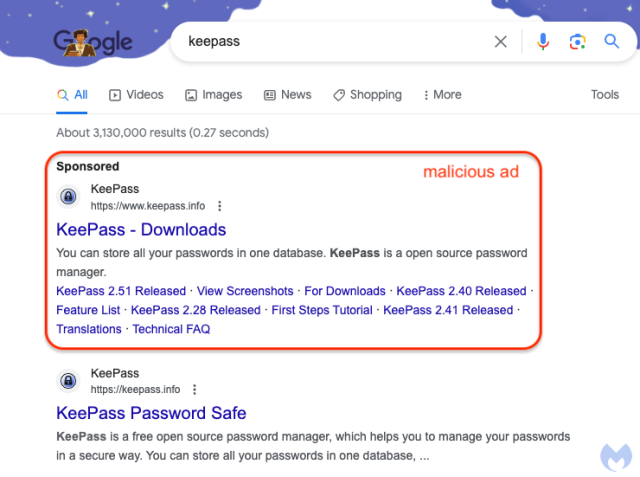
Screenshot of the malicious ad hosted on Google. (credit: Malwarebytes)
Looking at the ad, which masquerades as a pitch for the open source password manager Keepass, there's no way to know that it's fake. It's on Google, after all, which claims to vet the ads it carries. Making the ruse all the more convincing, clicking on it leads to eepass[.]info, which, when viewed in an address bar, appears to be the genuine Keepass site.
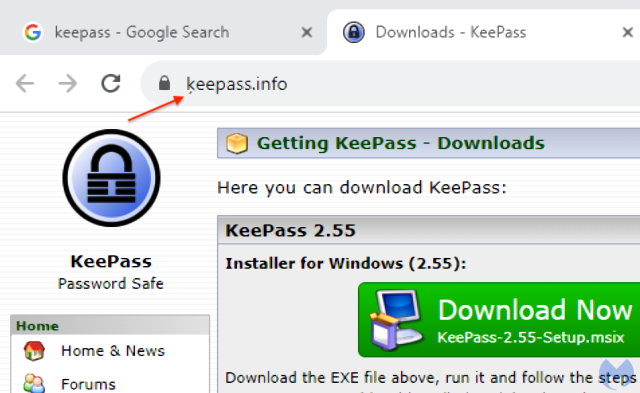
Screenshot showing keepass.info in the URL and Keepass logo. (credit: Malwarebytes)
A closer look at the link, however, shows that the site is not the genuine one. In fact, eepass[.]info-at least when it appears in the address bar-is just an encoded way of denoting xn--eepass-vbb[.]info, which, it turns out, is pushing a malware family tracked as FakeBat. Combining the ad on Google with a website with an almost identical URL creates a near-perfect storm of deception.